All Blogs
Healthcare Penetration Testing Best Practices for Cybersecurity and Compliance

Blog Overview: Healthcare faces rising ransomware threats, costly breaches, and strict compliance demands. This blog explores penetration testing best practices to help providers strengthen defenses, minimize downtime, and safeguard patient data with continuous, safety-focused security testing.
Healthcare is the most expensive industry in which to suffer a data breach, and it’s getting more complex to secure. Electronic Health Records (EHRs), telemedicine platforms, medical IoT devices, and cloud-based health applications have revolutionized patient care but have expanded the attack surface for cybercriminals.
In the first quarter alone, over 650 security incidents exposed the data of more than 32 million people, marking 2025 as one of the most challenging years for healthcare cybersecurity. With the average healthcare data breach costing $11.45 million per incident, the highest across any industry, healthcare faces unparalleled urgency to identify and mitigate cyber risks through robust penetration testing.
A well-run penetration testing is one of the most effective methods hospitals, payers, and digital healthcare companies can proactively reduce risk without slowing care.
A pentesting in healthcare industry is a mission-critical exercise, directly protecting patient data and complex digital infrastructures. As per the latest statistics, 19% of global penetration testing investment comes from healthcare, reflecting growing digitization, ransomware attacks, and increased regulatory demands.
This blog explores the best penetration testing practices for healthcare industry. Backed by research, real-world data, and expert recommendations, we will guide healthcare IT professionals, compliance officers, and security teams on how to conduct effective, compliant, and actionable penetration tests that protect both data and patient trust.
Why risk being the weak link? Let’s talk about securing your apps before attackers find you. Secure My Business Now
On This Page
- Why Penetration Testing is Non-Negotiable in Healthcare
- Key Regulatory Drivers: HIPAA, HITRUST, and Beyond
- Best Penetration Testing Practices for Healthcare
- Case Study
- The Road Ahead: Building a Continuous Pen Testing Culture
- Healthcare Penetration Testing: The Shield to Protect Data
- Role of ZeroThreat
- Final Thoughts
Why Penetration Testing is Non-Negotiable in Healthcare
With the high value of protected health information (PHI) on the dark web, healthcare organizations have become the prime targets for cyberattacks. A single patient record can fetch up to $1,000, compared to $5 for a credit card number, according to the report.
The recent statistics unveil the real picture:
- 70% of healthcare organizations experienced a ransomware attack in 2022 (Sophos State of Ransomware in Healthcare 2023).
- The healthcare sector accounted for 45% of all reported data breaches in the U.S. in 2023.
- Medical devices are now a top attack vector, with over 1.8 million vulnerable devices connected to hospital networks.
Pen testing in cybersecurity is the ethical method of simulating real-world cyberattacks to identify vulnerabilities before malicious actors can exploit them. Unlike automated vulnerability scans, pentesting involves human expertise, context-aware analysis, and adversarial thinking, which make it indispensable for healthcare environments where lives and data are on the line.
Key Regulatory Drivers: HIPAA, HITRUST, and Beyond
Before implementing penetration testing best practices in healthcare, we must understand the compliance requirements that healthcare organizations must comply with.
- HIPAA Security Rule: While not explicitly mandating pen testing, it requires regular risk assessments and implementation of security measures to protect ePHI. Penetration testing is a critical component of comprehensive risk analysis for health data protection.
- HITRUST CSF: This framework explicitly requires annual penetration testing as part of its control requirements (Control 10.4).
- NIST SP 800-53 Rev.5: Recommends penetration testing under RA-5 (Vulnerability Scanner) and CA-8 (Penetration Testing).
- FDA Guidance for Medical Devices: Encourages manufacturers to conduct security testing, including pen testing, throughout the device lifecycle.
Failure to comply can result in fines, reputational damage, and loss of patient trust. In 2023, HHS’s Office for Civil Rights (OCR) levied over $20 million in HIPAA fines, many tied to inadequate security testing.
Best Penetration Testing Practices for Healthcare
To maximize effectiveness, ensure compliance, and drive real value, healthcare CIOs, CISOs, and other executives should adopt these research-backed healthcare cybersecurity best practices as a strategic approach to strengthen their testing initiatives.
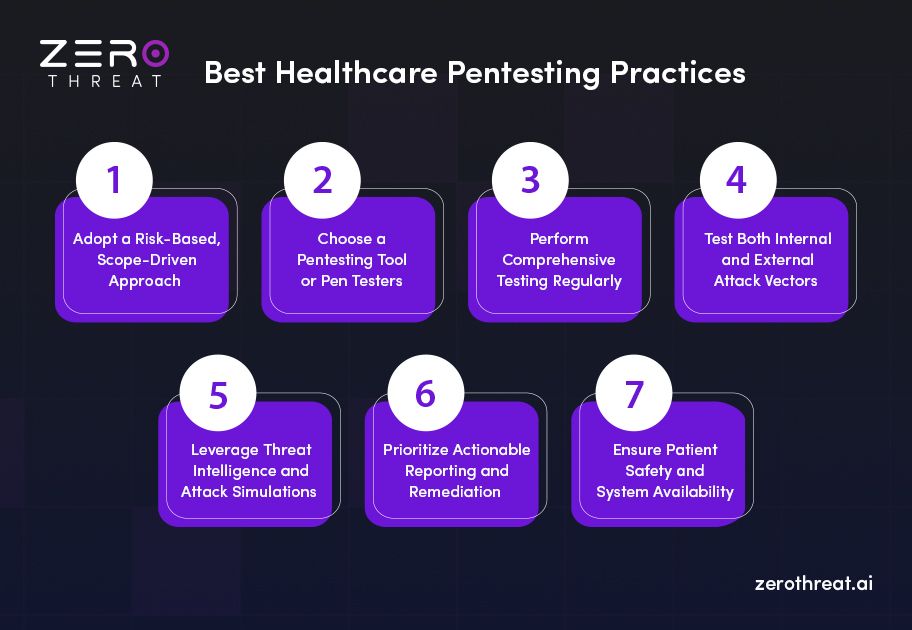
1) Adopt a Risk-Based, Scope-Driven Approach
When implementing the best practices for healthcare penetration testing, you should know that not all systems are equally critical. A strategic pen test should prioritize high-risk assets:
- EHR systems
- Patient portals and telehealth platforms
- Networked medical devices (MRI machines, infusion pumps)
- Cloud environments (AWS, Azure) hosting PHI
- Legacy systems still in use (often overlooked but highly vulnerable)
A study by the Ponemon Institute found that 68% of healthcare breaches originated from unpatched systems or misconfigured cloud services, both of which are detectable through targeted pen testing.
Best Practices: Conduct a vulnerability assessment to identify critical assets, then define the scope of testing based on data sensitivity, system criticality, and regulatory exposure.
2) Choose an Automated Pentesting Tool or Certified Pen Testers
Not all penetration testers are equipped to handle the nuances of healthcare environments. For example, medical devices often run on outdated OS and cannot tolerate aggressive scanning.
Best Practice: Choose an automated pentesting tool or hire pen testing firms with:
- Certifications like OSCP, CREST, or CISSP
- Experience in healthcare-specific regulations (HIPAA, HITRUST)
- Knowledge of medical device security standards (e.g., IEC 62304, UL 2900)
- Use of non-disruptive testing techniques to avoid impacting clinical operations
The FDA recommends that pen testers use “safe and top pentesting methodologies” to prevent device malfunction during assessments.
3) Perform Comprehensive Testing Regularly
If you perform pentesting annually, it may meet compliance requirements, but it is insufficient in today’s evolving threat landscape. Systems evolve, new devices are added, and vulnerabilities emerge daily.
Best Practices:
- Perform annual penetration tests as a baseline.
- Conduct bi-annual or quarterly tests for high-risk systems.
- Perform ad-hoc tests after major changes (e.g., system upgrades, mergers, new device deployments).
A report found that organizations that conduct quarterly pen tests experience breach rates of 53% lower than those that test annually or less ess frequently.
4) Test Both Internal and External Attack Vectors
Many security threats in healthcare applications originate from within the network, whether through phishing, insider threats, or compromised credentials.
Best Practice:
- External Pen Testing: Simulates attacks from outside the network (e.g., internet-facing portals, APIs).
- Internal Pen Testing: Assesses what an attacker could do if they gained access (e.g., via a phishing email).
- Wireless and Physical Testing: Evaluate Wi-Fi security and physical access points (e.g., unattended workstations in clinics).
Ensure HIPAA, PCI, and ISO compliance before gaps cost you fines or breaches. Ask Us How
5) Leverage Threat Intelligence and Real-World Attack Simulations
Effective pentesting goes beyond checking boxes. It should simulate real-world attack scenarios based on current threat intelligence.
Best Practice:
- Use frameworks like MITRE ATT&CK for Healthcare to model adversary behavior.
- Simulate ransomware attack paths, lateral movement, and data exfiltration.
- Test incident response capabilities during the engagement.
For example, simulating a Conti-style ransomware attack can reveal gaps in backup integrity, network segmentation, and detection capabilities.
6) Prioritize Actionable Reporting and Remediation
A pentest is only as valuable as the actions it drives. Vague reports with numerous low-severity findings can overwhelm teams and delay fixes.
Best Practices:
- Deliver executive summaries for leadership and technical reports for IT teams.
- Rank vulnerabilities by risk score (CVSS) and business impact.
- Provide clear remediation steps and retesting options.
- Integrate findings into the organization’s vulnerability management lifecycle.
As per the SANS Institute survey, organizations that re-tested within 30 days of remediation reduced residual risk by 75%.
7) Ensure Patient Safety and System Availability
Unlike other industries, healthcare pen testing must balance security with patient safety. A misstep could disrupt life-saving equipment.
Best Practice:
- Obtain clinical oversight approval before testing medical devices.
- Use passive scanning techniques where possible.
- Schedule tests during low-usage periods (e.g., weekends, nights).
- Establish a rollback plan in case of unexpected impacts.
The Joint Commission now includes cybersecurity in its hospital accreditation standards, emphasizing the need for safe testing practices.
Case Study: How a Regional Health System Avoided a Breach
In 2022, a 15-hospital health system in the Midwest conducted a comprehensive pen test that uncovered a critical flaw: an unpatched vulnerability in their patient portal that allowed SQL injection. Attackers could have accessed over 2 million patient records.
Thanks to the pen test, the team patched the vulnerability, implemented a Web Application Firewall (WAF), and revised their change management process. Six months later, an attempted breach using the same exploit failed—proving the value of proactive testing.
The Road Ahead: Building a Continuous Pen Testing Culture
Penetration testing should not be a one-off compliance exercise. Leading healthcare organizations are adopting continuous penetration testing models, integrating automated red teaming tools, and embedding security into DevOps (DevSecOps) pipelines.
Emerging trends include:
- AI-powered pen testing tools that simulate advanced persistent threats (APTs).
- Bug bounty programs for healthcare apps.
- Collaborative testing with medical device manufacturers.
As healthcare becomes more interconnected—with AI diagnostics, remote monitoring, and genomic data—the need for rigorous, intelligent, and frequent pen testing will only grow.
Healthcare Penetration Testing: The Shield to Protect Data
Penetration testing in healthcare benefits hospitals, clinics, dental practices, behavioral health providers, and other covered entities in multiple critical ways:
Safeguarding Sensitive Patient Data
Penetration testing identifies weak points in healthcare applications, networks, and databases where patient records could be exposed. By simulating real-world cyberattacks, it ensures protected health information (PHI) remains confidential, reducing the risk of costly breaches that compromise both patient trust and compliance with regulations.
Meeting Compliance Requirements
Healthcare providers must comply with strict regulations like HIPAA, GDPR, and HITECH. Penetration testing helps uncover compliance gaps, ensuring systems meet legal standards. Regular testing demonstrates due diligence, protects organizations from penalties, and strengthens their ability to withstand audits with evidence-based security practices.
Preventing Financial Loss
A single healthcare data breach can cost millions in fines, legal liabilities, and reputational damage. Penetration testing proactively reduces these risks by exposing vulnerabilities before attackers can exploit them. This preventive measure saves costs while preserving the credibility and stability of healthcare organizations.
Enhancing Patient Trust
Patients trust healthcare providers with their most personal information. Penetration testing strengthens security frameworks, ensuring that privacy is never compromised. Demonstrating commitment to cybersecurity reassures patients that their data is safe, ultimately improving loyalty, reputation, and long-term patient relationships.
Supporting Digital Transformation
With telemedicine, cloud-based EHRs, and mobile health apps rising, healthcare systems are more connected—and more vulnerable—than ever. Penetration testing ensures these digital innovations remain secure by validating security controls and minimizing risks, enabling healthcare organizations to embrace transformation without compromising safety.
Teams like yours are already cutting false positives by 90%. Don’t be left behind. See In Action Today
The Role of ZeroThreat in Implementing Best Healthcare Cybersecurity Practices
As an automated pentesting tool, ZeroThreat plays a vital role in implementing best cybersecurity practices, helping healthcare organizations safeguard patient data, meet compliance standards, detect vulnerabilities faster, and maintain trust while reducing risks from evolving cyber threats.
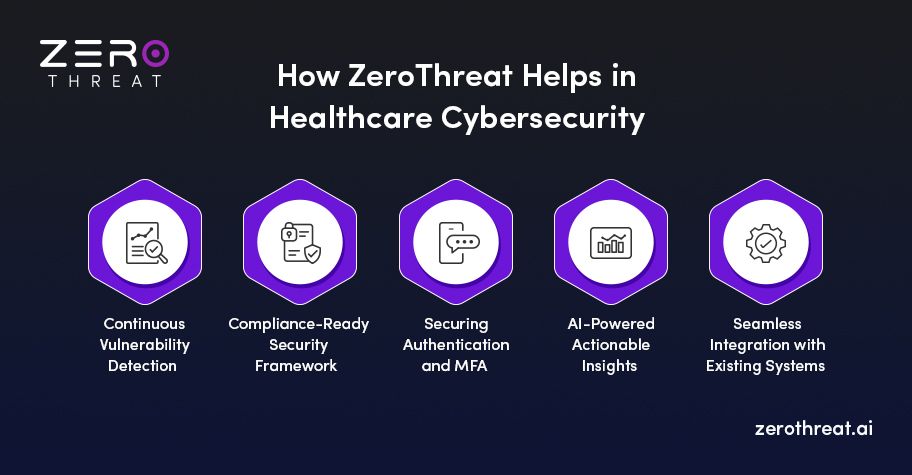
Continuous Vulnerability Detection
ZeroThreat scans healthcare applications, APIs, and systems to detect vulnerabilities before attackers exploit them. This proactive approach helps organizations stay ahead of emerging threats while ensuring patient records, diagnostic tools, and connected devices remain protected without disrupting critical medical operations.
Compliance-Ready Security Framework
Meeting strict regulations like HIPAA, GDPR, and ISO is easier with ZeroThreat. Its evidence-based reporting aligns with industry standards, giving CIOs and CISOs clear visibility into compliance gaps and actionable steps to resolve them. This ensures healthcare providers meet security audits with confidence and precision.
Securing Authentication & MFA
Many healthcare breaches stem from weak authentication. ZeroThreat supports MFA and advanced identity testing, ensuring that sensitive systems are protected behind strong authentication layers. This minimizes unauthorized access to patient data and strengthens trust in digital health applications.
AI-Powered Actionable Insights
ZeroThreat doesn’t just find vulnerabilities—it provides AI-driven remediation guidance tailored for healthcare IT teams. This reduces manual effort, speeds up fixes, and ensures that cybersecurity measures are practical for environments where downtime can impact patient care.
Seamless Integration with Existing Systems
Healthcare relies on legacy and modern systems working together. ZeroThreat integrates smoothly into existing EHRs, patient portals, and connected medical devices, ensuring robust protection without costly reconfiguration. This compatibility helps teams focus on care delivery instead of IT roadblocks.
Thinking of upgrading your security testing? Sign up for FREE with ZeroThreat now. It helps healthcare providers detect vulnerabilities 10x faster while ensuring HIPAA and ISO compliance effortlessly.
Final Thoughts
Cybersecurity in healthcare is not just about protecting data—it’s about protecting lives. Penetration testing is a powerful tool that, when done right, can prevent breaches, ensure compliance, and uphold the trust patients place in their providers.
By following these best practices—grounded in data, regulation, and real-world experience—healthcare organizations can turn pen testing from a checkbox into a strategic advantage.
Remember one thing. The goal isn’t just to find vulnerabilities. It’s to fix them before they cost millions, disrupt care, or endanger lives.
Frequently Asked Questions
What is the role of cybersecurity in healthcare?
Cybersecurity in healthcare protects sensitive patient data, ensures system availability, and maintains compliance with regulations like HIPAA. It protects against ransomware, breaches, and unauthorized access, ensuring patient safety and trust while preventing costly disruptions to healthcare operations.
What are common vulnerabilities in healthcare systems?
How often should you perform penetration testing in healthcare industry?
How does automated healthcare pentesting differ from manual testing?
What are common mistakes to avoid in healthcare pentesting?
What type of healthcare systems should be included in a pentest?
Is healthcare penetration testing required for HIPAA compliance?
What should be included in a healthcare pentesting report?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


