All Blogs
Business Logic Attacks in SaaS: How They Work and How to Prevent Them

Quick Overview: Business Logic Attacks in SaaS exploit flaws in workflows, APIs, and application rules rather than code vulnerabilities. These attacks can bypass payment steps, escalate privileges, or abuse trial features, leading to financial loss and data exposure. This blog explains how they work, their impact, and effective strategies to prevent them.
SaaS applications run core operations from billing to automated workflows. Businesses rely on them to scale fast, serve more customers, and push innovation. But fast growth often brings hidden risks. Business logic vulnerability is one of the endpoints that is often missed at the time of SaaS app security testing.
The reason why business logic attacks in SaaS are hard to identify is that they look legitimate to the system. Attackers don’t exploit technical vulnerabilities; they find weakness in the workflow design of your system and abuse it.
According to recent studies, over 75% of organizations reported SaaS-related security incidents in the past year, among which many traced back to misconfigured permissions or unmonitored APIs.
The fallout of such attacks includes revenue drop, unauthorized access, regulatory penalties, and broken trust. This makes business logic security protection as important as technical ones.
To help you prevent and mitigate business logic attacks, we’ll cover the best strategies you can implement. But before that, let’s start with learning about business logic attacks, their common flaws, and how they work. With that said, let’s get started!
Keep your SaaS app protected from attacks by detecting vulnerabilities with advanced tools. Start Now
On This Page
- Understanding Business Logic Attacks in SaaS
- 7 Common Business Logic Flaws in SaaS Apps
- How Business Logic Attacks Exploit SaaS Applications?
- The Impact of Business Logic Attacks in SaaS
- Strategies to Prevent Business Logic Vulnerability in SaaS
- How ZeroThreat’s AI Can Save Your SaaS App from Business Logic Attacks?
- Wrapping Up
Understanding Business Logic Attacks in SaaS
Business logic defines how a SaaS application processes user actions and enforces rules. It’s the set of rules that guide how the system behaves. A business logic attack in SaaS happens when an attacker manipulates these workflows to bypass intended rules and gain unauthorized access. Unlike typical security flaws like SQL injection, business logic attacks target the core functioning of the application rather than technical vulnerabilities.
These attacks are often subtle because they exploit what the system is supposed to do. For example, an attacker might trick an eCommerce SaaS into giving discounts repeatedly by abusing the checkout workflow. The actions appear legitimate from a technical perspective, making detection of such an attack challenging.
SaaS platforms are particularly vulnerable because their workflows involve multiple user roles and API integrations. API business logic vulnerabilities in SaaS are common entry points for attackers to manipulate endpoints and exploit the system.
Plus, detecting business logic vulnerabilities requires a deep knowledge of how the application should behave. This is where human insight, combined with AI detection of business logic vulnerabilities, can make a difference. AI-driven SaaS app security solutions can monitor unusual workflow patterns and detect attempts to abuse business logic in real time.
7 Common Business Logic Flaws in SaaS Apps
Business logic flaws in SaaS apps happen when the system’s intended workflow can be manipulated by users. These flaws are not technical bugs but gaps in the way processes are designed. Attackers exploit these gaps to bypass restrictions, gain unauthorized access, or manipulate application behavior.
Here are some of the common business logic vulnerabilities that attackers target.
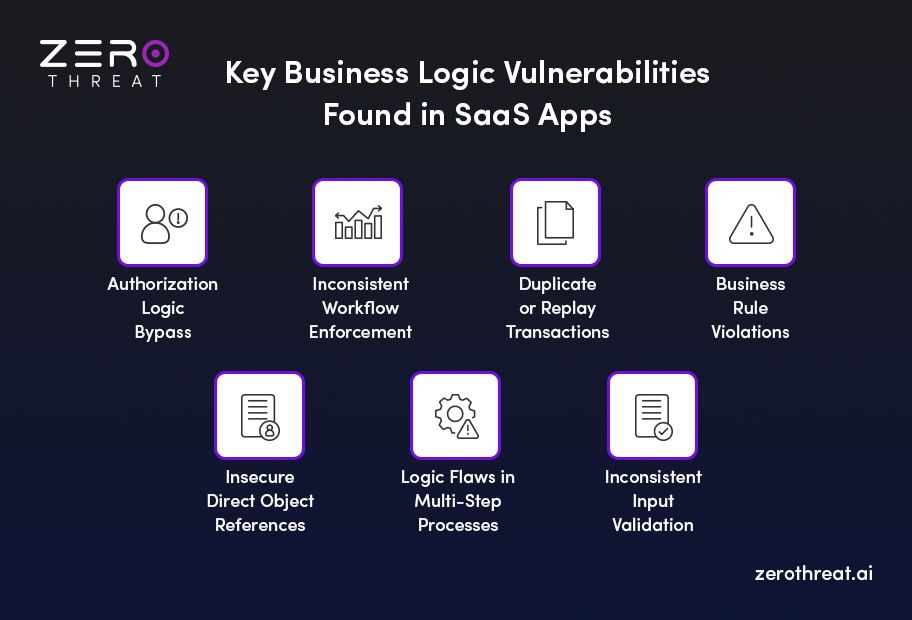
1. Authorization Logic Bypass
This flaw occurs when users access features or data they shouldn’t. For example, a basic user might gain admin privileges due to weak role checks. Attackers exploit this to view sensitive information or perform restricted actions. Proper access control and workflow validation are key to preventing authorization bypass.
2. Inconsistent Workflow Enforcement
Some SaaS applications allow users to skip steps in critical workflows. For instance, a subscription-based service might let users activate premium features without completing payment. Attackers exploit these gaps to misuse services or gain unfair benefits. By checking for logic flaws at every workflow stage, you can avoid this weakness.
3. Duplicate or Replay Transactions
Duplicate transactions happen when the system doesn’t prevent repeated actions, like multiple discount redemptions or repeated API calls. Attackers take advantage of such flaws to gain financial benefits or manipulate system processes. You can implement unique transaction IDs and proper validation to stop this abuse.
4. Business Rule Violations
Applications may fail to enforce specific business rules, like quantity limits or usage caps. Attackers exploit this to bypass limits, overload services, or manipulate analytics. Clear rule enforcement in the SaaS code and through APIs reduces the risk of this vulnerability.
5. Insecure Direct Object References (IDOR)
IDOR vulnerabilities allow attackers to manipulate object identifiers, like URLs or API parameters, to access and modify resources they shouldn’t. For example, changing an invoice ID to view someone else’s billing information. This is why proper authorization checks on requests made by the user are important.
6. Logic Flaws in Multi-Step Processes
Complex SaaS workflows often involve multiple steps, approvals, or integrations. Attackers exploit weak points between steps, like skipping approvals or triggering unintended actions. Regular penetration testing and monitoring of these multi-step processes help catch these flaws early.
7. Inconsistent Input Validation
Even when input validation exists, it’s sometimes bypassed in workflows, allowing users to manipulate calculations, discounts, or outputs. Attackers exploit this to alter application behavior. Strong validation at both the front-end and back-end is required to mitigate this risk.
How Business Logic Attacks Exploit SaaS Applications?
Business logic attacks in SaaS apps exploit the way workflows, rules, and processes are designed. These attacks often appear normal to the application, making them difficult to detect. Understanding how they work will help you protect your SaaS apps from costly misuse.
Step 1: Understanding Workflows
Attackers start by studying the SaaS application to understand its workflows and business rules. They observe how users interact with the system and identify points where rules are enforced or skipped. This step allows them to spot potential vulnerabilities.
Step 2: Identifying Weak Points
Next, attackers look for gaps in the application’s business logic. This could be missing validations, incomplete role checks, or loopholes in multi-step processes. Weak business rules are the doors through which attackers gain unauthorized access.
Step 3: Exploiting APIs and Integrations
Many SaaS applications rely on APIs and third-party integrations. Attackers manipulate these endpoints to trigger actions that benefit them and are not legal. For example, they may bypass usage limits, modify data, or gain access to restricted resources.
Step 4: Abusing Workflow Sequencing
Complex SaaS processes often require users to complete tasks in a specific order. Attackers exploit flaws in this sequence, skipping steps or repeating actions. This allows them to take advantage of discounts, subscriptions, or system resources without following proper procedures.
Step 5: Performing Unauthorized Transactions
Once gaps are found, attackers execute unauthorized transactions. These can include repeated payments, unearned credits, or access to premium features. Each action appears legitimate to the system, making the detection of attacks difficult without behavioral monitoring.
Step 6: Covering Tracks and Evading Detection
Finally, attackers take steps to avoid detection. They mimic normal user behavior or use automated scripts that blend with regular traffic. Without AI-driven monitoring or thorough workflow validation, these attacks can continue unnoticed for a long time.
Business logic attacks in SaaS are simple but effective because they exploit the intended behavior of the system. Without AI tools that can recognize such attack patterns and a human who can interrupt them, the business logic attack will continue to let hackers exploit your SaaS app.
Discover and fix security risks with the most accurate vulnerability scanning tool. Scan at $0
The Impact of Business Logic Attacks in SaaS
Business logic attacks are as damaging as any other security threat. Since these attacks exploit how an application is designed to work, the consequences directly hit revenue and customer trust.
Financial Losses
Attackers often exploit pricing logic, discount workflows, or subscription models. For example, repeatedly applying coupons or bypassing payment validation leads to direct revenue loss. In SaaS, even small abuses at scale can add up to massive financial losses.
Data Exposure
Business logic flaws can lead to sensitive data exposure by manipulating IDs or API parameters. Exposed customer records, billing details, or business insights violate trust and put the company at risk of compliance regulatory fines.
Operational Disruptions
When attackers bypass quotas or system limits, SaaS resources can be overused or abused. This results in performance degradation, unexpected downtime, or inflated infrastructure costs. The worst part is that these disruptions are caused by activity that looks “normal” or “legitimate” to the system.
Reputational Damage
Trust is everything for SaaS providers. Once customers realize the system can be manipulated, confidence drops. Competitors gain an advantage, and negative perception can spread quickly, especially if the breach becomes public. Rebuilding that trust is far more expensive than preventing the attack in the first place.
Compliance Issues
If business logic attacks lead to data breaches, companies face penalties under regulations like GDPR, HIPAA, or PCI DSS. Regulators don’t differentiate between a coding flaw and a logic flaw; the responsibility of customer data security lies with the SaaS provider.
Long-Term Risks
Beyond the financial and reputational hit, business logic vulnerabilities undermine product reliability. Investors, partners, and large customers may view the SaaS as insecure. That may slow down growth opportunities and directly affect market competitiveness.
Business logic attacks create tangible risks across finance, operations, and security compliance. Detecting and preventing these flaws early through business logic vulnerability detection tool and AI-driven monitoring is the easiest way to avoid them.
Strategies to Prevent Business Logic Vulnerability in SaaS
Below are practical measures every SaaS team should follow to prevent business logic vulnerability and attacks.
Principle of Least Privilege (PoLP)
Users should only have the minimum access needed to perform their role. For example, a customer support agent doesn’t need admin-level permissions. Implementing PoLP reduces the damage an attacker can do if accounts are compromised or roles are misused.
Input Validation and Sanitization
Attackers often manipulate input fields or API parameters to bypass logic or rules. Strict input validation ensures only expected data is processed. On the other hand, sanitization blocks malicious attempts such as SQL injection and cross-site scripting attacks.
Regular Penetration Testing
Business logic flaws are hard to detect with automated scans alone. Regular penetration testing helps uncover these vulnerabilities by simulating real-world abuse of workflows. Plus, including a manual business logic test can help you secure your system fully.
Rate Limiting Controls
Attackers can abuse business logic by sending repeated or automated requests. Rate limiting controls and prevents brute force attempts, repeated coupon redemptions, or excessive API calls. Setting a real-world threshold helps you protect SaaS applications from logic-based attacks.
Security Configuration Management
Misconfigured configuration of APIs, integrations, or roles can create business logic vulnerabilities. Regularly reviewing configurations ensures permissions, access rules, and workflows align with security and compliance requirements.
Logging and Monitoring
Detailed logging of user actions and API calls makes it easy to spot unusual activity. Monitoring tools can flag repeated requests, skipped steps, or abnormal workflows. These insights can help you catch business logic vulnerabilities before they grow.
How ZeroThreat’s AI Can Save Your SaaS App from Business Logic Attacks?
Business logic attacks might go undetected with traditional testing tools, which can result in fraud and financial loss. This is where ZeroThreat, an AI-based testing tool, helps you prevent them with ease. Here is how:
- ZeroThreat simulates real attacker behavior, uncovering flaws like privilege escalation, workflow abuse, or bypassed validations without relying on manual checks.
- Its Dynamic Application Security Testing tool (DAST) detects logic-based vulnerabilities for API and web app security.
- Detection comes with clear exploit evidence and AI-driven remediation steps, making fixes faster and less error-prone for developers.
- Integrated into CI/CD, ZeroThreat keeps testing every release, ensuring new features don’t have hidden logic risks.
- It detects shadow or zombie APIs where logic flaws often hide, securing your SaaS beyond just the obvious endpoints.
With ZeroThreat, security teams cut 90% of manual pentest effort, while gaining 98.9% accurate vulnerability detection. For SaaS, that means faster releases without sacrificing trust and security.
Secure your SaaS app before the attack with unmatched security tools. Contact Us
Wrapping Up
With sensitive data, customer trust, and revenue on the line, protecting against business logic attacks in SaaS is not optional. These attacks exploit overlooked workflows, misused APIs, and design flaws that traditional testing tools often miss.
To stay resilient, SaaS providers must enforce the least privilege and input validation along with regular penetration testing to detect vulnerabilities. If you want to secure your SaaS app, using ZeroThreat’s AI-based automated pentesting tool and DAST platform will simplify your work.
Frequently Asked Questions
Can business logic attacks be prevented with penetration testing?
Yes, advanced pentesting tools simulate real-world attacks, combined with input validation and rate limiting, can reduce the risk of cyber-attacks.
How often should SaaS companies test for business logic vulnerabilities?
Why are business logic attacks hard to detect?
How can SaaS teams test for business logic vulnerabilities?
What types of business logic attacks are most common on SaaS platforms?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


