All Blogs
SaaS Pentesting Explained: Methods, Benefits, and Best Practices

Blog Overview: SaaS applications power today’s businesses but also face unique security challenges. This blog explores SaaS penetration testing, its purpose, scope, methodologies, and benefits. Learn how pentesting strengthens cloud-native environments, ensures compliance, and protects sensitive data across web apps, APIs, and multi-tenant infrastructures.
In the past decade, Software as a Service (SaaS) has shifted from being an optional delivery model to becoming foundational for many enterprises, startups, and even governments. As of 2024-25, over 70% of enterprise software usage is via cloud-delivered services, and a majority of organizations now store sensitive data in third-party SaaS platforms.
But this convenience comes with increased risk. According to recent research:
- In the past year, 80% of companies reported experiencing at least one cloud security breach.
- Around 96% of organizations encountered challenges with their cloud security strategies.
- 28% of organizations experienced cloud- or SaaS-related data breach in the past year, with 36% of those suffering multiple breaches.
- Worse, breaches in SaaS environments are getting faster: threat actors are known to compromise core systems in as little as 9 minutes in some documented cases.
- Almost 99% of organizations were found to have sensitive data exposed in SaaS or cloud environments in a study of nearly 10 billion files across environments and platforms.
Well, the above statistics make one thing clear: pentesting is not just “nice to have”, but it’s essential, especially for SaaS providers, SaaS consumers who rely on third-party services, and organizations adopting hybrid or multi-cloud models.
This SaaS penetration testing guide aims to provide a research-backed roadmap for conducting comprehensive pentesting in SaaS environments. Whether you’re a developer, security engineer, or leader wanting to understand what kind of risks are real, how to test them, and how to build sustainable practices, this is for you.
Start your journey toward stronger SaaS security. Create your account in minutes and begin testing today. Get Started Free
On This Page
- What is SaaS Penetration Testing?
- Key Characteristics of SaaS Pentesting
- Benefits of SaaS Pentesting
- Why SaaS App Needs Penetration Testing Before Scaling
- Types of SaaS Penetration Testing
- What to Expect from SaaS Penetration Testing?
- SaaS Pentesting Methodologies and Standards
- What Should You Look for in a SaaS Penetration Testing Tool?
- Five Stages in a SaaS Penetration Testing Tool
- SaaS Pentesting with ZeroThreat
- Final Thoughts
What is SaaS Penetration Testing?
SaaS penetration testing is the process of evaluating the security of Software-as-a-Service applications and their supporting infrastructure by simulating real-world attacks. Unlike generic web app pentesting, SaaS pentesting goes deeper into the unique risks that arise from cloud-native, subscription-based software models.
The primary goal of SaaS security testing is not only to find vulnerabilities but also to assess how they could be exploited in a multi-tenant, API-driven environment where customer trust and regulatory compliance are critical.
So, when you implement SaaS pentesting, one answer you must be aware of: Can an attacker compromise the confidentiality, integrity, or availability of customer data and services in a shared, cloud-hosted application?
Key Characteristics of SaaS Pentesting
Let’s understand some of the common key characteristics of SaaS security testing.
Multi-Tenancy Awareness
The foundation of most SaaS platforms is multi-tenancy. This allows multiple organizations (tenants) to use the same application instance while relying on strict separation of data and resources.
In penetration testing, this is a critical area of focus. Testers simulate attempts to bypass authorization boundaries, exploit insecure direct object references (IDOR), or manipulate tenant identifiers in API requests. Even subtle flaws in logic could result in catastrophic cross-tenant data leakage. Therefore, SaaS pentesting must validate that isolation is consistently enforced across every layer of the application.
API-Driven Services and Integrations
Another defining trait of SaaS applications is their dependency on APIs. In SaaS pentesting, APIs are scrutinized for broken authentication, broken authorization, weak input validation, and missing rate limits. A vulnerable endpoint could allow attackers to harvest sensitive information or manipulate workflows.
Testers often use API pentesting tools and other techniques like fuzzing to detect how APIs handle unexpected inputs, while also assessing whether business logic flaws could be abused.
Identity and Access Management (IAM)
Identity forms the front door of SaaS platforms. Users access services via login portals, single sign-on (SSO) integrations, or third-party identity providers like Google or Azure AD.
SaaS pentesting evaluates how well authentication and authorization are enforced. This includes testing whether role-based access controls (RBAC) are properly applied, whether MFA can be bypassed, and whether session tokens are securely generated and invalidated.
Compliance and Regulatory Obligations
For SaaS providers, security is not just a technical concern but also a regulatory requirement. Industries such as finance, healthcare, and government impose strict compliance standards. Frameworks like SOC 2, GDPR, HIPAA, and India’s Digital Personal Data Protection (DPDP) Act require organizations to prove that data is handled securely
Pentesting plays a key role in demonstrating compliance. By identifying gaps in encryption, logging, access control, or incident response, it ensures that the SaaS provider is not only meeting the bare minimum for audits but is also reducing real-world risks.
Benefits of SaaS Pentesting
Implementing SaaS security best practices is essential to make your business more secure and reliable. With sensitive customer data at stake and strict regulated industry security standards to follow, proactive testing ensures your environment stays safe and resilient.
- Expose Hidden Risks: SaaS web app pentesting uncovers weaknesses in applications, infrastructure, and integrations before attackers can exploit them.
- Strengthen Security Roadmaps: Test insights guide smarter strategies to harden defenses and reduce long-term risk.
- Stay Compliant: Meet standards like SOC 2, ISO 27001, HIPAA, and GDPR with confidence.
- Earn Customer Trust: Demonstrating robust security builds credibility, boosts customer confidence, and strengthens brand reputation.
Pentesting for Saas applications helps businesses gain the assurance needed to grow safely and win customer loyalty.
Why Every SaaS App Needs Penetration Testing Before Scaling
Scaling a Saas app means onboarding more customers, integrating with third-party services, and handling larger volumes of sensitive data. While growth is exciting, it also magnifies risk. A vulnerability that affects ten users in the early stage could compromise thousands once the platform scales.
Penetration testing before scaling acts as a security checkpoint, ensuring the app’s foundation is strong enough to handle increased demand without exposing customer data. By simulating real-world attacks, pentesting validates tenant isolation, API security, and access controls that become more critical as usage expands.
Another reason is compliance readiness. Larger customers often demand evidence of SOC 2, HIPAA, or GDPR compliance. Without pentesting, SaaS providers risk losing enterprise deals due to weak security assurances.
Most importantly, early pentesting helps avoid costly retroactive fixes. Identifying and remediating vulnerabilities during the growth stage is cheaper, faster, and less disruptive than patching them after scaling. In fact, it’s a key driver of sustainable SaaS growth.
Types of SaaS Penetration Testing
SaaS penetration testing is not a single activity but rather a collection of focused assessments that provide a holistic view of security posture.
Since SaaS applications are built on layered architectures, which involve web frontends, APIs, cloud services, identity systems, and third-party integrations, pentesting must address each of these layers.
Below are the major types of SaaS pentesting and how they contribute to securing the platform.
Web Application Pentesting for SaaS Frontends
Traditional web vulnerabilities like SQL injection, XSS, and CSRF still apply, but in SaaS, the risk is amplified because a single flaw can impact multiple tenants simultaneously.
Here, pentesters assess input validation, session management, and business logic to ensure that the frontend cannot be used as an entry point.
API Pentesting
APIs are an important entity of SaaS platforms, powering integrations with CRMs, payment processors, analytics tools, and more. Unfortunately, they also account for some of the most severe SaaS breaches.
API pentesting focuses on identifying issues such as:
- Broken authentication or authorization: Can one user access another tenant’s data?
- Excessive data exposure: Does an endpoint return more information than necessary?
- Rate limiting gaps: Can attackers brute-force tokens or overwhelm services with requests?
- Logic flaws: Could workflows like refunds or license activation be abused?
Testers typically combine automated API pentesting tool with manual exploitation to validate these risks. This ensures both technical flaws and subtle business logic errors are discovered.
Cloud Configuration Security Testing
Using AWS S3 bucket for storage, Kubernetes clusters for orchestration, and services like Azure Functions or Google Pub/Sub for backend tasks, SaaS platforms are deeply tied to cloud infrastructure. And here, misconfigurations are the real culprit behind most breaches.
So, cloud pentesting is used to simulate attacks such as accessing public storage buckets, exploiting overly permissive IAM policies, or hijacking misconfigured DNS records. This ensures whether encryption is properly enforced for data at rest and in transit.
Continuous Pentesting (Pentest-as-a-Service)
Traditional pentests are point-in-time exercises. But SaaS applications evolve rapidly, often deploying code multiple times a day. A vulnerability that didn’t exist yesterday could be introduced today.
This is where continuous pentesting or Pentest-as-a-Service (PTaaS) comes in. Instead of running tests once or twice a year, organizations integrate pentesting into their CI/CD pipelines. Automated security testing tools are combined with regular human-led assessments to provide near real-time feedback.
Transparent, flexible pricing designed for startups to enterprises. See which plan fits your security needs. View Pricing
What to Expect from SaaS Penetration Testing?
Setting the right expectations before a SaaS pentest begins is essential. A mature pentesting engagement gives you clarity on what will be tested, what outcomes to expect, and where its boundaries lie. SaaS pentesting is designed to simulate real-world threats within an agreed scope, but it is not a silver bullet for every security challenge.
What SaaS Pentesting Can Deliver:
1. Comprehensive Vulnerability Discovery
- Identify flaws across web applications, APIs, cloud configurations, IAM roles, and third-party integrations.
- Simulate realistic attack paths such as cross-tenant data access or privilege escalation.
2. Assessment of Security Posture
- Provide a clear snapshot of how resilient your SaaS environment is against current threats.
- Highlight gaps in configurations, access controls, and software dependencies.
3. Actionable Remediation Guidance
- Every vulnerability is reported with technical details, business impact, and step-by-step remediation advice.
- This equips your security and development teams to prioritize and fix issues effectively.
4. Compliance Support
- Generate evidence needed for regulatory frameworks like SOC 2, GDPR, HIPAA, or DPDP (India).
- Demonstrate proactive security measures to auditors and enterprise customers.
What SaaS Pentesting Does Not Do
1. Fix Vulnerabilities Directly
- Pentesters identify and document flaws but don’t patch them. Remediation is carried out by your internal development or DevOps teams.
2. Replace Security Awareness
- Pentesting cannot address organizational issues like poor password hygiene, phishing susceptibility, or insider negligence. It can highlight risks, but awareness and training remain separate initiatives.
3. Test Out-of-Scope Services
- Unless explicitly agreed, external SaaS applications, unmanaged APIs, or third-party vendor platforms are not tested. The focus remains on your defined SaaS environment.
4. Perform Destructive Testing
- Activities such as Distributed Denial of Service (DDoS) or stress-testing are excluded. Cloud providers (AWS, Azure, GCP) prohibit such tests without special authorization, and they risk disrupting production systems.
SaaS Pentesting Methodologies and Standards

SaaS pentesting methodologies provide structure, consistency, and industry-recognized credibility to the engagement. Instead of relying on ad-hoc tests, professional pentesters adapt established standards to SaaS environments.
OWASP Testing Framework
The OWASP Web Security Testing Guide (WSTG) and OWASP API Security Top 10 are highly relevant to SaaS.
- They provide test cases for injection flaws, authentication weaknesses, misconfigurations, and insecure APIs.
- In SaaS pentesting, OWASP principles are extended to validate multi-tenancy boundaries and SaaS-specific business logic.
PTES (Penetration Testing Execution Standard)
PTES defines the phases of a professional pentest: pre-engagement, intelligence gathering, threat modeling, exploitation, and reporting.
- For SaaS, PTES helps standardize engagements across multiple components (web, API, cloud).
- It ensures that findings are reproducible and traceable, which is critical for audit readiness.
NIST Guidelines
The NIST SP 800-115 technical guide for security testing provides another benchmark.
- It emphasizes risk-based testing, meaning pentesters align depth of testing with business impact.
- In SaaS, this approach ensures focus on high-value assets like customer data, IAM, and API gateways.
SaaS-Specific Adaptations
Generic frameworks are not enough; SaaS requires contextual adaptation. For example:
- Multi-tenant test cases: attempting data leakage between tenants.
- Continuous deployment workflows: testing CI/CD pipelines and staging environments.
- Cloud service validation: reviewing permissions, storage policies, and encryption defaults in AWS/Azure/GCP.
Human-Led + Automated Testing
Automation is valuable for coverage, but SaaS pentesting must include manual exploration to uncover business logic flaws that scanners miss.
- Automated tools: for scanning APIs, dependencies, and misconfigurations.
- Human expertise: for chaining vulnerabilities, exploiting workflows, and testing unique SaaS logic.
Key takeaway: Methodologies provide the backbone of SaaS pentesting, but the real value lies in adapting these frameworks to the unique challenges of SaaS architectures.
What Should You Look for in a SaaS Penetration Testing Tool?
A mature and prominent SaaS security testing tool should go beyond simple scanning. It should provide visibility, context, and actionable insights tailored to cloud-native applications.
Key Capabilities to Expect in a SaaS Pentesting Tool
1. Comprehensive Coverage
- Ability to test web applications, APIs, and cloud configurations.
- Support for SaaS-specific scenarios like multi-tenancy validation, IAM testing, and business logic flaws.
2. Ease of Integration
- CI/CD pipeline support for automated security testing during development.
- Compatibility with developer workflows via GitHub, GitLab, or Jira integrations.
3. Clear Reporting and Management
- Centralized dashboards for tracking vulnerabilities.
- Reports tailored for both technical teams (detailed findings) and executives (risk summaries).
4. Actionable Remediation Guidance
- Contextual fixes aligned with the SaaS environment.
- Prioritization based on exploitability and business impact, not just raw vulnerability count.
5. Retesting and Validation Support
- Ability to verify fixes through automated re-scans or on-demand retests.
- Continuous validation rather than one-time testing.
6. Scalability and Flexibility
- Support for multi-cloud environments (AWS, Azure, GCP).
- Ability to scale testing as the SaaS application grows in complexity and customer base.
7. Security and Data Privacy
- Secure handling of test data, with clear policies on data storage and retention.
- Compliance with standards like SOC 2, GDPR, or HIPAA where required.
Ready to test your SaaS against real-world threats? Book your pentest with ZeroThreat today. Request a Pentest
Five Stages in a SaaS Penetration Testing Tool
SaaS penetration testing tools are designed to automate and streamline the security testing process, providing faster visibility into risks while complementing manual reviews. A mature tool follows a structured workflow that mirrors a professional pentesting engagement but is optimized for scale and speed.
1. Setup and Scoping
The tool begins by mapping out the environment to be tested. This may include:
- Web applications, APIs, and microservices.
- Cloud configurations and storage buckets.
- Identity and access roles.
Users can define testing scope, exclusions, and environments (staging vs production) to ensure safe and targeted assessments.
2. Automated Vulnerability Discovery
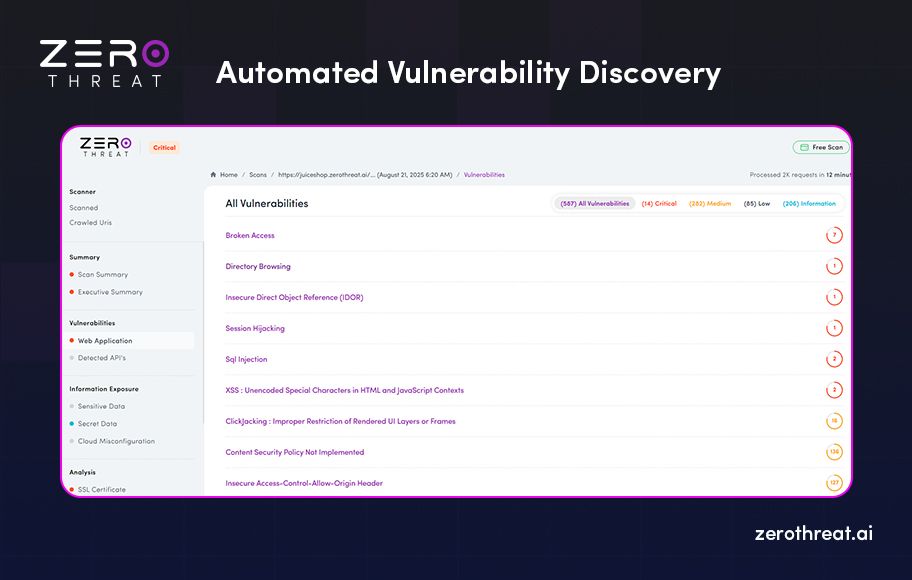
The core engine scans the SaaS environment for known vulnerabilities, misconfigurations, and weak security controls.
- Uses signatures, heuristics, and machine learning models to detect flaws.
- Covers OWASP Top 10, API Security Top 10, and cloud-specific risks.
- Provides a prioritized list of issues for review.
This step replaces the traditional “vulnerability assessment” phase but runs continuously to keep pace with SaaS development cycles.
3. Exploitation Simulation
A mature tool doesn’t stop at identifying vulnerabilities. In fact, it simulates exploitation safely to validate real-world impact.
- Confirms if a vulnerability is exploitable, reducing false positives.
- Demonstrates attack paths such as privilege escalation, data leakage, or cross-tenant access.
- Runs in controlled environments to avoid service disruption.
This ensures findings are actionable and relevant rather than just noise.
4. Reporting and Collaboration
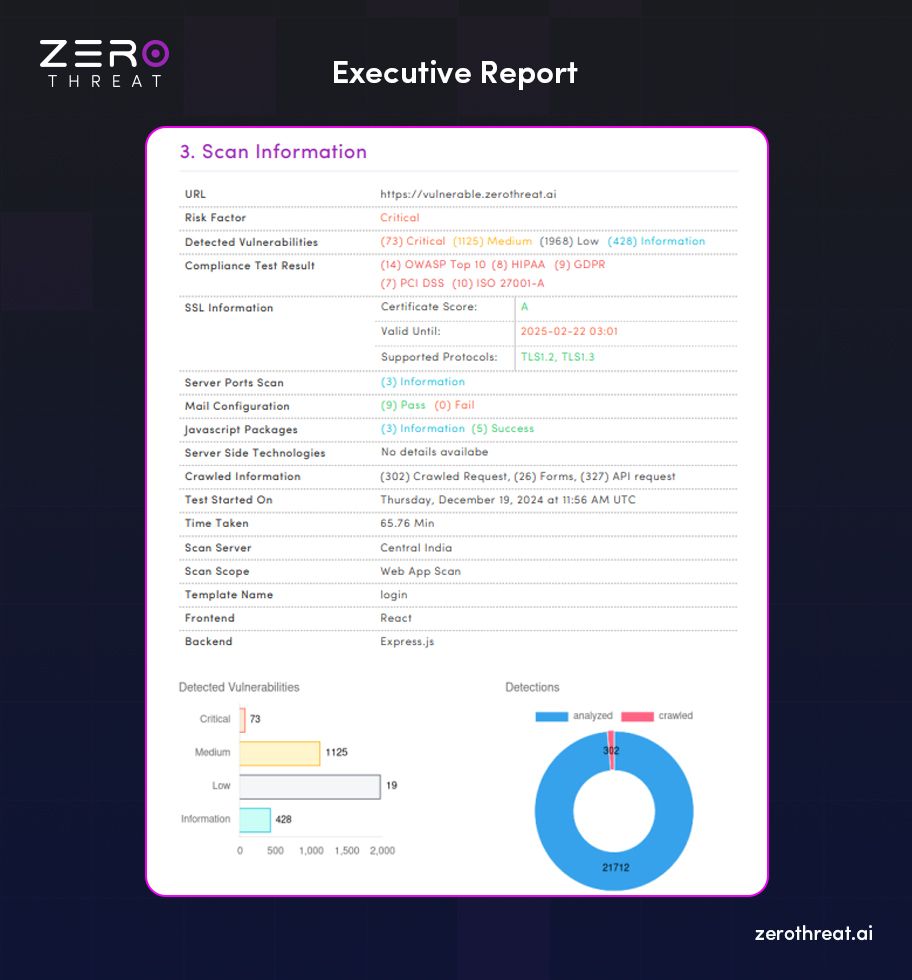

The tool generates structured reports for different stakeholders:
- Developers: Technical details, PoCs, and reproduction steps.
- Executives: Risk scores, compliance mapping, and business impact.
- Security teams: Central dashboards to manage vulnerabilities, assign fixes, and track SLA timelines.
Many modern tools also integrate directly with Jira, Slack, or GitHub to simplify collaboration and reduce remediation cycles.
5. Retesting and Continuous Assurance
After remediation, the pentesting tool verifies whether vulnerabilities have been successfully fixed.
- Supports on-demand retesting or automated re-checks.
- Provides closure evidence for compliance and audit purposes.
- Offers continuous monitoring to detect newly introduced risks in subsequent deployments.
This final stage transforms pentesting from a one-time event into an ongoing security assurance process.
SaaS Pentesting with ZeroThreat
ZeroThreat is a next-gen SaaS penetration testing platform, combining the scale of automation with the real-world attack simulation. Unlike traditional service-driven pentests that are conducted once or twice a year, ZeroThreat enables continuous, tool-powered testing designed for fast-moving SaaS environments.
Key Capabilities of ZeroThreat
- Platform: Cloud-native SaaS pentesting platform, designed for web apps, APIs, and multi-tenant environments.
- Pentest Coverage: Continuous automated scans across 40,000+ security checks for business logic and complex scenarios.
- Accuracy: Vetted findings with zero false positives, so teams don’t waste time chasing noise.
- Compliance Readiness: Supports industry frameworks such as OWASP, PCI-DSS, HIPAA, and ISO27001.
- Workflow Integration: Connect seamlessly with Jira, Slack, GitHub, GitLab, Jenkins, and CI/CD pipelines for developer-first adoption.
- Pricing: Transparent pricing model starting at $25/scan, with enterprise and unlimited plans available.
Why ZeroThreat?
ZeroThreat provides a scalable, always-on pentesting tool that integrates directly into your SaaS development lifecycle. This ensures that vulnerabilities are discovered early, fixed faster, and continuously validated, aligning with the pace of SaaS innovation.
Welcome back! Access your dashboard and manage your pentests seamlessly. Sign In Securely
Conclusion
SaaS penetration testing is no longer optional. It’s a critical layer of defense for cloud-native applications. By addressing risks across APIs, IAM, multi-tenancy, and cloud infrastructure, organizations can safeguard customer data, maintain compliance, and build lasting trust.
Frequently Asked Questions
What is SaaS penetration testing and why is it important?
SaaS penetration testing simulates real-world attacks on cloud-based applications to uncover vulnerabilities. It’s important because SaaS environments handle sensitive, multi-tenant data, making proactive testing essential for security, compliance, and maintaining customer trust.
Which components are covered in SaaS pentesting (web, APIs, cloud, etc.)?
Does SaaS pentesting help meet regulatory requirements like SOC 2 or HIPAA?
What can’t SaaS penetration testing do?
How often should SaaS penetration testing be conducted?
What’s the difference between automated and manual SaaS testing?
Are third-party integrations part of a SaaS pentest?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


