All Blogs
CVE: A to Z Guide to Learn About Common Vulnerabilities and Exposures

Summary: CVE, aka common vulnerabilities and exposures, is frequently mentioned and heard when discussing cybersecurity. But it's often perceived in a different context by many of us. In this blog, we will talk all about CVE and clear all the misconceptions that are usually found about it. By the end of this blog, you will have a clear understanding of CVE.
In today's day and age, the digital revolution is all over the world; all industries have been adopting it zestfully. Since the world is embracing digitalization, cybersecurity threats are evolving and taking a significant scope as well!
In such cases, having a detailed idea of potential vulnerabilities and cybersecurity threats is a must! Common vulnerabilities and exposures, i.e., CVE, is a concept managed by MITRE Corporation that exists to eradicate the exploitation of sensitive data.
In this blog, we will learn about common vulnerabilities and exposures, their core purpose, and all the other essential details that allow you to leave no room for vulnerabilities and malware attacks that may cause data misuse.
Say Goodbye to Potential Security Threats with Our Robust Vulnerability Scanner Try it Now
Table of Contents
- What is CVE?
- What Process Does CVE System Follow?
- What are the Core Purposes of CVE?
- What is the difference between Vulnerabilities and Exposures?
- What Factors Determine Vulnerability’s Eligibility?
- Top Public CVE Databases
- What is CVSS?
- How Optimal Security Tool Like ZeroThreat Can Help You?
What are Common Vulnerabilities and Exposures?
CVE is a platform where you will find all the publicly known information security vulnerabilities and exposures. Think of CVE as a giant list of standard vulnerabilities/problems in computer systems that are publicly accessible. Every vulnerability has a respective code known as CVE ID. With these listed problems with specific codes, it becomes easier for experts to address them and fix them in the cybersecurity domain. As soon as any new vulnerability is discovered, it gets listed with a particular code to CVE.
As per Statista's report, internet users globally have come across 612 new common IT security vulnerabilities and exposures (CVEs). The highest reported annual figure was recorded in 2023, over 29,000.
What Process Does CVE System Follow?
The common vulnerabilities and exposure system is a framework for identifying and cataloging publicly known cybersecurity vulnerabilities and exposures. Let’s see how does the CVE system work.
Identification and Reporting
Vulnerabilities assessed by vendors, researchers, or security professionals These discoveries can be reported to various entities like CVE Numbering Authorities (CNAs) or directly to MITRE. CNAs are organizations authorized by MITRE to assign CVE IDs to vulnerabilities.
Assignment of CVE Identifiers
A CVE ID is a unique identifier assigned to each vulnerability. It follows the format `CVE-YYYY-NNNNN`, where `YYYY` is the year of the vulnerability disclosure, and `NNNNN` is a sequential number.
CNAs take care of the assignment process of CVE IDs for vulnerabilities within their scope.
Documentation
Once the assignment of CVE IDs is completed, comprehensive information about each vulnerability is documented. These comprehensive details cover information about a vulnerability, its impact, affected products, and any references or links to further information.
Publication
The information is integrated into the CVE database which is publicly available. This database is a central repository for all CVE entries and can be queried by anyone. Moreover, concerned parties like affected enterprises, security professionals, vendors, are informed every time the new CVE entries are registered.
Use and Integration
Security tools, such as vulnerability scanners and threat intelligence platforms, optimize CVE identifiers to identify and track vulnerabilities in systems and applications. Also, businesses optimize data present in CVE database to prioritize and manage patches and updates based on the vulnerabilities that affect their systems.
Uniform Updates
The CVE database is continuously updated with new vulnerabilities and modifications to existing entries. As it’s a publicly available database for every concerned entity to learn about current vulnerabilities and their impact on systems’ security.
What are the Core Purposes of CVE?
CVE’s job is not all about helping audience with potential vulnerabilities, but a lot more than that. Check out these points to know CVE’s core purposes.
Centralized Repository
CVE manages an extensive database of common vulnerabilities and exposures, which is publicly available. This is not just a database but an in-depth piece of information that is extremely useful for security researchers, vendors, enterprises, and ordinary people interested in obtaining insights regarding known security issues.
Promotes Sharing Insights
Even though the vulnerabilities are accessible to everyone for the purpose of fixing them with optimal solutions, cybersecurity analysts and beginners in the domain can access this information to learn about potential security threats and glitches and collaborate on creating foolproof solutions.
Reduces Risk
When you have an extensive database of potential threats, you can continually optimize your web apps and other digital assets to boost security. It's always a good practice to continuously perform security testing with a reliable web app security scanner to ensure digital product's security. It will help secure your digital assets from common vulnerabilities and exposures.
Policy and Compliance
CVE adheres to policy development, compliance initiatives, and regulatory requirements in the cybersecurity domain. Enterprises can optimize CVE data to demonstrate compliance with fundamental security principles, regulations, and ideal practices by learning about potential vulnerabilities in their systems.
This is all about CVE's purpose, which is much more than making the database accessible to the public. Remember, you can utilize this database of common vulnerabilities and exposures and boost your product's security by optimizing the data for multiple purposes, as mentioned above. It'll be an added advantage for you if the differences between vulnerabilities and exposures are apparent.
What is the Difference between Vulnerability and Exposure?
Vulnerability is a weakness in a computer system that can be easily misused, whereas exposure is a situation in which vulnerability already exists and can be manipulated for fraudulent activities. Check out the detailed definitions and differences of both.
Vulnerability
Vulnerability is simply a flaw in the computer software or system that easily allows attackers to misuse the data with the help of that flaw.
Attackers generally misuse vulnerabilities to get unauthorized access, privileges, or control over a system or its data.
Vulnerabilities exist within systems, software, configurations, or processes. They can be accidental, like a software bug, or intentional, like a backdoor.
Exposure
Exposure is generally a situation of negligence—a condition where a system, asset, or data is left accessible to potential risk or compromise.
Exposures are the outcome of vulnerabilities but are broader. They comprise the risk posed by vulnerabilities, but there are chances of factors like misconfigurations or human errors.
These are the primary points that differentiate vulnerabilities and exposures from each other. These concepts are somewhat interrelated, but attackers can exploit the two for different purposes.
Let the Attackers Wonder Which Security Tool You Use Quality Scanning in Minutes
What Factors Determine Vulnerability's Eligibility?
There is a specific criterion for vulnerabilities to be counted in the list of common vulnerabilities and exposures. We are mentioning some of the common factors that make the vulnerability eligible to be counted in CVE.
Effect
When we talk about vulnerability, there are many kinds of cybersecurity issues that exist in computer software; not all of them can cause an impact that needs to be highlighted publicly. Only potential vulnerabilities that can cause an adverse impact on sensitive data need to be shed light upon so that people stay away from them, and security experts can build optimal solutions to fix them.
Reproducibility
For vulnerability to be addressed publicly, it must be verified by concerned people like security analysts as a bona fide issue. Then, it can be listed as a potential vulnerability in CVE.
Measurability
If the vulnerability is caught in the system, it must be presented in some sort of measure. There should be metrics to consider how much data has been affected due to a particular problem or how many systems have crashed.
Independent Issue
You cannot consider it as a vulnerability that is a result of something that is already a separate issue. Vulnerabilities are not supposed to be interdependent in order to be listed in CVE.
Vendor Acknowledgement
The relevant vendor is required to take complete responsibility for acknowledging the affected system before disclosing it to the public. So, when it's in the public eye, it can be considered an actual issue.
Documentation
The problem alone sometimes doesn't suffice for people to consider looking into it. Relevant reports, analysis, and documentation add weight to it. So, there should be viable documentation to emphasize the issue.
These are the factors that determine whether your vulnerability is qualified to be added to the CVE list or not. Ensure these factors are considered when any vulnerability is caught in your system.
Top Public CVE Databases
Some popular CVE databases are accessible to everyone for collecting information about vulnerabilities.
SecurityFocus
It is an all-inclusive security resource that encompasses information about common vulnerabilities and exposures.
National Vulnerability Database
This platform is managed by NIST: National Institution of Standards and Technology. You will find a detailed database of vulnerabilities along with CVSS, CVE IDs, and other related insights.
Open-Source Vulnerability Database (OSVDB)
An open-source database that provides the precise, technical, and neutral index on vulnerability security, along with CVE references and severity ratings.
Common Vulnerabilities and Exposures (CVE) List
The official CVE database carries all the information related to vulnerabilities and exposures with CVE IDs, descriptions, and references. It allows you to access vulnerabilities by vendor's name, product, type, and date.
With these open CVE databases, cybersecurity professionals, researchers, enterprises, and even normal people can gain insights and optimize them.
Leave No Chance of Vulnerability in Your Web App Using Zerothreat Safeguard Your App
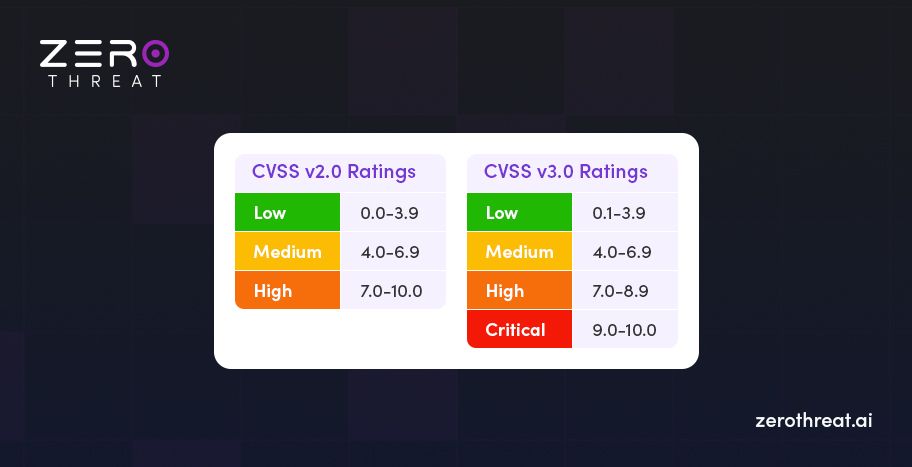
What is CVSS (Common Vulnerability Scoring System)?
Common Vulnerability Scoring System basically ranks and rates vulnerability on the basis of its severity. On the basis of ratings and rankings, viewers understand how adversely it can affect the system and how urgently it should be fixed with a viable solution.
Ideally, vulnerability with the highest number carries a pressing issue. The problem of vulnerability (0-10) ascends subsequently.
How Optimal Security Tool Like ZeroThreat Can Help You?
The concept of common vulnerabilities and exposures is one of the most misunderstood terms in cybersecurity. Our sole purpose is to enlighten our audience about such subjects and enable cybersecurity to get its deserving attention and significance.
You need the right measures and tools to protect your digital assets against potential security threats. Here our robust web app and API security testing tool, ZeroThreat can help. It allows you to scan your web apps and API within minutes! Ultimately diminishing your hour's process and turning it into a minute job.
Try it for free to check its benefits.
Frequently Asked Questions
What are typical examples of CVE?
Buffer overflows, UI errors, authentication errors, channel and path errors, code evaluation and injection, and many more can fit into a list of common examples of CVE.
What is CVSS in CVE?
How does CVE work?
How to prevent security attacks with CVE scanning?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


