All Blogs

Quick Overview: The OWASP Top 10:2025 introduces major changes that reflect today’s evolving application security risks. This update adds two new categories, shifts existing rankings, and redefines how teams should approach testing and secure development. This blog breaks down what’s new, what changed, and why these updates matter for your security strategy.
The OWASP community has always played a key role in helping teams build safer software. In a world where attackers evolve faster than most development cycles, having a trusted, open-source standard to guide security decisions is more important than ever. That’s why the OWASP vulnerabilities remain the most widely referenced resource in application security.
Every few years, OWASP updates the list to reflect real-world attack patterns and the latest data from security researchers. The 8th installment, OWASP Top 10 2025 version, highlights the shift in how modern applications fail from supply chain weaknesses to overlooked error handling that exposes sensitive data.
In this blog, we’ll break down what’s new in the OWASP Top 10 2025, what changed from the previous list. We’ll also dive into what this update means for developers and security teams.
Turn the new OWASP 2025 into your security advantage today. Try for $0
On This Page
- What's New in the OWASP Top 10 2025: The Big Picture
- OWASP Top 10 for 2025: Quick Overview
- New Risk Categories in OWASP Top 10 Update
- The Latest OWASP Top 10 for 2025 List
- OWASP Top 10 Update for Security Teams and Developers
- Role of ZeroThreat in Maintaining Security
- Wrapping Up
What's New in the OWASP Top 10 2025: The Big Picture
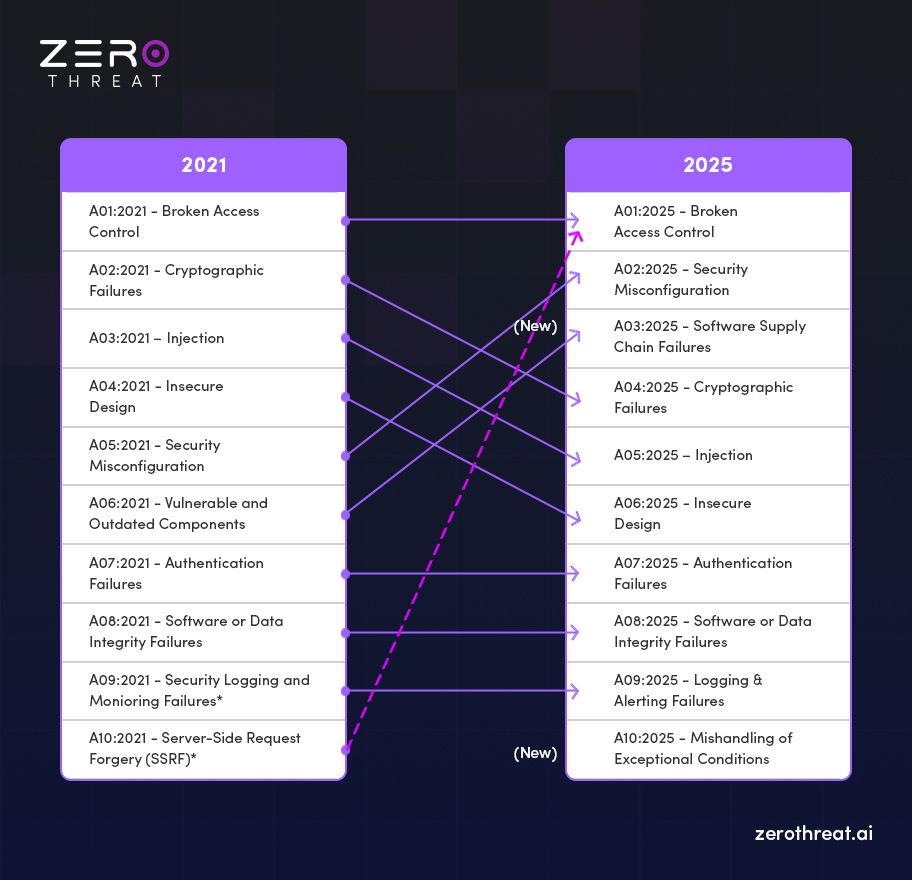
The OWASP Top 10 2025 update brings meaningful shifts that reflect how modern applications are built and attacked. Two new categories have been introduced, along with one consolidation.
Here is an overview of these updates:
1. A03: Software Supply Chain Failures: It is a major addition, expanding the older “Vulnerable and Outdated Components” category to cover the entire software ecosystem, starting from third-party dependencies to CI/CD pipelines and distribution systems.
2. A10: Mishandling of Exceptional Conditions: This new category highlights how weak error handling and poor resilience can expose critical vulnerabilities. It also shows the importance of secure error handling and resilience.
Along with these two categories, OWASP has consolidated A10:2021 Server-Side Request Forgery (SSRF) into A01:2025 Broken Access Control, emphasizing how SSRF often stems from broader access control issues.
Meanwhile, Broken Access Control and Security Misconfiguration continue to lead the latest OWASP Top 10, proving that foundational security failures still dominate real-world breaches. Overall, the new OWASP Top 10 2025 shifts focus from isolated bugs to systemic, software development lifecycle-wide weaknesses.
The OWASP Top 10 for 2025: Quick Overview
| Rank | Category | Summary |
|---|---|---|
| A01:2025 | Broken Access Control | Remains the top risk; covers flaws that let attackers bypass authorization, escalate privileges, or gain unauthorized access. |
| A02:2025 | Security Misconfiguration | Involves weak default settings, exposed services, and inconsistent security controls across environments that create an attack surface. |
| A03:2025 | Software Supply Chain Failures | Expanded to cover vulnerabilities in dependencies, CI/CD systems, build tooling, and distribution infrastructure. |
| A04:2025 | Cryptographic Failures | Covers insecure or outdated encryption practices, poor key management, and use of deprecated protocols that expose sensitive data. |
| A05:2025 | Injection | Includes classic input-validation flaws such as SQL, OS command injection, and template injection that allow untrusted input to alter commands or queries. |
| A06:2025 | Insecure Design | Results from weak architectural choices and missing threat modeling, producing systemic design-level security gaps. |
| A07:2025 | Authentication Failures | Includes broken or weak login flows, weak password policies, and session handling errors that enable account compromise. |
| A08:2025 | Software or Data Integrity Failures | It highlights cases where code or data can be modified or tampered with, often via update mechanisms or pipelines, without proper controls. |
| A09:2025 | Logging & Alerting Failures | Refers to insufficient monitoring, logging, or alerting practices that prevent timely detection and response to incidents. |
| A10:2025 | Mishandling of Exceptional Conditions | It focuses on unsafe error handling, poor failure modes, and a lack of resilience when systems hit edge cases. |
Detailed Breakdown of the New Risk Categories in OWASP Top 10 Update
As we discussed above, the OWASP Top 10 2025 update introduces two new categories that reflect how modern software is built and how security failures occur. Here is a deeper dive into the same.
A03:2025 – Software Supply Chain Failures
Software supply chain failures happen when the tools, libraries, or services your product depends on become compromised. Most teams don’t realize how many third-party components they rely on until something breaks. And when a dependency fails, it can expose the entire application. This risk increases as teams adopt more open-source packages and external integrations.
These failures usually begin with a malicious update, misconfigured package, or hijacked repository. That means it can introduce vulnerabilities without anyone noticing. Even trusted vendors can unintentionally ship insecure versions. By the time the issue is discovered, attackers may already have leveraged the weakness.
To reduce this risk, teams need better visibility over their dependencies. Regular dependency scans, strong version control policies, and vendor risk checks are required. And when updates roll out, testing them quickly and safely is essential.
A10:2025 – Mishandling of Exceptional Conditions
Exceptional conditions are those “edge cases” most developers don’t think about until something fails in production. These include timeouts, memory limits, overloaded queues, or unexpected user inputs. When systems don’t handle these moments safely, they can expose sensitive data or open new attack paths. What seems like a minor crash can turn into a serious vulnerability.
The exceptional conditions often appear when the software is tested on edge cases, not during normal usage. When the system is under high load, small business logic gaps become bigger problems. Error messages might reveal internal details, or a failure may bypass key security checks. Attackers actively exploit these blind spots because they know many applications ignore them.
To stay safe, teams must plan for the unexpected. That means adding proper error handling, testing failure scenarios, and making sure systems tackle them as intended. A proper handling of exceptional conditions keeps your application resilient against surprise attacks.
See where your app stands across OWASP 2025 risks with pentesting. Run Automated Pentest
The Latest OWASP Top 10 for 2025 List
OWASP’s 2025 list highlights the risks that matter most today. Here’s a simple, side-by-side look at the new ranking and how it compares to the previous version (OWASP 2021).
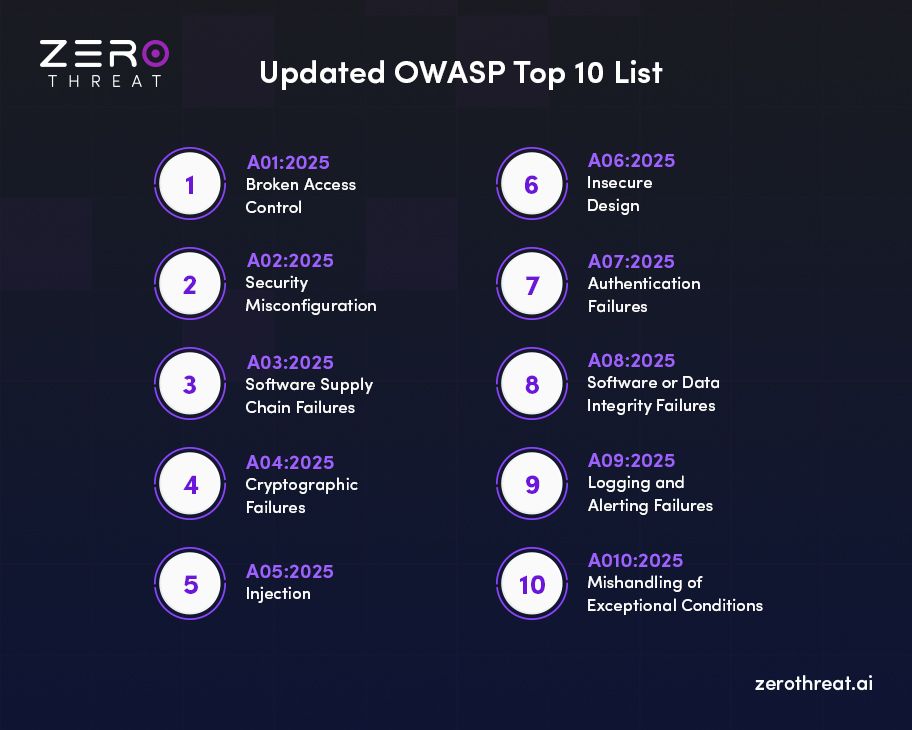
A01:2025 - Broken Access Control
Broken Access Control stays at the #1 spot, showing it remains the most critical and widespread application security risk. This year’s data shows that 3.73% of tested applications contained one or more of the 40 CWEs in this category. OWASP also rolled Server-Side Request Forgery (SSRF) into this risk, reflecting how access flaws often enable deeper lateral movement.
A02:2025 - Security Misconfiguration
Security Misconfiguration climbs from #5 in 2021 to #2 in 2025, driven by higher prevalence across modern applications. About 3.00% of tested apps had at least one of the 16 CWEs tied to misconfiguration issues. As more application behavior depends on configuration files, cloud settings, and environment-level controls, these mistakes have become far easier for attackers to exploit.
A03:2025 - Software Supply Chain Failures
Software Supply Chain Failures is an expansion of the older A06:2021 “Vulnerable and Outdated Components” to cover attacks across dependencies, build systems, and distribution pipelines. It is ranked as a top community concern because of the difficulty in detecting supply chain compromises. It includes only 5 CWEs but carries the highest average exploitability and impact scores across modern CVEs, making it one of the riskiest threats.
A04:2025 - Cryptographic Failures
Cryptographic Failures has slipped two spots to #4, but it remains one of the most dangerous risks for sensitive data. Nearly 3.80% of applications contain at least one cryptographic weakness, showing how often encryption is implemented incorrectly. These failures often lead to sensitive data exposure, broken confidentiality, or full system compromise.
A05:2025 – Injection
Injection moves from #3 to #5, even though it continues to be heavily tested across modern applications. It includes 38 CWEs ranging from common Cross-Site Scripting issues to severe SQL Injection flaws. While frequency varies, injection flaws remain high-impact when exploited, especially in data-driven applications.
A06:2025 - Insecure Design
Insecure Design shifts from #4 to #6 as other categories rise in priority. First introduced in 2021, it reflects problems rooted in missing or weak security design practices. OWASP notes improvements in secure design and threat modeling, but the category still highlights how early architectural choices shape long-term security.
A07:2025 - Authentication Failures
Authentication Failures holds steady at #7, with a refined name that better reflects the 36 CWEs it covers. While still a critical risk, the rise of modern authentication frameworks is helping reduce many common weaknesses. Even so, flaws in session handling and authentication logic continue to create paths for unauthorized access.
A08:2025 - Software or Data Integrity Failures
Software or Data Integrity Failures remains at #8, focusing on risks where systems fail to maintain or validate the trust boundaries around code and data. These issues occur at a deeper level than supply chain failures and often involve untrusted updates, unsafe deserialization, or tampering risks. When integrity checks are missing, even small changes can compromise entire systems.
A09:2025 - Logging & Alerting Failures
Logging & Alerting Failures stays at #9, with a name update that highlights the importance of alerting, not just monitoring. OWASP notes that logs without action-triggering alerts do little to help detect real incidents. Although the data underrepresents this category, community voting again confirmed its importance.
A10:2025 - Mishandling of Exceptional Conditions
Mishandling of Exceptional Conditions is the newest entry for 2025, covering 24 CWEs tied to improper error handling and system behavior under stress. These failures occur when applications “fail open,” expose sensitive details, or behave unpredictably during abnormal events. The new category pushes teams to design software that is resilient, predictable, and safe.
What Does OWASP Top 10 Update Mean for Security Teams and Developers?
The 2025 update is a reminder that modern application security is about understanding how systems behave end-to-end. Security teams now need deeper visibility into supply chains, runtime behavior, and architectural decisions that developers make every day. The list makes it clear that risks are shifting toward systemic weaknesses, not just isolated code flaws.
For developers, this update reinforces that secure coding isn’t enough unless the surrounding ecosystem is also hardened. Misconfigurations, weak error handling, and integrity issues often come from assumptions made during development, not malicious intent. The new categories push teams to think beyond functions and frameworks and consider how their applications operate under real-world conditions.
For security teams, the changes highlight the need for better testing depth, not just testing for more vulnerabilities. The rise of supply chain and resilience-focused risks means traditional scanners won’t catch everything, and manual validation becomes more important. The update essentially calls for collaboration of developers, architects, and security engineers working together to design systems that have a reduced cybercrime cost and recover quickly.
How ZeroThreat Can Help You Maintain Security Against the OWASP Top 10
Staying aligned with the OWASP Top 10 is hard when threats evolve faster than traditional scanners. ZeroThreat helps teams keep up by continuously validating real-world risks by showing how threats behave when attacker-like behavior is simulated using an automated pentesting tool.
Here is a breakdown of how ZeroThreat tackles each of the latest OWASP Top 10 vulnerabilities:
- A01: Broken Access Control: ZeroThreat automatically tests for unauthorized resource access, validating access rules the same way an attacker would.
- A02: Security Misconfiguration: The platform identifies weak defaults, exposed services, and inconsistent configurations across environments with automated environment-wide checks.
- A03: Software Supply Chain Failures: ZeroThreat maps third-party dependencies, flags outdated or risky components that could expose your supply chain.
- A04: Cryptographic Failures: It inspects encryption practices, flags weak or deprecated algorithms, and ensures sensitive data isn’t exposed through poor crypto implementation.
- A05: Injection: ZeroThreat runs active payloads for SQL injection, command injection, and more to confirm whether the application is actually vulnerable or not.
- A06: Insecure Design: The platform highlights architectural flaws by testing workflows, data flows, and business logic paths that lack proper security controls.
- A07: Authentication Failures: ZeroThreat checks session handling, credential flows, MFA logic, and standardized auth frameworks for gaps that attackers could use to bypass authentication.
- A08: Software or Data Integrity Failures: ZeroThreat validates the integrity of client-side code (like Sub-resource Integrity) and attempts to tamper with serialized data to catch vulnerabilities where data integrity is not enforced.
- A09: Logging & Alerting Failures: ZeroThreat intentionally triggers application errors and invalid states to check if the system leaks sensitive stack traces or fails to handle exceptions, indicating gaps in secure logging practices.
- A10: Mishandling of Exceptional Conditions: The platform tests how your system handles unexpected inputs or failures to ensure errors don’t expose sensitive logic or create new attack paths.
Need help securing your software product? Let our experts guide you. Talk to Us
Wrapping Up
The OWASP Top 10 2025 makes one thing clear: the threat landscape is shifting faster than most teams realize. New categories like supply-chain failures and unstable error handling show how modern apps break in places we rarely looked at a few years ago. This update is a reminder to rethink how we test, validate, and maintain security in real time.
Security testing tools can help, but only when they go beyond surface-level scans. That’s where ZeroThreat adds real value. Its automated penetration testing tool tests your applications the way attackers actually would, offering you near-zero false positives. And with built-in coverage for OWASP Top 10 risks, it helps you fix what matters with AI-powered remediation reports.
Frequently Asked Questions
What is the OWASP Top 10:2025 and how does it differ from the 2021 edition?
The OWASP Top 10:2025 is the latest update highlighting the most critical web application security risks. It differs from the 2021 edition by introducing broader, ecosystem-level risks like Software Supply Chain Failures and adding a new category for mishandling of exceptional conditions. It also includes category shifts, consolidations, and updated rankings based on new data and community feedback.
Which categories are new in the OWASP Top 2025 list, and why were they added?
Which existing categories have changed position, and what does that shift signal?
Were any categories merged, removed, or substantially redefined in this update?
How should the update impact risk assessment, testing, and secure development lifecycles?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


