All Blogs
Unauthorized Access Explained: The Risks and Consequences You Can't Ignore

Quick Summary: Unauthorized access is a critical security risk for organizations that expose their digital assets to an unknown entity without permission. This article will help you understand how it occurs and how to prevent unauthorized access. Read on to understand this threat and protect your digital assets.
Imagine this: It’s 2 am, and you are scrolling through your Instagram feed when suddenly, an alert pops up on your phone. The message says, “Suspicious login attempt detected.”
Your heart skips a beat as you realize someone is trying to get through your account online. Now, many questions will arise in your mind – how did they get there? What do they want? And most importantly, what damage could they cause?
Well, this is Unauthorized Access. It’s not just a plotline from a Hollywood thriller but a chilling reality for millions of people and businesses worldwide. Every day, hackers and criminals exploit vulnerabilities in systems to gain entry where they don’t belong. From stealing sensitive personal data like credit card numbers and passwords to personal information, unauthorized access is the digital equivalent of leaving your front door wide open – with thieves ready to walk right in.
Unauthorized access is one of the easiest yet most damaging security breaches. It gives access to weak passwords, poorly managed permissions, and unpatched systems to cybercriminals.
So, how can a business implement unauthorized access prevention? The key lies in Zero Trust security, advanced vulnerability testing, and strict access controls. In this blog, we’ll uncover how unauthorized access risks creep into your systems, the devastating impact they leave behind, and—most importantly—how you can stop them before they start.
Because in cybersecurity, the biggest mistake is thinking, “It won’t happen to us.”
Build a Strong Shield for Data Protection by Eliminating Hidden Security Loopholes Let’s Do It
On This Page
- What is Unauthorized Access?
- Examples of Unauthorized Access in Cyber Security
- Why Does Unauthorized Access Occur?
- How Do Individuals Gain Access to Your Digital Assets?
- What are the Risks of Unauthorized Access to Digital Assets?
- How to Prevent Unauthorized Access?
- How Can ZeroThreat Help You Prevent Unauthorized Access?
- To Wrap Up
What is Unauthorized Access?
As per NIST, unauthorized access in cybersecurity occurs when “a person gains logical or physical access without permission to a network, system, application, data, or other resources.”
Unauthorized access in cyber security is an act of accessing an organization’s digital assets without requisite permissions. It might be accidental, due to a cyberattack, or caused by a malicious insider. Plus, it violates the security policies of the organization and results in a data breach.
Let’s understand it by comparing it with a real-world analogy. In the physical world, unauthorized access occurs when a person enters an area they are not permitted to. For example, a person sneaking into a locked office building and entering a place they are not authorized to.
The person bypasses the security protocols in place for protecting the entire building. Plus, the access policy of the organization is also violated. Similarly, an attacker or a malicious employee can access the sensitive data of an organization while not having the required permissions.
There are many disastrous consequences for unauthorized access. For example, the person could steal confidential information, destroy assets, or it could lead to sensitive data exposure. All in all, your digital assets like networks, applications, devices, data, and systems are at risk when someone accesses them unauthorizedly.
Examples of Unauthorized Access in Cyber Security
There are lots of examples where a malicious person accessed unauthorized information. However, we are mentioning two of them that made top headlines.
The First American Financial
The customers’ trust in The First Americal Financial (an American financial corporation) melted away when 885 million customer documents were exposed online. These documents contained sensitive customer information like social security numbers, bank account numbers, mortgage records, and more. All this information was available without any kind of protection. An attacker found an authorization error that enabled them to access documents that only a specific party could view.
Equifax
In 2017, a massive data breach occurred at Equifax (a prominent credit reporting agency) in which attackers accessed and stole data of millions of customers. Attackers could access sensitive data by exploiting a well-known vulnerability that wasn’t patched on time.
Why Does Unauthorized Access Occur?
Unauthorized access occurs for many reasons, involving both technology issues and human actions. Let’s go through some of the reasons why unauthorized access and hacking happen.
Accidental
It might be the case that someone already with access to a system or application could accidentally find data they are not supposed to see. This could happen due to weak access policies. For example, when a person is authenticated with a system’s security mechanism and able to access other files beyond their access rights.
Planned
A malicious insider can purposely intrude into your systems, applications, or databases to steal sensitive information. They might be financially motivated and could misuse their access to bypass security controls and gain access to confidential data.
Hacking
While both the above causes of unauthorized access are internal, hacking is an external threat factor. Here, an attacker can launch a cyberattack against an organization by exploiting vulnerabilities to access sensitive data. The attacker will use attack vectors like SQL injection, XSS, CSRF, etc.
How Do Individuals Gain Access to Your Digital Assets?
Malicious individuals like attackers use various tactics to intrude into a system and steal confidential data. The following are some of these tactics.
Poor Authentication: When there are flaws in the authentication mechanism or it is not implemented properly, an attacker can bypass it to gain unauthorized data access. For example, if a web application doesn’t lock a user after multiple failed login attempts, an attacker can exploit it with brute force to gain access to it.
Vulnerabilities: An attacker can also gain access to a system or application by exploiting known vulnerabilities. There are flaws or weaknesses that can help an attacker overcome security controls.
Social engineering: It is a popular tactic used by an attacker to gain access to a system or application. Attackers can utilize deceptive emails or links to achieve their objectives. Phishing is one of the examples of social engineering.
Insider threat: An employee, business associate, contractor, or any other individual who has legitimate access to your system may also gain access to critical information for malicious purposes.
What are the Risks of Unauthorized Access to Digital Assets?
When a malicious person infiltrates your system, network, or database, they can cause havoc. They not only can steal sensitive data but also damage your system. The following are a few unauthorized access risk examples.

Direct Risks
These are the risks that will directly impact an organization, its users, and digital assets.
Risk to Confidential Data
When a malicious individual gains access to a system or network, confidential information like intellectual property or trade secrets are their primary target. Such intrusion has significant financial and reputational repercussions.
If not stealing confidential data, the malicious individual can destroy, encrypt, or damage it. The years of research will go in vain if the malicious individual damages or destroys confidential information. There will be catastrophic damage to an organization that will be hard to recover from.
Risk of Data Breach
A data breach can occur when a malicious individual successfully bypasses your database security and gain access to it. As a result, the safety and integrity of data is at stake. The end users of your application are affected by such a breach because their data is exposed to an unknown entity.
Moreover, the data involved in such a breach includes PII (Personally Identifiable Information) such as social security numbers, health records, financial details, etc. When the data is accessed by an unauthorized individual, they can misuse it or sell it on the dark web.
There are many drastic consequences of such data breaches, like financial loss, cyberbullying, and identity theft. The malicious individual can misuse a victim user’s identity for unlawful activities.
Risk of Defacement
Malicious individuals may not only exploit unauthorized access for sabotaging your systems but may also deface your websites. They can do it by injecting malicious code into your website, disrupting its functioning, and causing other problems.
Indirect Risks
These are the risks that occur indirectly after unauthorized access.
Legal Consequences
Unauthorized access often results in data breaches that invite several legal actions and penalties. For example, there are many data protection regulations like HIPAA, PCI DSS, and GDPR. Failing to comply with these regulations causes heavy penalties and legal implications.
Reputational Damage
Unauthorized access to your data or other digital assets will raise a question about your security mechanisms. Users will become concerned about their data, and it will melt away their trust. It will affect your organization’s reputation badly.
How to Prevent Unauthorized Access?
Preventing unauthorized access to your digital assets is critical for the security and integrity of your systems and data. However, as cyber threats become more sophisticated, securing them becomes even more challenging. You need to adopt the best security mechanism to prevent such threats.
Moreover, continuous security assessment like web app security testing helps you detect potential weaknesses that could allow unauthorized access. These measures will help you ensure that your assets and resources are accessed by only those who possess the appropriate access permissions.
Let’s find some ways that can help prevent unauthorized access to your data or systems.
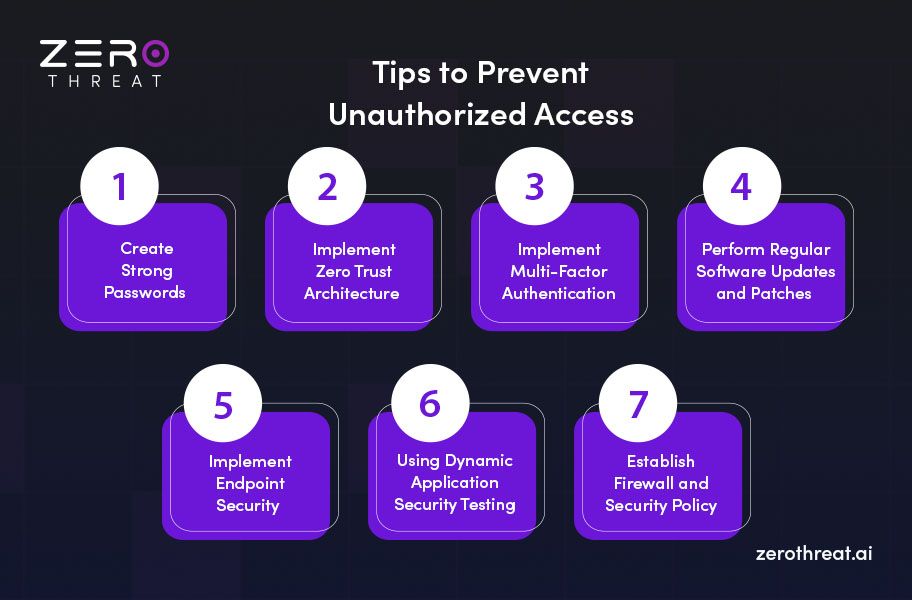
Create Strong Passwords
Often, passwords are taken for granted in organizations and predictable or default passphrases are used. This results in security breaches, allowing intruders to access sensitive data. Passwords must be strong and encrypted with a strong hash function like SHA-256. It should also not contain easily guessable information such as the user’s name, birth date, or common words.
Implement Zero Trust Architecture
Adopt a zero-trust approach when it comes to accessing digital assets and resources. This approach emphasizes the principle of “never trust, always verify.” It means trust shouldn’t be implicit in accessing digital assets and resources, instead, every interaction should be verified with authentication to grant access. It can minimize potential threats like web app security risks.
Implement Multi-Factor Authentication (MFA)
Authentication is a strong shield against unauthorized access. However, a single layer of authentication can be bypassed because of weak passwords or attacks like brute force. MFA is a powerful method to reduce the chance of unauthorized data access and keep accounts safe.
Here, you can benefit from multi-factor authentication that adds another layer of security. For example, you can use two-factor authentication in which there will be levels of authentication like with a password and code sent to a phone number or email.
Perform Regular Software Updates and Patches
Patching and updates keep your systems and applications secure by eliminating vulnerabilities. Vulnerabilities are holes in your security armor that invite breaches. They can help attackers penetrate your system.
By regularly performing software updates and managing patches, you can ensure that your systems are protected against known vulnerabilities like OWASP. This can reduce your risk of inappropriate user access.
Implement Endpoint Security
Endpoint security is a strategy that involves protecting endpoint devices on a network from unauthorized access. The endpoint devices include phones, laptops, tablets, and other devices connected to your network. These devices are quite vulnerable to access violations. They can allow a malicious individual to penetrate your network and then main systems.
In fact, endpoint security measures can include software firewalls, next-generation antivirus (NGAV), and intrusion detection systems. These consist of several policies that restrict the use of removable media, such as USB drives, which can be used to introduce malware or steal data.
Using Dynamic Application Security Testing (DAST)
DAST or Dynamic Application Security Testing is a proactive approach to prevent cyber threats like unauthorized access to web applications. DAST assesses and scans all endpoints and URIs of URL from an external viewpoint. It helps you identify vulnerabilities by mimicking real-world attacks that could expose security gaps and introduce unauthorized access, such as XSS, SQLi, and other OWASP Top 10 threats.
Establish Firewall and Security Policy
Firewalls are strong shields against cyber threats to your application or network. It will filter out bad traffic and prevent traffic from untrusted sources. Besides, you can also tighten your security policies with stricter access rules to stop unauthorized entities from accessing your assets.
Get Rid of Common Web App Security Risks and Ensure a Robust Security Posture Start Haunting
How Can ZeroThreat Help You Prevent Unauthorized Access?
Now, we know unauthorized access is not just a risk, but a ticking time bomb. Therefore, to answer the question of how to detect unauthorized access, you must get your hands on the ZeroThreat tool. As an automated penetration testing tool, ZeroThreat ensures that cyber intruders never get the chance to walk through your digital doors.
Here’s what it offers:
- Zero Trust Access Control
- MFA & Strong Credential Control
- Automated Risk Assessment & Remediation
- Seamless Integration with Your Security Stack
- Intelligent Crawler to Simulate Attacks
ZeroThreat not only helps you detect unauthorized access but also prevents it. So, don’t wait for a breach to happen. Take control of your cybersecurity today with ZeroThreat and sleep soundly, knowing your digital world is yours alone.
To Wrap Up
It’s hard to fathom the damage that a malicious individual can cause after gaining unauthorized access to your digital assets. Hence, you need to ensure optimal protection against such a threat. Security protocols, firewalls, and other measures are insufficient without continuous vulnerability assessment. It helps you identify security loopholes that could lead to compromised systems or applications.
You can automate this process with a tool like ZeroThreat. It is an advanced DAST tool that helps your web applications to avoid unauthorized access and other vulnerabilities. It helps you discover hidden weak spots in your web apps that a malicious individual may exploit to gain access to your main systems.
Try it for free to understand it and know its benefits.
Frequently Asked Questions
Why is preventing unauthorized access important?
It is crucial to make sure that your system, applications, networks, and other digital assets are not accessed by those who are not permitted. It helps to protect confidential information and critical resources from malicious use.
What would be the risk of potential unauthorized system access?
Can firewalls defend against unauthorized access?
What is the long-term damage of unauthorized access?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.



