All Blogs

Quick Summary: Security testing is vital to protect applications from cyber risks. It enables organizations to discover hidden threats and take appropriate actions to reduce risks. Organizations can identify weak spots and fix them to avoid data breaches or disruption in services. Keep reading to know more about security testing, its types, methods, and a lot more information.
Modern applications are complex and entail a wide spectrum of components. So, there is always a possibility that it might have vulnerabilities that could be a jackpot for attackers. It is crucial to detect these vulnerabilities to avoid costly data breaches that are in the millions on average today, as per IBM’s report.
Besides, these breaches also attract heavy penalties and legal actions because governments are making stricter laws to protect data. Security testing is a solution to this problem as it helps mitigate the risks by allowing organizations to evaluate applications for vulnerabilities before an attacker finds them.
Checking applications for vulnerabilities provides an opportunity to look into the attack vectors, assess the potential threat, and take prompt actions to fix them. As a result, organizations can stay abreast of attackers by identifying and remediating security weaknesses as early as possible.
Let’s understand more about security testing, its methods, and other aspects in detail.
Create a Strong Security Shield for Applications by Uncovering Hidden Weaknesses Let’s Identify Them
On This Page
- Security Testing in a Nutshell
- Different Aspects for Security Testing
- Different Types of Security Testing
- Methods for Security Testing
- How Does Security Testing Work?
- Final Thought
Security Testing in a Nutshell
In order to build hack-proof applications, you need to evaluate their security aspects to ensure they don’t have any weaknesses or loopholes. Attackers can exploit these security weaknesses or loopholes to steal data or launch APTs (Advanced Persistent Threats).
Security testing comes into the picture to identify such risks as it helps assess applications from various security aspects. So, in essence, security testing boils down to evaluating applications to discover and address inherent vulnerabilities.
Identifying and addressing security weaknesses is essential to prevent unauthorized access, malware infections, data breaches, and other security risks.
What are the Key Aspects for Security Testing?
When it comes to checking applications for security loopholes, there are different aspects that need to be evaluated. These aspects form the criteria for testing. Let’s check out the key application aspects to check for security.
Authorization
Authorization refers to the right to access specific data or resources. In other words, it defines the access role of the user to determine what kind of resources or data he/she can access after authentication. Two common methods for this include RBAC (Role-based Access Control) and ABAC (Attribute-based Access Control).
With security testing, you can evaluate the authorization aspect of an application to identify loopholes. It helps verify that the authorization policies are implemented and enforced correctly. As a result, it protects your sensitive data and resources.
Confidentiality
How do you interpret confidentiality when you hear it in real life? Obviously, you immediately recognize it to be important information or resource that only people with requisite permissions can access. It has a similar meaning in computing, where confidentiality means that only authorized users are allowed to access certain data or resources.
Web application security risks related to weak confidentiality refer to the group of vulnerabilities that result in accessing sensitive data by unauthorized parties. It leads to sensitive data exposure, where data can go into the wrong hands.
Any user can access other users' data or resources without the required permissions. For example, if an application allows users to access user information from a database without proper controls, a user can access the information even if they are not authorized to access it.
There are diverse methods, such as access controls, authentication, and encryption, that can be used to implement authentication. It ensures that only authorized users have access to respective data or resources.
Integrity
Another objective of security testing is to ensure the integrity of data and resources. This means that security controls are evaluated to ensure that data remains unaltered and accurate. The integrity checks provide in-depth insights into data’s vulnerability that can allow attackers to corrupt or tamper with it. Hence, security audits in this aspect ensure the reliability and accuracy of data.
Availability
One criterion for security testing is availability. This kind of security check ensures that any authorized user must be able to access data as and when required without any problem. It also checks for security plans or backups that can make data available to users even if there is a cybersecurity incident. Availability test in security assessment ensures that users can access data when the attacker tries to disrupt services.
Authentication
Authentication is also a crucial criterion for security testing that verifies the identity of a user. Just think of a person trying to enter a building and the guard outside asks for his/her identity card. Well, this identity card verifies that the person who owns the card has the right to enter the building.
Security auditing helps evaluate the effectiveness of access controls and login methods like passwords, biometrics, multi-factor authentication, etc. It helps identify common loopholes and verifies whether users are effectively being verified and authenticated.
Understanding the Different Types of Security Testing
There are different varieties of security testing, and each one caters to diverse needs. They help organizations uncover potential weaknesses and protect their applications and systems from cyber risks.

Penetration Testing
Penetration testing is one of the widely adopted security testing methodologies. It involves attacking applications, networks, or systems simulating an attacker’s behavior. Typically, penetration testing is performed by ethical hackers who try to hack applications, networks, or systems by overcoming security layers.
The hacker discovers vulnerabilities and tries to exploit them. If the attack becomes successful, the hacker documents them and reports all the vulnerabilities to the concerned organization. Penetration testing involves real-life attacks, and it is a manual process to discover potential security weaknesses.
Vulnerability Scanning
Identifying vulnerabilities with penetrating testing is a time-consuming and resource-intensive process. However, modern organizations follow agile-driven methodologies where frequent releases are common for applications. So, pentesting isn’t feasible in that case, as it can take many days.
Therefore, automated vulnerability scanning steps in as a solution. It is a kind of security testing that can be performed in a very short span of time, like in a few hours or a day. Automated vulnerability scanning can help discover common security risks like misconfigurations, missing security patches, authentication issues, and more. It uncovers OWASP top 10 security risks.
Application Security Testing
It is a kind of security testing approach that focuses on evaluating the security aspects of software applications. It is also referred to as AppSec and involves assessing security controls like encryption, authentication mechanisms, and more.
For example, web application security testing (WAST) involves assessing web-based applications for vulnerabilities. It involves identifying and fixing security loopholes like session management flaws, cross-site scripting, SQL injection, and more.
API Security Testing
APIs are widely used in organizations to establish seamless communication between different systems or applications. While they are quite useful, they can also become a potential entry point for hackers. Usually, organizations use a large number of APIs, and they fail to keep track of all of them, leading to vulnerabilities that hackers can exploit.
API security testing involves discovering all APIs within the digital landscape of an organization to document them and identify vulnerabilities. Additionally, it also involves identifying risky APIs like zombie or shadow APIs.
Risk Assessment
Cybersecurity risk assessment involves identifying, evaluating, and ranking cyber risks depending on their severity. This kind of security assessment helps organizations to understand threats with key information about their likelihood of occurrence, severity, and impact.
Based on an understanding of the threat, organizations can build the right plans to mitigate the risks. Hence, risk assessment is essential to build resilient security strategies.
Security Posture Assessment
Is your organization prepared for a security incident? You can answer this question with a security posture assessment. It evaluates the cybersecurity readiness of an organization by checking the implementation and effectiveness of security measures.
In other words, security posture assessment evaluates the overall security shield of an organization to determine how effective it is to identify, protect, prevent, and respond to cyber risks.
Eliminate Cyber Threats with 98.9% Accuracy and Protect Your Sensitive Data Start Now
What are the Different Security Testing Methods?
There are different methods to conduct security tests. These methods leverage various techniques to identify and report vulnerabilities. They use automated security testing tools to simplify and expedite the process. Let’s check these methods below.
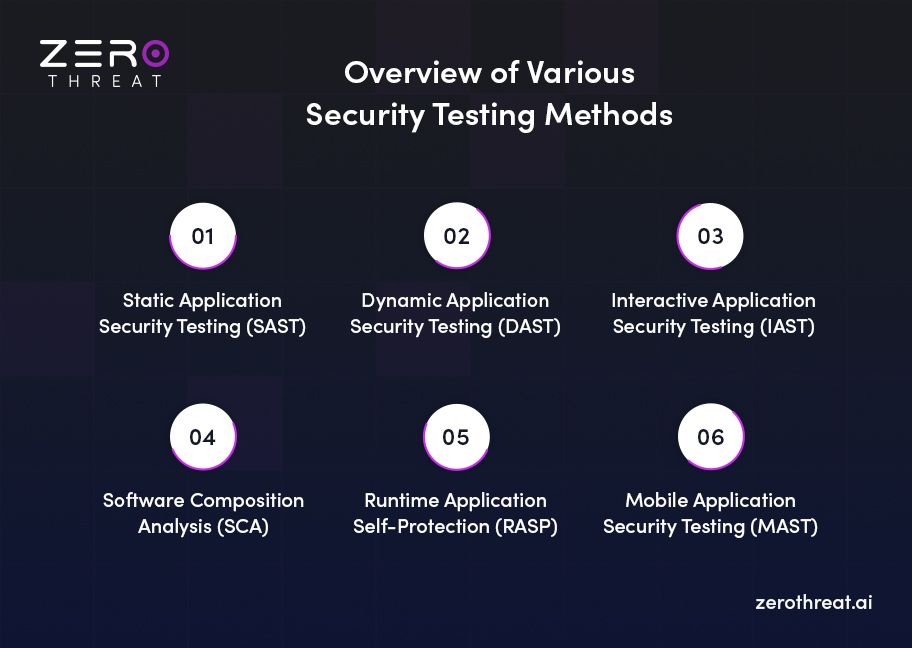
Static Application Security Testing (SAST)
This security testing method evaluates the binary or source code of a software application to uncover vulnerabilities and misconfigurations. Well, the benefit of this method is that vulnerabilities can be detected early in the software development lifecycle like coding issues or potential security weaknesses that can be exploited when an application is launched in production. SAST tools can be integrated into code editors to detect security-related bugs while coding.
Dynamic Application Security Testing (DAST)
DAST is a security testing method that helps discover and report vulnerabilities in applications when they are run, or code is executed. Usually, applications are tested at the staging environment with this method by performing automated simulated attacks. A DAST tool will analyze applications in the running state to identify security issues that occur only when the application is live.
Interactive Application Security Testing (IAST)
IAST results in the convergence of SAST and DAST. It means IAST offers the benefits of both these security methods. So, in this method, applications are monitored when they run, and the code is analyzed in real-time while it is being executed. This method offers more accurate results of security analysis because it involves observing an application’s behavior at runtime while also having access to internal implementation.
Software Composition Analysis (SCA)
This method analyzes the components and libraries of software applications to identify known vulnerabilities. Today, most applications rely on third-party components and codes that could come with unwarranted threats. Plus, there is a possibility of supply chain attacks. SCA helps discover vulnerabilities and helps organizations ensure they are secure and up to date.
Runtime Application Self-Protection (RASP)
RASP offers real-time monitoring of applications to dynamically detect and eliminate potential security risks. This method integrates security into an application, providing dynamic protection against emerging threats. It detects suspicious behavior in applications while they are executing. Hence, RASP is capable of detecting threats in real-time.
Mobile Application Security Testing (MAST)
It provides tools and methods to test mobile-based applications. With this method, mobile apps are evaluated to identify common security weaknesses. It helps identify different types of security issues in mobile apps, including application permissions, network communication, and more. MAST helps protect apps against security issues such as unauthorized access to critical data.
How Does Security Testing Work?
There are several steps in a typical security testing process. It offers a structured approach to identify and address security vulnerabilities. Let’s check out all the steps in security testing.
Plan and Gather Information
Firstly, you need to define the scope of security testing. For this, start by identifying the systems, applications, or components that need to be tested. Further, define the kinds of testing you need to perform, such as pen testing or automated vulnerability scanning. Finally, define the objectives of the test.
Identify the Potential Risks
You need to identify the potential risks as well as understand your attack surface, possible threat vectors, and vulnerable areas. Here, you need threat modeling to discover potential risks to your organization and make a prudent cybersecurity strategy.
Create Test Cases
The next step is to create test cases for performing simulated attacks. These test cases are designed considering the information collected about the potential risks and attack surface. Every test case should have a clear objective, expected outcome, success criteria, and other information.
Execute Security Tests
Once the test cases have been designed, the next steps involve executing the tests accordingly. Perform security testing like penetration testing or vulnerability scanning with tools like DAST or SAST. Document and report any security weaknesses detected.
Analyze the Security Weaknesses
Next, you need to analyze the test results to evaluate the impact and severity of each vulnerability. All vulnerabilities must be documented and prioritized based on their severity and impact. The document will be a reference to address and mitigate the security risks.
Fix Vulnerabilities
After the findings, the security team and developers work together to address the identified vulnerabilities. There could be various methods to fix vulnerabilities, including adding new security controls, patching software, and reconfiguring systems.
Perform Re-tests for Validation
After all the vulnerabilities have been addressed, you need to perform re-tests to validate them. The re-testing ensures that the vulnerabilities have been eliminated effectively, and it also finds any issues that persist.
Continuous Testing
Security testing isn’t a one-time task; it is a continuous process. Since cyber threats keep evolving and increasing, continuous testing helps identify and address them before they pose a critical challenge for organizations.
Scan in Minutes and Detect Thousands of CVEs Precisely to Mitigate Cyber Risks Perform a Scan
Final Thought
Cyber risks are evolving gradually posing new kinds of challenges for applications. Hence, applications require constant auditing to check for security loopholes that arise over time and protect them against potential cyber threats.
ZeroThreat – a robust API security testing tool is useful in this process as it helps discover and address various vulnerabilities. Equipped with AI-powered DAST capabilities, ZeroThreat can detect vulnerabilities with pinpoint accuracy, even if they require OAST.
It is a cutting-edge tool for automated vulnerability scanning that can be integrated into SDLC to actively detect and remediate vulnerabilities in the staging environment. Get a full overview of this tool to know more about its benefits.
Frequently Asked Questions
What are the different security testing best practices?
The following are the key best practices to follow for quality testing:
- Integrate security testing into SDLC with a shift-left approach.
- Test application for security on various stages of SDLC.
- Conduct a comprehensive risk assessment by evaluating threats and their impact.
- Analyze and monitor security metrics.
- Update and maintain security measures regularly.
What are the key benefits of security testing?
Is security testing performed automatically or manually?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


