All Blogs

Quick Summary: Broken Object Level Authorization (BOLA) is one of the most critical API security risks, allowing attackers to access data by manipulating object IDs. This blog explains how BOLA works, the damage it can cause, and the different forms it takes. You’ll also learn why early detection matters and the key practices to prevent these attacks and strengthen your API security posture.
Today, APIs are among the most critical attack vectors for organizations. They are ubiquitous and widely used in applications. Since they are widespread in organizations, it makes them the foremost choice for attackers to plan a cyberattack.
Attackers look for API vulnerabilities like Broken Object Level Authorization for a successful attack. It is a type of vulnerability that occurs when an API allows access to objects but doesn’t validate a user’s access to those objects.
With this flaw, an unauthorized user can access other users’ data. Attackers can use it to modify or steal data. It is important to identify and resolve such types of vulnerability to ensure a robust security posture for your environment.
You can discover most API threats using an advanced pentesting tool. Such a tool will thoroughly simulate a real-world attack on your applications and discover insecure API endpoints. Moreover, let’s learn more about broken object level authorization, how it occurs, and ways to prevent it.
Identify vulnerabilities with 98.9% accuracy and prevent cyber security risks. Uncover Risks Now
Table of Contents
- What is Broken Object Level Authorization (BOLA)?
- How Does BOLA Work?
- Impact of Broken Object Level Authorization Attack on Organization
- Types of Broken Object Level Authorization
- Why Discovering BOLA Vulnerability is Important?
- How to Prevent and Mitigate Risks from BOLA Vulnerability?
- Take API Security to the Next Level with ZeroThreat
What is Broken Object Level Authorization (BOLA)?
Broken Object Level Authorization (BOLA) is an access control flaw where an application exposes object identifiers and fails to verify whether the requesting user is allowed to access them. Attackers can simply change an ID in the request like a user ID, order ID, or file ID and access data that doesn’t belong to them.
BOLA is also referred to as IDOR (Insecure Data Object Reference) vulnerability. It’s one of the most critical security vulnerabilities that sits on top of the OWASP Top 10 API Security Risks list because it directly affects sensitive data.
Let’s understand it with an example.
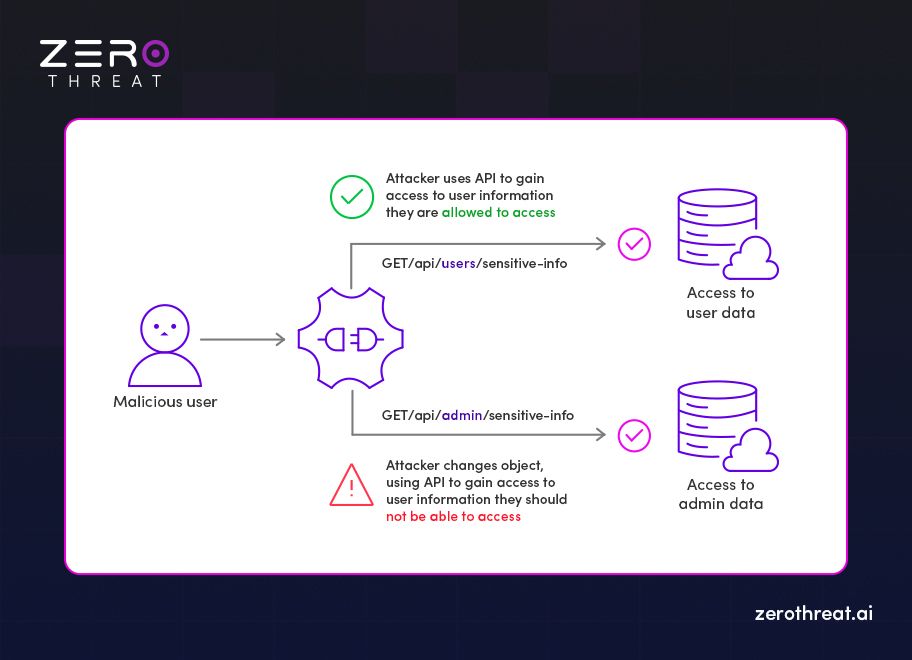
Imagine an API endpoint that returns sensitive user information, like /api/users/sensitive-info. A normal, authenticated user can access their own data through this endpoint. However, a malicious user notices that the admin panel likely uses a similar structure.
They simply change the request from /api/users/sensitive-info to /api/admin/sensitive-info. If the server doesn’t perform a strict object-level authorization check, it might fulfill this request. Suddenly, the attacker gains access to highly privileged admin data without any escalation of credentials, just by guessing or modifying the object reference in the API call.
This happens because APIs often assume that if a user is authenticated for one type of data, the request itself can be trusted. But authentication (who you are) and authorization (what you are allowed to do) are completely different. Without verifying permissions on every single request, BOLA gives attackers a straightforward path to data they should never see.
How Does BOLA Attacks Work?
BOLA attacks happen when an application exposes object IDs and skips proper authorization checks. This creates a simple path for attackers: find how the app references objects, change those references, and access data that doesn’t belong to them. Here’s how the attack unfolds in practice with an example.
1. Identifying the Vulnerability
An attacker starts by looking for the Broken Object Level Authorization flaw. The attacker examines how application URLs or API endpoints are constructed. When there is a direct reference to objects, it indicates that the target application or API is vulnerable to BOLA attacks.
For example, there is a pseudo API endpoint for a finance application that downloads statement with the following URL:
example.com/statements/download_as_pdf?statement_id=1025
Now an attacker can manipulate the statement_id to access and download the statements for other users.
Let’s see another example of BOLA provided by OWASP. It is regarding an online document storage application that enables users to edit, delete, and store documents. A GraphQL mutation comprising a document ID is forwarded to the API when a user attempts to delete a document. Look at the following code to see the working:
POST /graphql { "operationName":"deleteReports", "variables":{ "reportKeys":["<DOCUMENT\_ID>"] }, "query":"mutation deleteReports($siteId: ID!, $reportKeys: [String]!) { { deleteReports(reportKeys: $reportKeys) } }" }In this case, the problem occurs when the code enables users to delete documents without checking for requisite permissions. Consequently, a user could accidentally or purposely delete another user’s document.
2. Modifying the Object Reference
After finding a potential object reference weakness, aka BOLA vulnerability, the attacker will manipulate the object ID. The ID is the reference to the object that is sent within an API request. The ID can be a sequence of integers or a generic string. The attacker can identify them in the request headers, query string parameters, or path.
Once the object reference is discovered, the attacker can manipulate it. In some cases, it can be as simple as modifying digits or could be complex based on the application logic and URL structure. An attacker can obtain the ID and perform actions on behalf of another user in case requests are not properly authorized.
3. Accessing Unauthorized Data
Eventually, the attacker gains unauthorized access to data by successfully manipulating the reference. There will be dire consequences for the users as the attacker can modify personal information, account settings, make transactions, and do other unethical activities. It results in a data breach and puts user data at risk of theft and manipulation.
Protect your data with thorough API security testing and eliminating risks. Let’s Scan Now
Impact of Broken Object Level Authorization Attack on Organization
The Broken Object Level Authorization API vulnerability leads to severe impacts on your organization. It not only puts your sensitive data at risk but also expands your attack surface for a bigger attack. It can also be challenging to cope with a data breach when it happens due to this vulnerability.
The best-case scenario would be to perform a API penetration test, detect vulnerabilities and remediate such security loophole. Let’s see the overall impact of a BOLA attack.
- There is a strong possibility of data exposure when there is a BOLA or IDOR vulnerability. Attackers can easily exploit these vulnerabilities by using scripts. Consequently, your data can be compromised.
- An attacker can manipulate data by editing, delete, modify, or view the data.
- By exploiting this vulnerability, an attacker can even take control over admin accounts.
- An attacker can get privilege escalation providing access to resources that only high-level users can access.
- The incident of a data breach will result in reputational damage. It will be hard to retain existing customers or acquire new ones.
- A data breach will result in compliance issues and attract penalties and legal action.
Types of Broken Object Level Authorization
Broken Object Level Authorization (BOLA) is a vulnerability that takes place when an application improperly implements authorization checks for user-specific objects or resources. Let’s check out its main types.
Insecure Direct Object References (IDOR)
This type of BOLA vulnerability occurs when the exploiter misuses input parameters to access or modify objects they are prohibited to interact with. For example, modifying a URL parameter to access someone else's data.
Missing Authorization Checks
This occurs when a system can’t verify whether a user has the required permissions to access a particular object or resource. This can cause unauthorized access if the authorization logic is not enforced or is bypassed.
Broken Access Control Logic
It involves flawed implementation of access control measures, where systems fail to properly perform permissions or roles for accessing resources. This leads to potential unauthorized access.
Improper Object Filtering
This vulnerability occurs when the system does not correctly filter objects on the basis of user permissions. This increases the chances of unauthorized access misusing objects they should not be accessible to.
Why Discovering BOLA Vulnerability is Important?
Broken Object Level Authorization is a serious security risk that can lead to unauthorized data disclosure, manipulation, and destruction. Failing to implement access control policies properly is the root cause of BOLA security flaws. Finding and fixing it is crucial to API security.
- Restricting unauthorized access: Often, there are different users with different roles. They have restrictions on what they can access. Identifying and remediating object-level authorization flaws enables you to firmly implement role-based access policies and prevent unauthorized access.
- Avoid data leaks: When confidential data is leaked to an unauthorized party unintentionally, it is known as a data leak. Vulnerabilities like object-level authorization flaws can cause data leaks and expose confidential company information to others. With effective control of data objects, you can ensure your confidential information is not leaked.
- Protect data: Identifying and remediating the BOLA OWASP API risk enables you to effectively protect your data. Attackers steal your data under your nose by exploiting such vulnerability. However, with proper access controls, only users with the requisite permissions can access data, preventing sensitive data exposure.
- Meet compliance requirements: Organizations need to implement proper security controls to protect users’ data under HIPAA, GDPR, and other such regulations. Discovering and resolving API vulnerabilities can help you prevent data breaches and comply with regulations.
How to Prevent and Mitigate Risks from BOLA Vulnerability?
The following are some practices to help you prevent and mitigate the risks arising from insecure data object references.

Ensure Proper Access Controls
Always verify whether a user is allowed to access the specific object they are requesting. Perform authorization checks on every object-level action, not just at login. Enforce role-based access control to keep permissions clear and intentional. This creates a strong first layer of protection against unauthorized access.
Implement Authentication and Session Management
Use strong authentication and maintain secure session handling to ensure each request comes from a verified user. Tie every user action to an active, valid session. Prevent session hijacking and reuse by rotating tokens and enforcing timeouts. It reduces the chance of attackers using stolen or invalid sessions to access sensitive objects.
Use Random UUIDs
Avoid predictable object IDs like numeric sequences. UUIDs make guessing or enumerating object references far harder. Even if an attacker tries to manipulate an object reference, the randomness reduces the chance of finding a valid ID. This adds an extra layer of friction for anyone attempting a BOLA attack.
Implement Rate Limiting
Control how many requests a user can make in a short time. Rate limiting helps stop attackers from rapidly testing object IDs or brute-forcing access to sensitive data. It slows down enumeration attempts and gives your monitoring systems more time to detect suspicious behavior.
Use Zero Trust Security Model
Adopt a mindset where no request is trusted by default. Validate every user, every session, and every object-level action before granting access. Zero Trust forces strict verification and reduces implicit trust that often leads to BOLA vulnerabilities. This approach keeps API access tighter and more controlled.
Perform API Security Testing
Regularly test your APIs using automated pentesting tools and manual pentesting to catch BOLA issues early. Testing helps you understand how object references behave and whether authorization checks are enforced consistently. The earlier you detect gaps, the easier they are to fix. Continuous testing keeps your API security posture strong over time.
Uncover OWASP risks and beyond with an advanced pentesting tool. Check for Free
Take API Security to the Next Level with ZeroThreat
Protect your digital landscape from API vulnerabilities with a proactive approach to security. You can identify all API vulnerabilities with a single click using ZeroThreat. It is a next-gen API penetration testing tool with lots of advanced functionalities.
With zero configuration, you easily start scanning APIs from any platform and scan in minutes with its 10x faster scanning speed. Since it’s a cloud-based solution, it can be easily used without any complex installation process.
ZeroThreat helps you strengthen your security posture by API discovery to detect all public, private, and shadow APIs and identify potential loopholes. The best thing about this vulnerability scanner is that you can identify security threats with near-zero false positives.
Hence, it finds security vulnerabilities that actually exist and provides results with 98.9% accuracy. You can try this tool for free and see how it helps you achieve excellence in API security.
Frequently Asked Questions
What exactly is Broken Object-Level Authorization (BOLA)?
BOLA is a vulnerability where an API fails to check whether a user is allowed to access a specific object. It lets attackers change an object ID and access data that isn’t theirs. This happens because authorization checks are missing or inconsistent. It’s one of the most common weaknesses seen in modern APIs.
What tools and techniques can be used to detect and test for BOLA vulnerabilities?
How can secure API design help prevent BOLA?
Why is BOLA still the top API security risk in OWASP’s latest list?
What coding practices ensure secure object-level authorization?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


