All Blogs
Navigating ISO 27001 Compliance: Your Roadmap to Data Security

Quick Summary: For modern customers and partners, standards are a hallmark of trust. So, organizations that align with such standards are trusted more. ISO 27001 is one such important standard that your customers and partners wish before doing any business with you. But there are a lot of things to understand and work on. Worry not! This blog helps you with the necessary information that makes your compliance easy. Read on to get the details!
Organizations, irrespective of their size, get different types of data from their customers. They process, store, and transmit this data but hardly use stringent measures to protect it. Internal safeguards often have inadequacies that attackers exploit to access sensitive data.
Therefore, organizations that are really concerned about their customers’ data adopt a standards-compliant approach. ISO 27001 is one of those important cyber security standards that they should follow to achieve compliance and security.
ISO 27001 provides a robust security framework to build a strong shield against cyber threats. It helps your organization improve its security practices and approaches, increasing the confidence of your customers in your processes.
Keep reading to learn more about ISO 27001, its importance, and how you can achieve compliance with this standard.
Avoid Risk and Penalties that Non-Compliance Can Bring You with ZeroThreat Get Started for Free
On This Page
- Understanding ISO 27001
- Benefits of Aligning with ISO 27001
- How to Achieve ISO 27001 Compliance?
- Achieve Compliance with ZeroThreat
What is ISO 27001?
ISO 27001 is a globally recognized standard for information security created by ISO (International Organization for Standardization) and IEC (International Electrotechnical Commission) collaboratively. This standard serves as a guiding force for organizations to implement, monitor, manage, and review information security.
It provides a structured and risk-based approach to manage and protect information systems regardless of an organization’s size and industry type. The ISO 27001 standard defines a set of requirements that enable organizations to implement and manage an information security management system (ISMS).
The ISMS is a security framework that offers a set of policies, controls, and procedures to protect the integrity, confidentiality, and availability of information systems from cyber threats. In a nutshell, the ISO 27001 standards provide crucial policies and procedures that help protect your organization's sensitive data and other information assets.
ISO 27001 compliance means that your organization aligns with the policies and principles defined by the standard. Your organization achieves ISO 27001 certification when it complies with the standard that demonstrates your commitment to protecting data, which builds confidence among stakeholders.
Advantages of ISO 27001 Compliance for Your Organization
Although compliance with ISO 27001 is not mandatory, as in the case of GDPR, it is a powerful tool for organizations to build secure ISMS. However, it is a flexible framework that can be applied and adapted to different organizations’ contexts. There are many advantages to complying with this standard, as mentioned below.
It provides the practices and policies that help organizations improve their security posture and reduce vulnerability to combat emerging cyber threats.
ISO 27001 certification shows your commitment to a secure IT environment, assuring your customers and prospects.
Compliance with this standard implies a stronger security posture that prevents breaches and reputational damage.
It ensures that intellectual properties, PIIs, financial statements, employee data, and other information that stakeholders have entrusted to your organization remain secure, undamaged, and confidential.
It provides a centrally managed security framework that protects information across the organization from a single control point.
It prepares processes and people to face technology-related risks and security threats.
Compliance with the standard ensures information security at every level, including digital, physical, and cloud.
It helps your organization to comply with legal requirements.
Your organization can improve security controls to avoid data breaches.
Reduce Your Attack Surface with Advanced DAST Scanning and Achieve Impeccable Security Conduct a Scan Now
How to Achieve ISO 27001 Compliance?
When it comes to achieving ISO 27001 compliance, certification is proof of compliance. However, it is not issued by ISO itself, and it is provided by an external certification body. Moreover, there are certain steps that you must follow to get your organization compliant with the standard by fulfilling necessary ISO 27001 requirements. Let’s check the steps below.
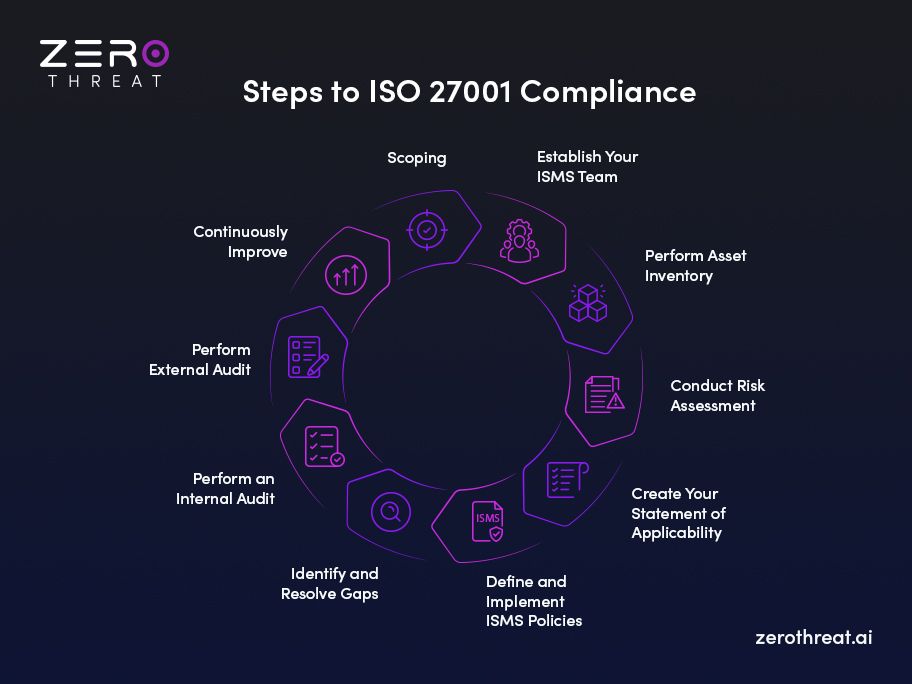
Scoping
Firstly, you need to create a scoping document. This document specifies everything that falls within the scope of ISMS like the type of sensitive data your organization handles, how your processes interact with that data, the areas of business covered by ISMS, and more. The scope can vary based on the size of an organization. It prepares a roadmap for implementing the standard.
Establish Your ISMS Team
After creating a scope for ISMS, the next step is to create a team to build the ISMS and assign them their respective roles. Your team may include only internal team members like engineers and compliance specialists, external contractors, or both.
Perform Asset Inventory
Every member of your team must know which assets to be covered by ISMS. So, you need to prepare an inventory of information assets that must be protected by ISMS. For this, you need to consider the different assets that process information and identify data flow within your organization.
Conduct Risk Assessment
Perform security audits to identify potential threats to your ISMS and document them. You can perform thorough automated vulnerability scanning to discover loopholes within your assets that can threaten the security of your data. Manage the record of the risks that you identified during the assessment, including their severity and likelihood. Also, create a risk response plan based on your identified threats.
Create Your Statement of Applicability
During the process of ISO 27001 compliance, you need to implement certain security practices and controls defined under section Annex A of the standard. These practices and controls apply as per the unique requirements or risks to organizations. Hence, you need to choose the controls that are relevant to your organization from the 114 controls mentioned there.
Define and Implement ISMS Policies
Once you have prepared your Statement of Applicability, the next step is to create appropriate policies for your ISMS to address all the controls defined in the statement. The policies should also define who will be maintaining the functions of ISMS. Besides, it should also provide information about the scope of these policies regarding vendors and contractors.
Identify and Resolve Gaps
Identify gaps in your policies that don’t align with ISO 27001. Address the gaps you have identified and implement a continuous cycle of monitoring to detect gaps. Analyze the gaps to identify the risks and root causes.
Perform an Internal Audit
Internal audits can be conducted by your internal team or an external auditor. It involves conducting penetration testing, analyzing non-conformities, document review, and recording the findings. The report of the internal audit contains essential information like the audit plan, test methodology, executive summary of the test, and recommendations that will help fix non-conformities.
Perform External Audit
In this step, an external auditor will evaluate your documents and provide feedback on moving to stage 2 audit. The stage 2 audit involves the evaluation of your ISMS to check its design, implementation, and functionality.
Continuously Improve
As the threat landscape is evolving constantly, ISO 27001 compliance becomes a continuous process. You must regularly conduct risk assessments to identify gaps and fix them to stay compliant with the standard.
Build a Strong Security Shield and Mitigate Cyber Risks with AI-Powered Vulnerability Assessment Uncover Risks
Meet ISO 27001 Compliance with ZeroThreat
ISO 2001 is one of the most important security standards that your organization must comply with to ensure customer trust and protect sensitive data. However, the dynamic nature of the cybersecurity landscape poses a challenge for your organization in keeping aligned with the standard.
Automation can be the best way to execute compliance as it helps you continuously assess your digital assets to find loopholes affecting compliance. ZeroThreat’s AI-powered DAST tool can help you meet ISO 27001 compliance requirements.
It offers advanced testing capabilities that help your organization precisely discover external and internal threats to minimize your attack surface. It helps your organization to avoid potential cyber security risks and protect sensitive data. It offers detailed AI-powered reports that help you accurately pinpoint the real causes to secure your IT environment to align with the ISO standard. Try it for free to check how it works.
Frequently Asked Questions
What are the requirements for ISO 27001?
To fully implement the standard, organizations must fulfill the requirements defined under clauses 5 to 10 mentioned below.
- Leadership
- Planning
- Support
- Operation
- Performance Evaluation
- Improvement
Besides, they should also implement controls defined under Annex A divided into Organizational, People, Physical, and Technological controls.
Who must comply with ISO 27001?
What does it mean to be ISO 27001 certified?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


