All Blogs
The State of Penetration Testing 2025: What the Numbers Reveal

Quick Overview: This blog provides a comprehensive look at penetration testing statistics for 2025, covering adoption trends, common vulnerabilities, ROI, and regulatory drivers. It highlights how organizations are using pentesting to strengthen security postures, reduce breach risks, and adapt to evolving threats through automation, cloud testing, and continuous security assessments.
If there’s one lesson years in AppSec have taught us, it’s this: never make assumptions without context. And always rely on data you can trust.
With that mindset, we’ve compiled this comprehensive list of penetration testing statistics to give you clear, data-backed insight into the state of the industry.
Penetration testing provides organizations with a controlled way to simulate real-world attacks, helping them identify vulnerabilities before threat actors can exploit them.
Recent shifts—like the rise of AI-driven attacks, expansion of cloud infrastructure, stricter compliance mandates, and increasing costs of data breaches—have made penetration testing not just a best practice, but a necessity. As per data, 73% of successful perimeter breaches were achieved using vulnerable web applications.
But why are we creating a comprehensive report of penetration testing statistics? Because this stats and data empower AppSec experts like you to stay informed at a strategic level—while also supporting critical initiatives such as:
- Making a strong case for increased security budgets
- Justifying the need to hire talent for key capability gaps
- Demonstrating the business value of your team’s tools, workflows, and risk mitigation efforts
Explore these in-depth (and sometimes unexpected) penetration testing stats to uncover current industry trends and see how they directly affect your daily security operations.
Implement Advanced AI-powered Pen Testing into Your DevSecOps Workflow to Discover and Fix Issues Check Out Our Plans
On This Page
- Top Penetration Testing Statistics: An Overview
- Penetration Testing Statistics for 2025
- Vulnerability Statistics Relevant to Pentesting
- Why Organizations Conduct Penetration Tests
- Pentesting Jobs and Salaries Statistics
- Industry Adoption of Penetration Testing
- Types of Pentesting in 2025
- Tools & Technologies Used in Penetration Testing
- Effectiveness of Penetration Testing in Breach Prevention
- Regulatory Compliance and Pen Testing
- Future Trends in Penetration Testing
- Conclusion
Top Penetration Testing Statistics: An Overview
- As of Q1 2025, the global penetration testing market size is estimated at USD 2.34 billion, with a projected compound annual growth rate (CAGR) of 18.7% over the next five years. This rapid growth is driven by increasing regulatory mandates, rising ransomware incidents, and the adoption of cloud-based infrastructure.
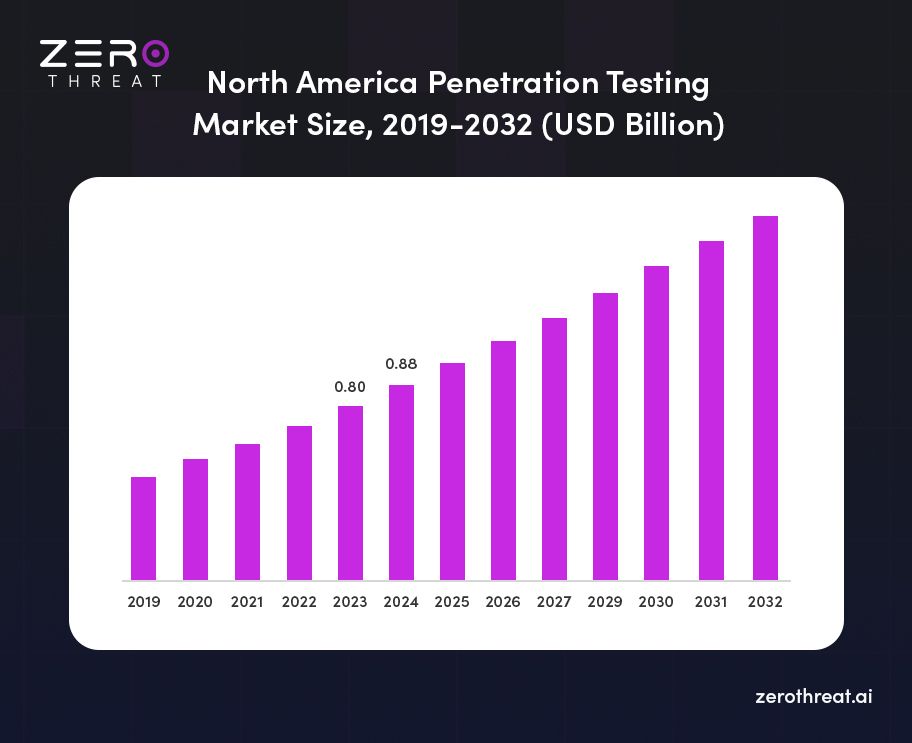
- The global penetration testing market was valued at USD 2.45 billion in 2024. The market is projected to grow from USD 2.74 billion in 2025 and reach USD 6.25 billion by 2032, exhibiting a CAGR of 12.5% during the forecast period.
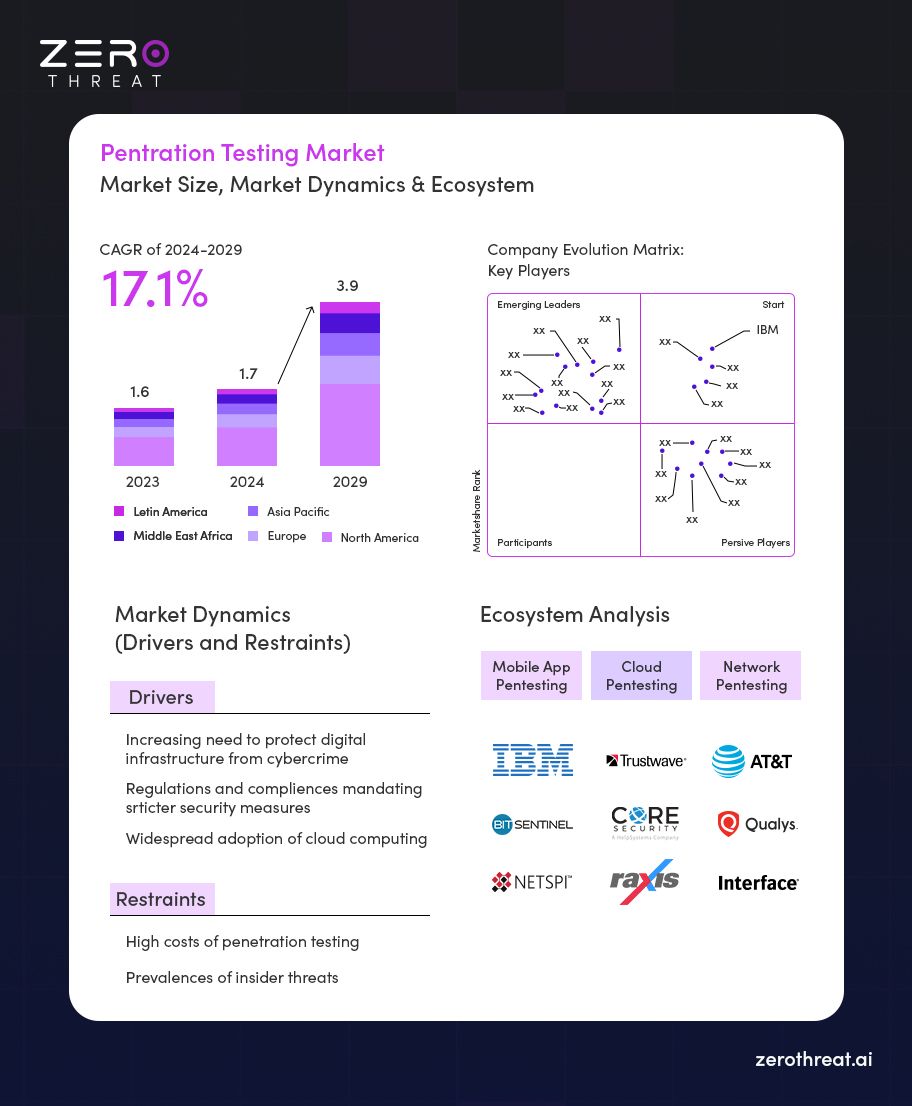
- The global penetration testing market is estimated to be worth USD 1.7 billion in 2024 and is projected to reach USD 3.9 billion by 2029 at a CAGR of 17.1% during the forecast period.
- 32% of organizations perform penetration tests annually or bi-annually, with 51% outsourcing to third-party specialists.
- Among large organizations, 28% conduct pentests quarterly, compared to 13% among smaller ones.
- U.S. enterprises spend an average of $187,000 annually on penetration testing, accounting for approximately 10.5% of their total IT security budgets.
- 55% of enterprises now leverage software-based tools to support their in-house penetration testing programs.
- 50% of CISOs identify software-based testing as their primary method for detecting exploitable security gaps within their IT environments.
- In the U.S., 59% of enterprises have implemented at least one cybersecurity solution due to requirements from their cyber insurance provider.
- 67% of U.S. enterprises reported experiencing a security breach within the past 24 months.
- Of those affected, 76% reported a direct impact on the confidentiality, integrity, or availability (CIA) of their data.
- According to Cybersecurity Ventures, the global market for penetration testing tools and services is projected to surpass $5 billion annually by 2031, based on aggregated forecasts from various industry analysts.
- 92% of U.S. and European organizations increased their overall cybersecurity budgets last year, with 85% specifically boosting their spending on penetration testing. Meanwhile, other projections suggest the global pentesting market could see over 24% growth by 2026.
- Despite this momentum, many organizations still skip annual penetration tests. One major barrier is cost—1 in 3 companies cite budget constraints as a key reason for limited testing.
- The cost of penetration testing varies widely, ranging from a few hundred dollars for basic assessments to over $100,000 for complex engagements. On average, a typical penetration test costs around $18,300 per organization.
- According to Mitnick Consulting, a comprehensive penetration test typically lasts 3 to 5 weeks, but in some cases, it can extend to several months.
- The U.S. Bureau of Labor Statistics (BLS) projects a 35% growth in jobs for information security analysts, including penetration testers, between 2021 and 2031—much faster than the national average for all occupations.
- Gartner estimates that the penetration testing industry will reach $4.5 billion by 2025, highlighting its rapid adoption across sectors.
- A Ponemon Institute study reveals that 1 in 5 companies do not test their software for security vulnerabilities—leaving them open to avoidable risks.
- The global network security market is expected to grow at a 12% CAGR from 2021 through 2028, reflecting increased cybersecurity investments.
- 76% of cybersecurity professionals globally agree that cyberattacks have surged due to the rise in remote work.
- Check Point Software reports that 81% of organizations adopted remote work, and 74% plan to maintain remote operations indefinitely.
- A Kaspersky report finds that 40% of companies admit they lack adequate cybersecurity infrastructure.
- 80% of senior IT and security leaders believe their organizations are underprepared for cyberattacks, and 77% lack a formal incident response plan.
- 93% of healthcare organizations have suffered at least one data breach in the past three years, underscoring their vulnerability.
- According to the (ISC)² 2021 Cyber Workforce Report, the global cybersecurity workforce needs to grow by 65% to effectively safeguard critical infrastructure.
- In Canada, 45% of organizations conduct regular penetration tests to identify threats and prevent cybercrime.
Stay One Step Ahead of Hackers by Proactively Identifying and Addressing Critical Vulnerabilities Early Get Started Now
Penetration Testing Statistics for 2025
Organizations everywhere are feeling the impact of an expanding threat landscape on their critical assets.
As per CVE details, by 2025 June, there are over 22,000 published CVE data registered.
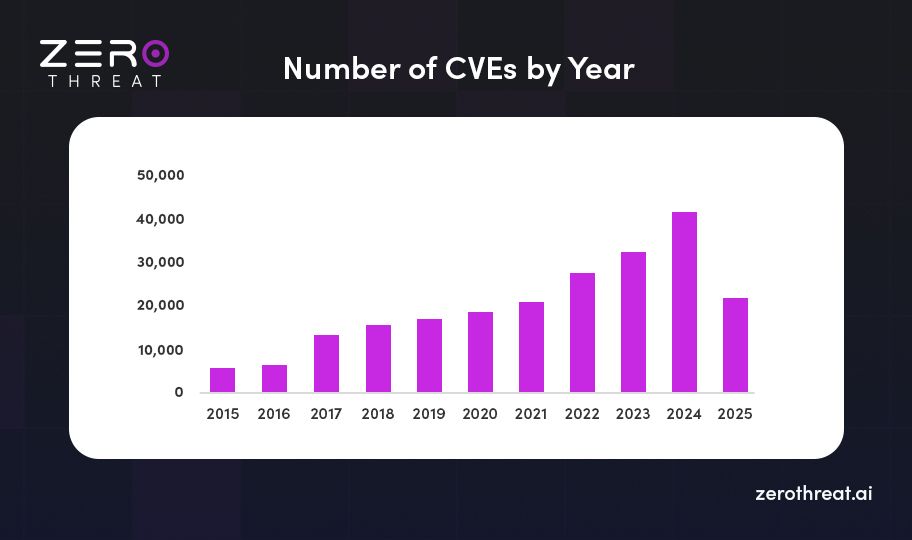
- North America remains the largest contributor to the pen testing market, accounting for 39% of global spending.
- Asia-Pacific is the fastest-growing region, with a CAGR of 22.4%, largely due to increased digitization and cybersecurity investments in countries like India, Japan, and South Korea.
- Europe follows closely behind North America, with strong demand driven by GDPR compliance and the EU’s NIS2 Directive.
- 29% of organizations have automated at least 70% of their security testing processes.
- The penetration testing market is projected to grow at a compound annual growth rate (CAGR) of 13.7% between 2022 and 2027.
- A Kaspersky Lab report states that over 40% of companies do not have adequate cybersecurity measures in place.
- The same report highlights that 73% of successful breaches in the business sector occurred due to exploited vulnerabilities in web applications.
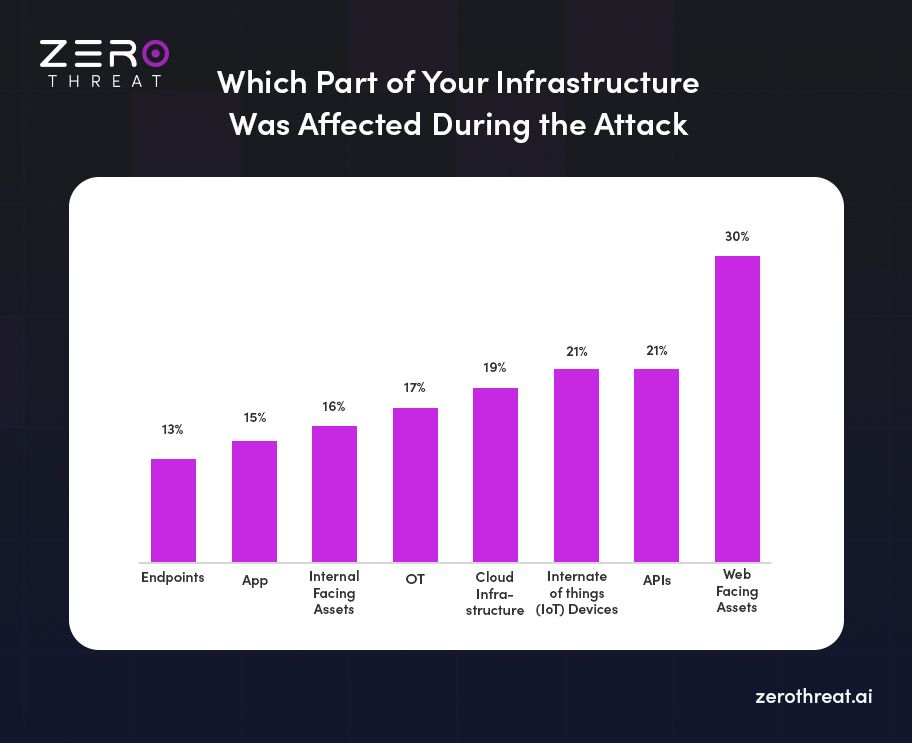
- Applications and networks remain the most common points of entry for attackers, with applications accounting for 35% of breaches and networks for 21%.
- According to Netwrix’s 2022 vulnerability assessment analysis, 52% of organizations are planning to switch to a new assessment solution to reduce the number of false positives in their vulnerability scans.
- The average cost of a data breach in 2025 stood at $4.44 million, while the cost in the United States reached a record high of $10.22 million.
- U.S.-based breaches cost the most, averaging $9.36 million, followed by the Middle East at $8.75 million
- Breaches caused by stolen or compromised credentials cost an average of $4.81 million, while malicious insider incidents averaged $4.99 million.
- 6% of organizations emphasize API penetration testing before deployment.
- 75% of infosec firms perform pentests to meet compliance regulations.
- The global Penetration Testing market is projected to reach US $1.86 billion in 2025.
- In 2025, nearly eight-in-ten (78%) organizations report plans to increase cybersecurity investment, reflecting how cyber risk remains a top priority.
- 69% of companies consider detailed reporting the most important feature in a paid penetration testing solution, followed by multi-vector testing (64%) and automation of redundant tasks (58%).
- Vulnerability scans are capable of identifying over 50,000 internal and external weaknesses.
- The top three areas targeted during penetration tests are servers, web application pen tests, and databases.
- The same survey found that just 44% of companies have embedded security tests and reviews into their coding workflows.
- While 66% of organizations have automated test builds, only 52% apply continuous integration (CI) and automated security testing.
- The mobile penetration testing segment in the U.S., Canada, Japan, China, and Europe is expected to grow at a CAGR of 20.7%.
- Penetration testing in the public sector is forecasted to further fuel industry growth by 2028, according to Digital Journal.
- Employment in the computer and IT sector is expected to grow by 13% from 2020 to 2030, reflecting the increasing demand for cybersecurity expertise.
- Among U.S. job postings for penetration testers, 71% require a bachelor’s degree, while only 20% ask for a graduate degree.
- According to the CoreSecurity Penetration Testing Report:
- 70% of companies conduct penetration tests to support their vulnerability management programs.
- 69% use them to assess their overall security posture.
- 67% rely on them for compliance purposes.
- 32% of organizations conduct penetration tests on an annual or bi-annual basis.
- 51% of businesses rely exclusively on third-party penetration testing teams.
- 42% of organizations have developed in-house penetration testing teams.
- The average time it takes for attackers to penetrate a local network is just four days.
- In 77% of external pentesting cases, the primary vector involved poorly protected web applications.
- 86% of companies had at least one exploitable web application vector, highlighting a widespread vulnerability.
- Common penetration methods include brute-forcing credentials, affecting:
- Database management systems (15%)
- Remote access services (6%)
- Internal penetration tests across 23 organizations resulted in complete system takeovers within three days.
- In 61% of organizations, attackers were able to gain control using just one simple vulnerability.
- 47% of pentesting attacks go undetected, often blending in with normal user or admin activity.
- According to BusinessWire, the global penetration testing software market will grow from $1.41 billion in 2021 to $4.05 billion by 2028, with a CAGR of 14.4%.
- 75% of infosec firms perform penetration testing primarily to ensure compliance.
- 71% of surveyed companies stated that pentesting is critical for their compliance initiatives, while only 4% said it’s not important.
- 58% of infosec professionals reported using third-party pentesting services to meet compliance standards.
Vulnerability Statistics Relevant to Pentesting
- Approximately 69% of all known vulnerabilities are linked to CVEs with a network-based attack vector, making remote exploitation a primary concern.
- The oldest vulnerability reported in 2020 was CVE-1999-0517, a security flaw that had existed for over 21 years before being rediscovered.
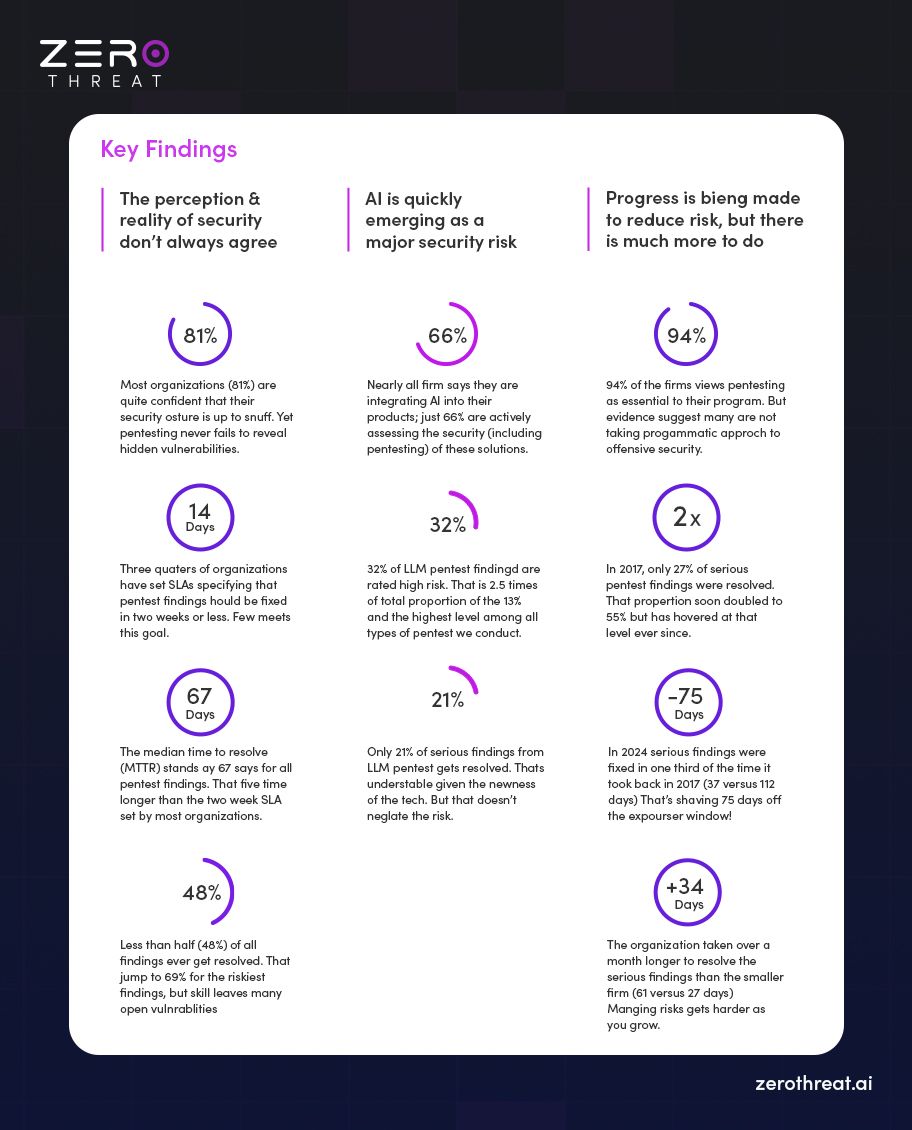
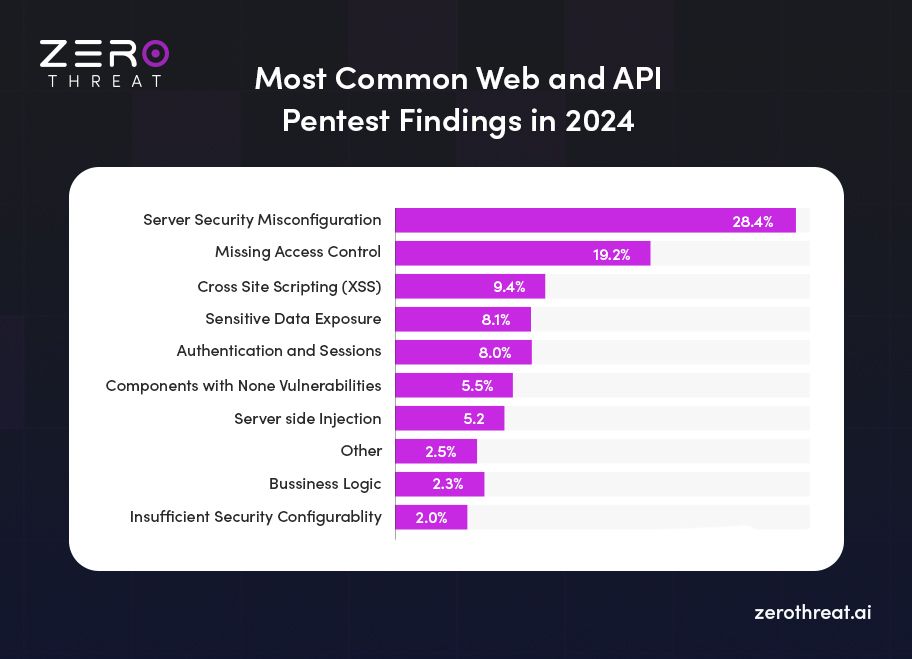
- Most common web and API pentest findings in 2024 is server security misconfiguration with 28.4%.
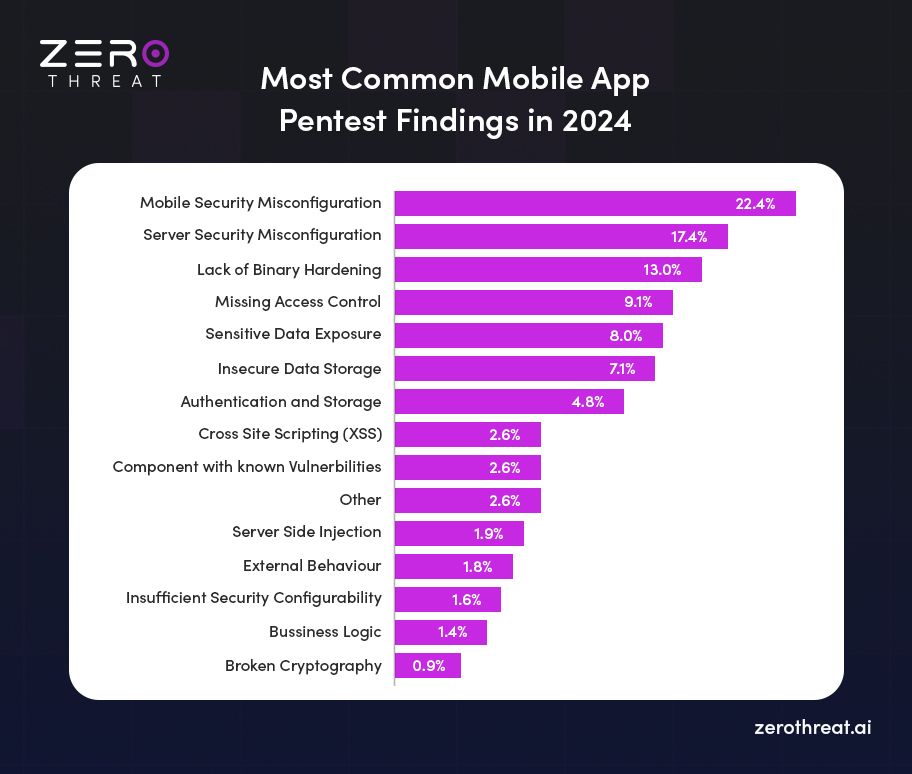
- Most common mobile application pentest findings in 2024 is mobile server misconfiguration with 22.4%.
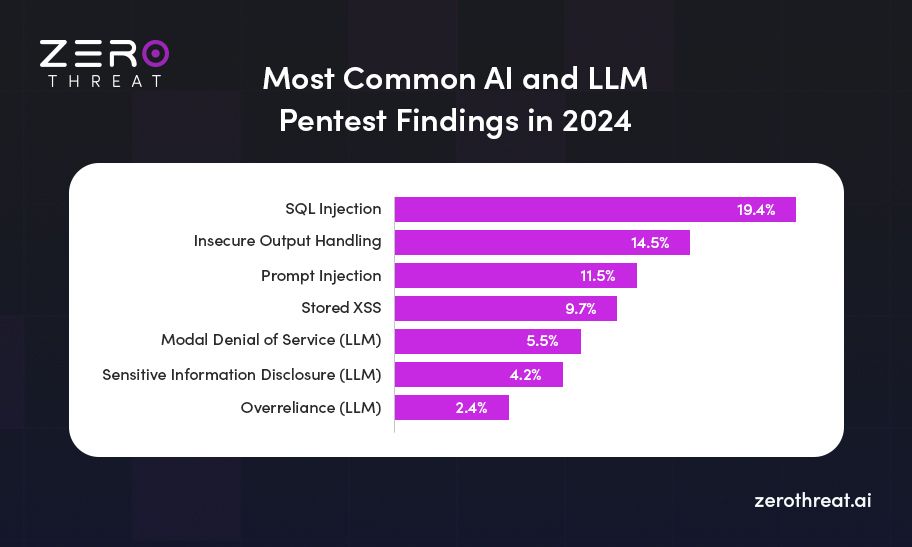
- Most common AI and LLM pentest findings in 2024 is SQL injection with 19.4%.
- 32% of the findings uncovered during AI and LLM pentests warrant a serious rating.
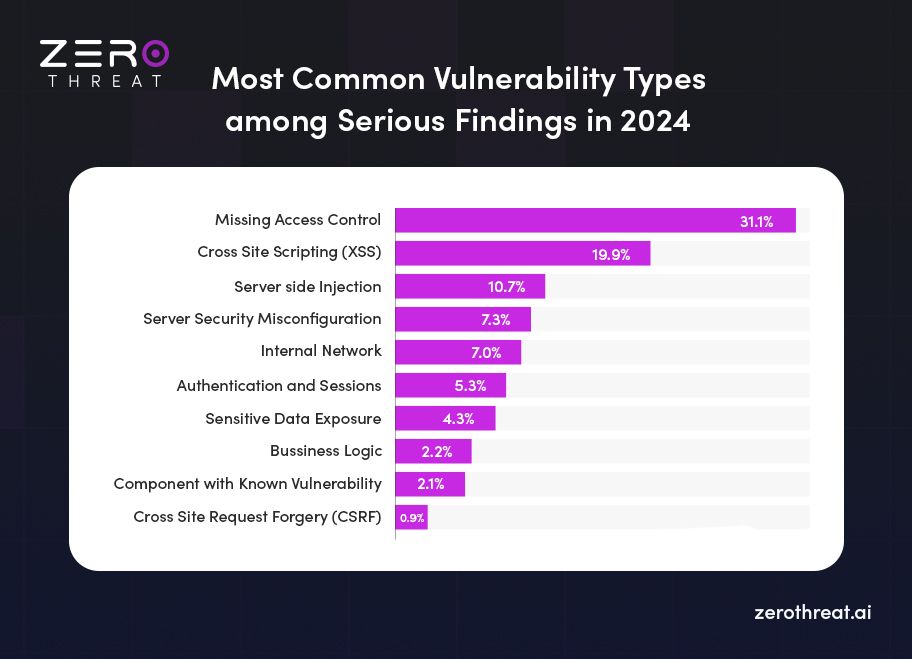
- Missing access control is the most common vulnerability type among serious findings with 31.1%.
Find Out Hidden Gaps in Your Security Posture Most Accurately and Prevent Hackers from Exploiting These Loopholes Let’s Uncover the Risks
Why Organizations Conduct Penetration Tests
- 94% – Consider pentesting foundational for modern security programs to ensure a strong security posture
- 92% – View it as important to their organization's strategy and supported by senior leadership
- 91% – Believe it's critical for meeting business and compliance objectives
- 77% – Say it improves customer trust in their software products
- Statista says that over 1 million companies worldwide use the Microsoft Office 365 suite. So it’s no surprise it remains an attractive attack vector.
- The top 3 most notable critical Microsoft vulnerabilities, which CISA added to their list of most exploited vulnerabilities in 2021, are ProxyLogon (CVE-2021-26855 and CVE-2021-27065), ProxyOracle (CVE-2021-31196 and CVE-2021-31195), and ProxyShell (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207) (HelpnetSecurity).
- More data from the AppSec Stats Flash report indicates that remediation rates for critical vulnerabilities saw a decline from 54% in 2020 to 47% in 2021.
Most Common Security Assurance Requests from Customers or Regulators
- 59% – Request a third-party penetration testing report
- 54% – Ask for a third-party code review
- 52% – Require internal security test results
- 48% – Look for vulnerability scan reports
- 43% – Request compliance certifications (e.g., SOC 2, ISO 27001)
- 1% – Indicated none of the above are required
Pentesting Jobs and Salaries Statistics
In the U.S., over 22,000 job openings for penetration testers were posted last year, with computer science proficiency emerging as the most in-demand skill.
According to Payscale, entry-level penetration testers earn an average of $72,823 annually. With 5 to 9 years of experience, the average salary increases to $110,251, while seasoned professionals can earn approximately $124,607 per year.
CyberSeek data shows the educational backgrounds of penetration testers are as follows:
- 11% hold an associate degree
- 65% possess a bachelor’s degree
- 24% have earned a master’s degree
Demographic insights from CareerExplorer reveal that:
- 13% of ethical hackers are female, while 87% are male
- The largest ethnic group is White (42%), followed by South Asian (17%) and Other ethnicities (11%)
- The global cybersecurity talent gap remains significant. The number of unfilled cybersecurity jobs grew by 350%—from 1 million in 2013 to 3.5 million in 2021. This number is expected to remain at 3.5 million through 2025. (Source: Cybersecurity Ventures)
- Employment in computer and information technology roles is projected to grow by 13% from 2020 to 2030, outpacing the average for all occupations. This translates to 667,600 new jobs in the U.S. alone. (Source: U.S. Bureau of Labor Statistics)
- According to Gartner, by 2025, nearly half of cybersecurity leaders will change jobs, and 25% will shift careers entirely, citing work-related stress as the driving factor.
- In 2022, the average U.S. salary for penetration and vulnerability testers was $101,446.
- An entry-level penetration tester (less than 1 year of experience) earns an average total compensation of $70,324, while testers with 10–19 years of experience can earn as much as $120,953 annually. (Source: PayScale)
- In 2021, the U.S. had 22,075 online job openings for pentesters and vulnerability testers; that number rose to 27,409 in 2022.
- 66% of U.S. job listings for pentester roles require a bachelor’s degree, while only 24% require a graduate degree.
The top 5 skills most commonly requested by U.S. employers for pentester roles include:
- Information Security
- Penetration Testing
- Linux
- Python
- Java
Pentesting Salaries in Europe & UK:
- Germany: €58,151/year
- Netherlands: €44,352/year
- France: €42,624/year
- Italy: €30,968/year
(Source: PayScale) - United Kingdom:
- Average salary: £38,702/year
- Entry-level (less than 1 year): £33,822/year
- Experienced (10–19 years): £50,325/year
Industry Adoption of Penetration Testing
According to a 2025 report by the SANS Institute:
- Financial Services (26%) – Banks and fintech companies lead in penetration testing investment due to high-value data and strict regulatory requirements.
- Healthcare (19%) – Increased digitization of medical records and ransomware targeting hospitals have made this sector a major adopter.
- Technology & Software Development (17%) – Continuous integration/continuous deployment (CI/CD) pipelines now routinely include automated and manual pen tests.
- Government & Defense (14%) – National security concerns drive extensive red teaming and adversarial simulations.
- Retail & E-commerce (12%) – Online payment gateways and customer databases make these businesses prime targets for attackers.
Adoption Rates by Organization Size:
- Large Enterprises (10,000+ employees): 87% conduct regular pen tests.
- Mid-sized Companies (1,000–9,999 employees): 64% perform annual assessments.
- Small Businesses (<1,000 employees): 32% engage in some form of pen testing, often limited to external vulnerability scans.
Every Minute of Delay Can Cost Millions to Your Business, Perform Automated Pen Testing to Uncover Critical Risks Precisely Test Your App Now
Types of Pentesting in 2025
Notably, cloud security testing has seen a 47% YoY increase since 2023, reflecting the growing complexity of hybrid cloud environments and misconfiguration-related breaches.
| Type of Pentest | % of Organization Using | Key Focus |
|---|---|---|
| Web Application Testing | 68% | OWASP Top 10, API security |
| Network Infrastructure Testing | 57% | Firewalls, routers, VLANs |
| Wireless Network Testing | 43% | Wi-Fi, Bluetooth, IoT devices |
| Social Engineering | 39% | Phishing, vishing, tailgating |
| Cloud Security Testing | 51% | Misconfigurations, IAM policies |
| Mobile App Testing | 47% | Data leakage, insecure APIs |
| Red Team Operations | 22% | Full-spectrum adversary simulation |
Tools & Technologies Used in Penetration Testing
Most Popular Pen Testing Tools (Based on 2025 Black Hat Survey)
- Burp Suite Pro – Used by 78% of application security testers
- Nmap – Network scanning tool used by 72%
- Metasploit Framework – Exploitation framework adopted by 65%
- Nessus – Vulnerability scanner preferred by 61%
- Wireshark – Packet analyzer used by 58%
- SQLMap – SQL injection detection and exploitation used by 49%
- OWASP ZAP – Open-source alternative used by 42%
- Cloud Security Posture Management (CSPM) Tools – Adopted by 35%, with tools like Palo Alto Prisma Cloud and Wiz gaining traction
A notable trend in 2025 is the integration of AI and machine learning into penetration testing workflows. Approximately 28% of organizations use AI-powered tools to automate reconnaissance, vulnerability prioritization, and attack path simulation.
Cost and ROI of Penetration Testing:
- Web Application Pen Test: $4,500 – $15,000
- Network Infrastructure Pen Test: $6,000 – $20,000
- Red Team Exercise: $20,000 – $100,000+
- Social Engineering Test: $3,000 – $10,000
Despite initial costs, 78% of organizations reported a positive return on investment within 12 months, citing reduced breach risk, faster incident response times, and improved compliance posture.
Effectiveness of Penetration Testing in Breach Prevention
Key Findings:
- 68% of breached organizations admitted they had not conducted a pen test in the year prior to the incident.
- Organizations that conduct quarterly pen tests experience breach rates of 53% lower than those that test annually or less frequently.
- 81% of detected vulnerabilities during pen tests were rated as "high" or "critical", indicating the value of uncovering exploitable flaws before attackers do.
Common Vulnerabilities Identified:
- Misconfigured Cloud Storage (AWS S3, Azure Blob) – Found in 37% of tested environments
- Outdated Software Components – Detected in 32%
- Weak Authentication Mechanisms – Present in 29%
- Insecure APIs – Identified in 26%
- Privilege Escalation Flaws – Discovered in 21%
Regulatory Compliance and Pen Testing
- GDPR (EU) – Requires periodic security testing; drives pen testing in 41% of European firms
- HIPAA (US Healthcare) – Mandates risk assessments; leads to pen testing in 35% of healthcare providers
- PCI DSS – Requires annual pen testing for Level 1 merchants
- ISO/IEC 27001 – Encourages regular testing; adopted by 28% of certified organizations
- NIS2 Directive (EU) – New mandate requiring critical infrastructure operators to conduct red team exercises annually
Future Trends in Penetration Testing
- AI-Powered Automated Pen Testing Platforms – Expected to grow by 30% annually, reducing reliance on human labor for basic exploits.
- Integration with Zero Trust Architectures – Pen testing will focus more on identity verification, lateral movement, and micro-segmentation.
- Rise of Bug Bounty Platforms – Crowdsourced security testing is expected to account for 15% of all pen testing activities by 2027.
- Focus on OT and ICS Systems – Industrial control systems are becoming attractive targets, prompting specialized pen testing frameworks.
- Ethical AI Penetration Testing – Assessing AI models for biases, evasion techniques, and prompt injections will become a new vertical.
Empower Your AppSec with Next-Gen Security Testing Capabilities and Protect Your Assets Effectively Contact Experts for Help
Conclusion
The pentesting statistics 2025 reveal a maturing cybersecurity mindset across industries with penetration testing emerging as a linchpin for risk management, compliance, and breach prevention. As attack surfaces expand and threats become more advanced, traditional security audits are no longer sufficient.
Pentesting tool for web apps and APIs like ZeroThreat represent the next phase of automated, accurate, and adaptive security testing. With near-zero false positives, MFA support, and seamless integration into CI/CD pipelines, platforms like ZeroThreat enable businesses to test smarter, respond faster, and secure deeper.
Organizations that prioritize consistent and strategic penetration testing will continue to stay one step ahead of attackers, turning security from a reactive cost center into a proactive enabler of trust and resilience.
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


