All Blogs
Healthcare API Penetration Testing: Ensure App Security, Compliance & Trust

Quick Overview: Healthcare API penetration testing helps uncover security gaps that could expose patient data or disrupt connected healthcare systems. This blog breaks down the importance of pentesting, core testing stages, compliance factors, and real-world challenges. It will help you strengthen healthcare organizations' security posture and ensure the ongoing protection of sensitive medical information.
Healthcare APIs connect electronic health records, mobile health apps, insurance systems, and countless third-party services. They make patient care faster and more connected. But they also create new entry points for attackers. A single flaw in an API can expose sensitive patient information, putting security, compliance, and trust at risk.
That’s why healthcare API pentesting becomes essential to perform. It allows you to simulate an attack and find vulnerabilities in your healthcare systems before the attackers do. In fact, this practice is so beneficial to organizations that today, 35% of healthcare providers adopt pentesting as part of their security programs.
In this blog, we’ll help you learn about the stages of healthcare API penetration testing, compliance considerations, and its challenges. But before we dive into that, let's first understand what API pentesting is and why it’s important.
Secure all your healthcare APIs with smart threat intelligence. Do a Quick Test
On This Page
- What is Healthcare API Penetration Testing?
- Why is API Penetration Testing Important in Healthcare?
- Stages of Penetration Testing for Healthcare APIs
- Compliance Considerations for Healthcare APIs Pentesting
- Challenges in Healthcare API Penetration Testing
- How ZeroThreat Simplifies Healthcare API Security Testing
- Wrapping Up
What is Healthcare API Penetration Testing?
Healthcare API pentesting is the process of simulating real-world attacks on APIs to uncover hidden weaknesses before attackers exploit them. Unlike basic testing, it focuses on patient data protection, regulatory compliance, and resilience against OWASP-listed API vulnerabilities.
For healthcare organizations, pentesting means more than just basic security practices. It’s about verifying whether APIs that handle Protected Health Information (PHI) are properly secured against various threats or not. In practice, this testing helps teams close security gaps early, avoid costly HIPAA penalties, and strengthen trust among patients.
Why is API Penetration Testing Important in Healthcare?
API penetration testing in healthcare is the foundation of three essential pillars: security, compliance, and trust. Here’s why each one matters:
Security
Healthcare APIs are often the entry point to sensitive patient data. A single flaw can expose records, disrupt critical systems, or give attackers unauthorized access. Penetration testing helps identify and fix these weaknesses before they can be exploited, ensuring patient data stays safe.
Compliance
Regulations like HIPAA, GDPR, and HITRUST set strict requirements for handling medical information. Failure to meet them can lead to hefty fines and loss of certification. API penetration testing ensures your systems align with these standards, reducing compliance risks.
Trust
Patients and partners expect healthcare providers to protect their data. Any breach erodes that trust instantly. Regular API penetration testing shows that you take security seriously, which strengthens confidence in your services and safeguards your reputation.
Stages of Penetration Testing for Healthcare APIs
Penetration testing for healthcare APIs allows you to find the security vulnerabilities before they turn into a threat. Here are the general stages of API pentesting (exact stages may vary based on the process you follow).
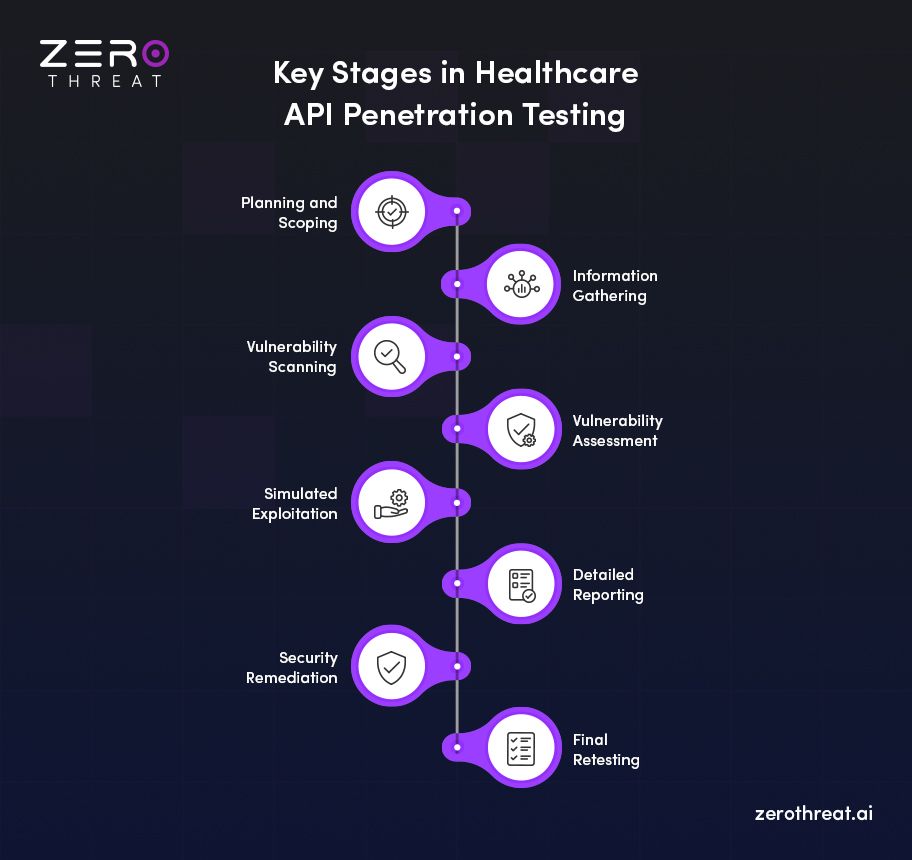
Stage 1: Planning & Scoping
Every healthcare API penetration testing project starts with planning. Here, the scope includes which APIs will be tested, what data flows are in play, and how they interact with patient information. Clear scoping ensures compliance boundaries are respected, especially when PHI is involved under HIPAA rules.
Stage 2: Information Gathering
This stage focuses on mapping out the healthcare API environment. Testers collect details about endpoints, authentication methods, and data structures. The goal is to understand how APIs connect with EHRs, payment systems, and mobile health apps, so potential attack surfaces can be identified early.
Stage 3: Vulnerability Scanning
Automated API security tools are used to scan healthcare systems for known weaknesses. These scans flag misconfigured endpoints, outdated libraries, or insecure tokens. In API security testing for healthcare, vulnerability scanning is required to spot issues that could put patient data at risk.
Stage 4: Vulnerability Assessment
Once vulnerabilities are found, they must be assessed based on the potential impact they could have, as not all flaws carry the same weight. A weak endpoint exposing non-sensitive data is less critical than one leaking PHI. This stage prioritizes risks based on sensitive data exposure and compliance impact.
Stage 5: Simulated Exploitation
Here, testers attempt to exploit vulnerabilities in a controlled way. The aim is not to damage systems but to prove whether flaws can be used to access sensitive data or bypass controls. Simulated exploitation shows the real-world impact of weaknesses in API security, helping teams understand what to fix.
Stage 6: Detailed Reporting
A pentest report highlights each vulnerability, how it was discovered, its impact on patient data, and how it maps to OWASP for healthcare APIs. This report gives CIOs, compliance officers, and IT directors a clear picture of actual risks. Some reports also include actionable remediation guidance to ease the work of security patching.
Stage 7: Security Remediation
The remediation stage includes patching code, tightening authentication, encrypting data flows, or reconfiguring API endpoints. In healthcare platforms, remediation is guided by both security best practices and regulatory frameworks like HIPAA. This ensures the security fixes protect data while maintaining compliance.
Stage 8: Final Retesting
Once fixes are applied, APIs are tested again to confirm vulnerabilities are closed. This retesting stage validates that remediation steps were effective and that no new weaknesses were introduced. For healthcare providers, final retesting is essential to maintain patient trust and demonstrate strong API security controls.
Pentest your Healthcare APIs before security gaps cost you fines or breaches. Secure Your API Endpoints
Compliance Considerations for Healthcare APIs Pentesting
When it comes to compliance, the healthcare sector has one of the strictest regulations. Here are the key compliances you should consider in your pentest process.
HIPAA
HIPAA sets the standard for protecting patient health information in the U.S. During healthcare API penetration testing, ensuring HIPAA compliance means verifying that PHI cannot be accessed without proper authorization. It also requires that data in transit and at rest is encrypted, and audit logs are maintained for accountability.
HITRUST CSF
HITRUST CSF provides a comprehensive framework that combines multiple healthcare and IT security standards. Penetration testing aligned with HITRUST ensures that APIs follow best practices for access control, data protection, and risk management across the entire healthcare ecosystem.
HITECH Act
HITECH strengthens HIPAA by emphasizing electronic health record security and breach notification requirements. In healthcare API penetration testing, it ensures that any risks to patient data are found quickly and fixed, and every breach is reported as required.
GDPR
For healthcare platforms handling EU patient data, GDPR is critical. API penetration testing checks that personal health data is processed lawfully, stored securely, and only shared with authorized parties. Non-compliance can result in severe fines, making it a key consideration for global HealthTech applications.
CCPA
CCPA governs personal data protection for California residents. In healthcare API testing, ensuring CCPA compliance means confirming that patients can access, delete, or restrict sharing of their personal data. This aligns API security practices with consumer privacy rights and regional regulations.
Challenges in Healthcare API Penetration Testing
Healthcare API pentesting isn’t like testing a retail app. The stakes are higher, the systems are more complex, and the consequences of getting it wrong can break your bank. Here’s what makes it so tough:
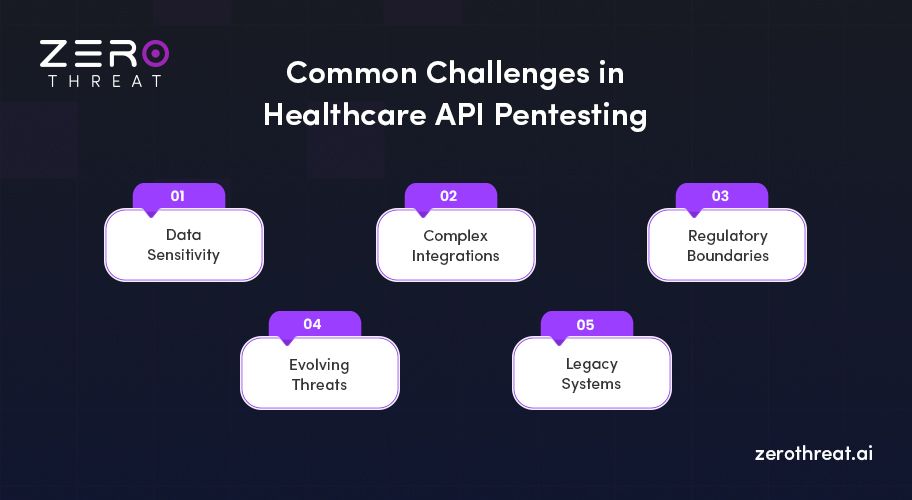
Data Sensitivity
Healthcare APIs handle protected health information (PHI), making every test a potential risk if not scoped correctly. One wrong move could expose sensitive records, so security testing for healthcare must follow strict privacy safeguards.
Complex Integrations
APIs in healthcare connect with EHRs, insurance systems, and third-party apps. This complexity makes API vulnerability testing in healthcare harder, as a single weak link can compromise multiple systems.
Regulatory Boundaries
Testers can’t always simulate full-scale attacks because of HIPAA, HITRUST, and GDPR restrictions. While these standards protect patient data, they also limit how penetration testing for healthcare APIs is carried out.
Evolving Threats
Healthcare APIs face constant new threats, from injection attacks to token mismanagement. Therefore, testers must continuously adapt their approach, since static scans or outdated tools often miss modern threats.
Legacy Systems
Many hospitals still rely on older systems connected to modern APIs. This mix creates vulnerabilities that aren’t easy to patch and require careful API security testing to avoid breaking essential workflows.
How ZeroThreat Simplifies Healthcare API Security Testing
Securing healthcare APIs can feel overwhelming when patient data, compliance rules, and constant threats collide. ZeroThreat makes this easier by combining an API pentesting tool and compliance-ready reporting in one platform.
- Complete API Coverage: ZeroThreat uncovers risks across internal, public, zombie, and shadow APIs, ensuring no endpoint slips through unnoticed.
- Fast and Accurate Testing: With 98.9% accuracy and scans done in hours, not weeks, security teams can act before attackers do.
- Built-In Compliance: The platform aligns with HIPAA, GDPR, and more, giving you audit-ready reports without extra effort.
- AI-Driven Fixes: Each finding comes with evidence-based reports and remediation steps, reducing security patching time.
- Reduced Manual Work: By automating 90% of pentesting tasks, ZeroThreat frees teams to focus on strategy, not repetitive checks.
ZeroThreat turns healthcare API security testing from a burden into an easy step toward safer systems with compliance.
Secure your healthcare APIs before it’s too late. Connect Us
Wrapping Up
Proactive API security is essential for healthcare organizations handling sensitive patient data. Identifying weaknesses in authentication, data handling, and integration helps prevent breaches that can disrupt care and harm trust.
Investing in an automated pentesting tool allows security teams to simulate attacks and uncover vulnerabilities before attackers do. It also simplifies compliance with regulations like HIPAA and GDPR, turning a complex security requirement into a manageable, continuous process.
So, what are you waiting for? Take a step toward safer, more trusted digital healthcare by actively pentesting your APIs and fixing vulnerabilities in advance.
Frequently Asked Questions
What makes HealthTech APIs more vulnerable than other APIs?
HealthTech APIs handle sensitive PHI and integrates with legacy systems, creating complex attack surfaces. They’re prime targets for hackers due to high-value data and often lack rigorous security testing. Many also rely on third-party integrations, which can introduce unseen risks.
Is penetration testing mandatory for HIPAA compliance?
Can HealthTech APIs be tested automatically during CI/CD?
How often should HealthTech platforms perform API penetration testing?
What are common API vulnerabilities in HealthTech platforms?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


