All Blogs

Quick Overview: This blog explains API penetration testing, a crucial practice to identify and fix vulnerabilities before attackers exploit them. It covers what API pentesting is, why it matters, the challenges involved, and key steps in the process. Learn how to strengthen API security, safeguard sensitive data, and ensure safer digital interactions.
APIs power everything from web apps to smart home devices, streaming services to financial systems. But the same APIs that drive innovation are also where attackers strike first. Hidden flaws in logic, weak authentication, or misconfigurations can make a doorway for attackers to exploit your site.
Reports estimate that poorly secured APIs could expose businesses to losses of up to $75 billion globally. And with API attacks growing year after year, ensuring security no longer remains optional.
This is where API pentesting steps in. By simulating real-world attacks, pentesting reveals the vulnerabilities that matter most, the ones hackers actually exploit. In this blog, we’ll break down what API penetration testing is, the different types, and provide a practical checklist you can use to strengthen your API security.
Secure All Your API End Points with Smart Threat Intelligence Do a Quick Test
On This Page
- What is API Penetration Testing?
- Why API Penetration Testing is Important?
- Benefits of API Pentesting
- Common API Vulnerabilities Exploited in Penetration Testing
- API Penetration Testing Checklist to Strengthen Security
- Key Challenges of API Penetration Testing
- How ZeroThreat Makes API Penetration Testing Effortless
- Let’s Summarize
What is API Penetration Testing?
API pentesting is a process of simulating real-world attacks on APIs to discover vulnerabilities before hackers do. Unlike surface-level scans, it digs into how your API handles authentication, authorization, and data exchange to find out the exploitable vulnerabilities.
In practice, API testing goes beyond just checking endpoints. It looks at how your API interacts with mobile apps, web applications, and third-party integrations. The goal of pentesting is to know current vulnerabilities, along with finding potential vulnerable endpoints that hackers may exploit. For companies that rely heavily on APIs, pentesting becomes a crucial part of their security checklist.
Types of API Pentesting (Based on Knowledge Level)
API penetration testing can be carried out in different ways depending on how much information the tester has about the system. Here are the three main types:
- Black Box Testing: Testing the API without prior knowledge of its structure or code, simulating an external attacker’s perspective.
- White Box Testing: Full knowledge of the API architecture, code, and documentation is provided to the tester.
- Gray Box Testing: Partial knowledge of the API is there, combining both insider and outsider perspectives.
With that, we have understood API pentesting and its types. Now let’s jump to the next section, where we’ll learn about the importance of API pentesting.
Why API Penetration Testing is Important?
API penetration testing is important because APIs are often the main entry point to business-critical systems. If they are left untested, attackers can exploit weaknesses in authentication, authorization, or data handling to steal sensitive information. A single exposed API can put customer trust, compliance, and business continuity at risk.
Pentesting helps uncover these issues before they can be exploited by attackers. It gives security teams a clear picture of how secure their APIs are against real-world attacks. This allows the experts to build and deliver secure applications.
Benefits of API Pentesting
API penetration testing is used to make APIs resilient against real-world attacks. Here are the key benefits it can bring:
Mitigates API Risks
Pentesting identifies flaws like broken authentication, insecure endpoints, or injection risks before attackers can exploit them. By addressing these risks early, you reduce exposure to common API vulnerabilities. This approach keeps your systems safer and reduces the attack surface.
Strengthens API Security
Regular pentesting helps validate how well your existing security controls are working. It exposes weak spots on various layers of your API. So, in that case, API security testing can help you reduce the attack surface area and make your API or web application more reliable.
Builds Customer Trust
Customers want to know if their data is safe when using your applications. Demonstrating that you regularly test and secure your APIs shows you take security seriously. This builds trust and strengthens long-term relationships with users and partners.
Ensures Regulatory Compliance
Many industries require strong API security under compliance frameworks like GDPR, HIPAA, or PCI DSS. Pentesting provides evidence that your APIs are tested and secured against real threats. This not only helps meet requirements but also reduces audit-related stress.
Reduces Security Costs
Fixing an exploited vulnerability after a breach is far more expensive than preventing it. Pentesting helps organizations catch issues early, when they are cheaper and faster to fix. It lowers the financial and reputational costs tied to data leaks and downtime.
In short, API penetration testing reduces risk, builds trust, and keeps your business secure while saving time and money in the long run.
Common API Vulnerabilities Exploited in Penetration Testing
The simulated attack made on the APIs can detect thousands of weaknesses in your system. Some of the most common vulnerabilities among them are:

Broken Authentication
Due to broken authentication, attackers can bypass login mechanisms or steal tokens to impersonate real users. APIs that don’t protect sessions properly or rely on predictable tokens are easy targets. This often results in unauthorized access to accounts or sensitive business data.
Broken Object Level Authorization (BOLA)
BOLA happens when an API exposes endpoints without checking if the user has the right to access that resource. Attackers can simply change an object ID in the request and view or modify someone else’s data. It’s one of the most common and dangerous API flaws.
Excessive Data Exposure
Sometimes APIs return more data than they should, assuming the client will filter out what’s unnecessary. Here, attackers can analyze the responses and extract sensitive information. Even hidden fields or log data in responses can leak valuable details.
Lack of Rate Limiting
APIs without rate limits allow attackers to send unlimited requests in a short time. This opens the door to brute-force attacks, credential stuffing, or denial-of-service (DoS) attempts. Without limiting the number of API requests or implementing throttling, even a small botnet can overwhelm your systems.
Injection Attacks
Injection flaws occur when untrusted input is passed directly into queries or commands. An attacker can manipulate requests to run malicious SQL, NoSQL, or system commands. This can lead to full database compromise or control over backend systems.
Mass Assignment
APIs that bind user input directly to data objects without filtering are at risk of mass assignment. Attackers can submit unexpected fields in a request and modify properties they shouldn’t have access to. For example, an attacker can change a user’s role from “user” to “admin.”
Broken Function Level Authorization (BFLA)
This happens when APIs fail to enforce role-based access on certain functions. A regular user might gain access to administrative endpoints just by calling them directly. If sensitive operations are not restricted, attackers can escalate their privileges and exploit your API.
Improper Data Validation
When APIs don’t validate input or sanitize it, attackers can insert malicious code or unexpected data formats. This can create security issues such as cross-site scripting (XSS) or buffer overflows. Strong validation ensures only safe and expected data gets processed.
Insecure Direct Object References (IDOR)
IDOR allows attackers to manipulate references (like file names, IDs, or keys) in API requests to gain unauthorized access. For example, changing an invoice ID in the request to view another customer’s bill. It’s simple to do for an attacker, but highly effective to get sensitive data.
Discover Vulnerabilities in REST, SOAP, and GraphQL APIs in a Click Secure Your API
API Penetration Testing Checklist to Strengthen Security
Ensuring security is not easy, and APIs are one of the most vulnerable points that attackers may try to exploit. Here are some pentesting checks you can do to detect vulnerabilities in your web app and API before the hacker does.
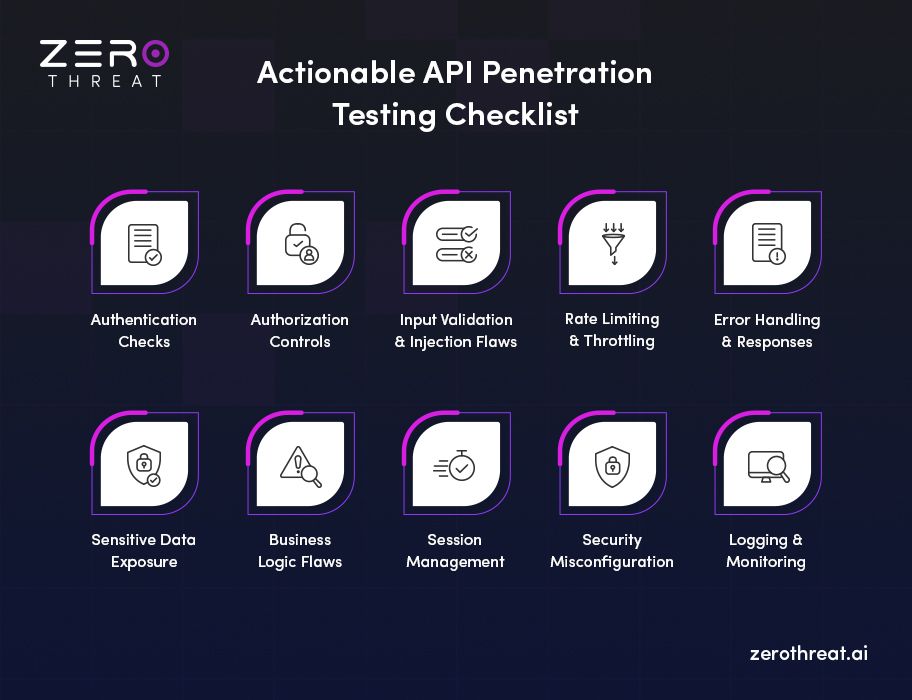
1. Authentication Checks
Verify how the API handles user logins and token-based authentication. Check if weak or default passwords are allowed, and whether tokens expire properly. Test if API keys or JWTs can be guessed, reused, or stolen. Look for missing multi-factor authentication where it should exist. Weak authentication is often the easiest doorway in for attackers.
2. Authorization Controls
Ensure users can only access the data and actions they are allowed to (least privilege). Try changing object IDs or user roles in requests to see if you can access restricted resources. Validate role-based access controls (RBAC) and function-level permissions. Test both vertical (admin vs. user) and horizontal (user vs. user) privilege escalation.
3. Input Validation & Injection Flaws
Send unexpected input such as SQL commands, NoSQL queries, or special characters to test how the API responds. Look for places where unvalidated data can get passed into queries or system commands. Check if error messages expose raw database details. A proper input validation should sanitize and not accept malicious payloads.
4. Rate Limiting & Throttling
You should send multiple requests to APIs; it will let you know if limits are in place. If the API doesn’t slow you down or block suspicious activity, then rate limiting or throttling is not implemented. That means your system is still vulnerable to brute-force attack, which is one of the commonly used tactics by attackers
5. Error Handling & Responses
Here, in this testing, you need to trigger errors intentionally and observe the response you get from the API. If your API is secure, it will return only the generic error messages, not detailed stack traces or debug info. On the other hand, if the API responds with system details, version numbers, or any other database information, your API is vulnerable and exploitable.
6. Sensitive Data Exposure
Inspect API responses for data that shouldn’t be visible. Look for excessive fields like passwords, tokens, or internal IDs being returned. Test if responses are encrypted in transit (TLS/HTTPS). To prevent sensitive data exposure, it should always be encrypted, masked, or protected. Even small leaks can give attackers enough to create a threat out of vulnerability.
7. Business Logic Flaws
Think like a user and test workflows for loopholes. Can you bypass steps in a transaction? Can you manipulate order values, discounts, or limits? Business logic vulnerability isn’t always technical; it often exploits how the system is designed. Testing this manually can help you reveal vulnerabilities that scanners can miss.
8. Session Management
Test how sessions are created, maintained, and invalidated. Does logging out actually swipes the session token? Can you reuse old tokens after they have expired? Check for secure flags on cookies and token storage. If the session management is poor, attackers can hijack accounts without needing credentials.
9. Security Misconfiguration
Check if the API is running with default settings, unnecessary services, or outdated components. Look for security misconfigurations such as exposed admin consoles, open ports, or directory listings that should not be public. Test if CORS policies are too permissive, allowing any domain to make requests. Therefore, proper hardening and regular reviews are a must to prevent such issues.
10. Logging & Monitoring
Look for signs that indicate failed login, unusual requests, or injection attempts. If the API is not logging such suspicious activity, kindly add an alert system. This will help you get notified when an attacker is trying to hack your API or system.
Key Challenges of API Penetration Testing
API pentesting, if done manually, is a complex and long process. It can take days to test APIs and check every possible way an attacker may exploit them. The challenge of penetration testing includes:
- Too Many Endpoints to Test: Modern APIs can have hundreds of endpoints. Missing even one could mean leaving a serious risk unchecked.
- Testing Takes a Lot of Time: Good API pentesting isn’t quick. It needs skilled testers, setup, and patience, especially when the documentation is incomplete.
- New Threats Keep Emerging: Attack methods change rapidly; what you tested last month might be outdated by now. So, continuous testing becomes a necessity.
- Complicated Login and Access Controls: OAuth, tokens, various roles, and multi-factor logins are not that easy to test. One mistake while testing authentication can become the reason behind complete hijacking.
- Different Protocols and Data Formats: REST, GraphQL, gRPC, SOAP; each API type works differently. Testing all of them requires different tools and specific expertise.
- Test Environment Issues: The staging site often doesn’t match production. Rate limits, missing features, or restrictions can make pentesting less accurate.
How ZeroThreat Makes API Penetration Testing Effortless
ZeroThreat’s API pentesting tool tool simplifies the identification of current and potential vulnerabilities in your APIs. Instead of spending days setting up tests, you get a platform built for speed and accuracy from day one.
Here is how ZeroThreat makes penetration testing as easy as snapping your fingers.
- With ZeroThreat, you can scan 2,000+ URLs in just 15 minutes, which means you uncover issues fast.
- ZeroThreat promises 98.9% accuracy in detecting vulnerabilities, indicating minimal false positives.
- It cuts down the manual testing work by 90%, taking off most of the load and reducing repetitive work.
- ZeroThreat targets 40,000+ vulnerabilities, including OWASP Top 10 and logic-based attacks.
- “Zero Config, No Expertise.” That’s how simple and easy ZeroThreat is to use. It’s simply click and go.
- If you work under GDPR, HIPAA, PCI DSS, or other regulations, ZeroThreat helps you stay compliance-ready.
These benefits of using ZeroThreat are just the tip of the iceberg. If you are a penetration tester or someone who wants to test an API or website with or without any prior testing knowledge, try ZeroThreat for free.
Detect and Fix Security Risks with ZeroThreat’s Security Testing Tool Start Free Scan
Let’s Summarize
APIs are at the core of modern applications, carrying sensitive data and critical business logic every single day. That makes them one of the most attractive targets for attackers and one of the most important areas to secure. API penetration testing is the safety net that helps you spot hidden flaws before hackers do.
To truly reduce risk, regular pentests, strong authentication, continuous monitoring, and secure coding practices all need to work together. When combined, they can reduce the risk of attack by closing every exploitable vulnerability.
If pentesting is done manually, it is challenging and time-consuming. You can opt to use an automated pentesting tool like ZeroThreat that makes the testing process as simple as a click.
Frequently Asked Questions
What is the difference between API penetration testing and web penetration testing?
API pentesting focuses on endpoints, authentication, and data exposure within APIs. On the other hand, web pentesting targets full applications, including UI, business logic, and server configurations. Both are essential for complete security coverage.
How is API penetration testing different from vulnerability scanning?
What tools are used for API pentesting?
What does an API pentest report include?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


