All Blogs

Quick Summary: Phishing is a notorious cyberattack technique that causes heavy losses to organizations and individuals. An understanding of this threat, its types, and ways to detect it is crucial to ensure robust cybersecurity. This blog will help you understand phishing attacks and their types to enable you to make informed decisions.
When it comes to creating a cybersecurity strategy for their organizations, CISOs or security teams must consider diverse attack vectors that could pose a potential threat. One of those attack vectors includes phishing, which is a critical cybersecurity challenge for organizations today.
Phishing is a kind of scamming scheme that involves tricking victims into installing malware or divulging their sensitive information. It involves using social engineering techniques to dupe victims into doing unwarranted actions.
Attackers use different types of phishing methods to lure victims and steal their sensitive information. Get complete information about phishing, its types, and tips for mitigation in this blog.
Get 10X Faster Results with 98.9% Accuracy to Mitigate Cybersecurity Risks Do a Scan Now
Table of Contents
- A Quick Overview of Phishing Attack
- Types of Phishing Attacks
- How to Detect a Phishing Attack?
- How to Mitigate the Risks of a Phishing Attack?
- To Wrap Up
A Quick Overview of Phishing Attack
Phishing is a deceptive technique in which an attacker sends fake emails or text messages with malicious content attached to them. When victims respond to these contents by clicking or downloading them, they fall prey to a cyberattack.
Usually, people associate Phishing attack with malicious emails that include dubious links or attachments with a message evoking urgency, fear, or excitement. However, phishing is not just about emails now as attackers also use other methods or channels like text messages, social media, phone calls, etc.
Phishing leverages psychological tactics to force victims into performing tasks that lead to identity theft, loss of data, malware installation, and other types of cybersecurity issues.
Over the years, global organizations have seen a sharp increase in email-based cyberattacks, as per Statista’s report. This indicates a growing concern for organizations. They need a robust cybersecurity approach and perform regular risk assessments to identify and mitigate potential threats.
Types of Phishing Attacks
Attackers use a wide range of tactics in an attempt to launch a successful phishing attack. So, this attack uses different threat vectors. The following are the different types of phishing attacks.
Email Phishing
This is the most common phishing attack today. An attacker sends emails to victims that seem to come from a legitimate source. The attacker includes a persuasive message that lures victims into entering sensitive information or downloading a malicious file.
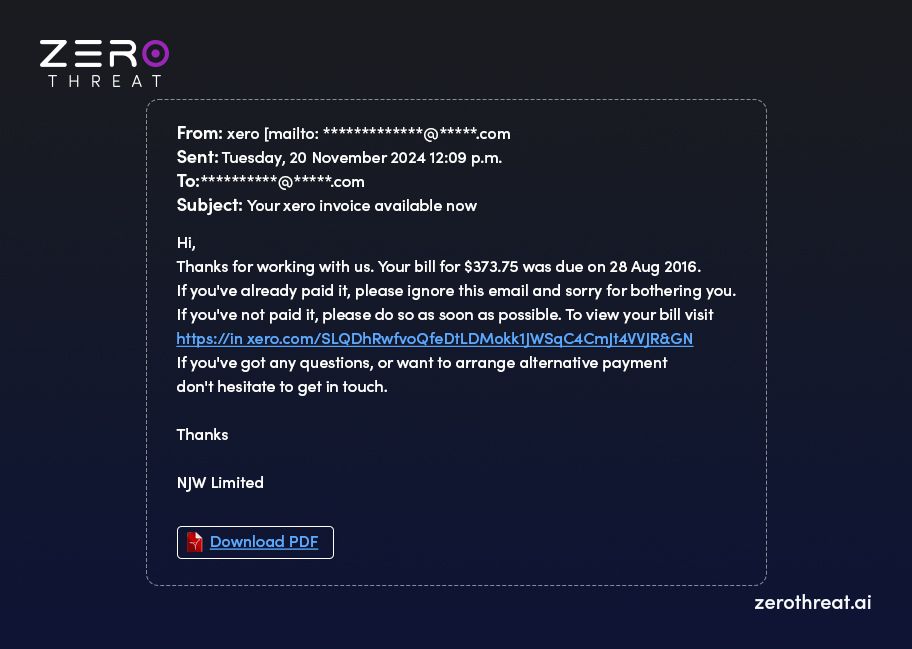
The email sent by the attacker is fake and contains malicious links or attachments that cause security issues when victims click or download them. The attacker can get the victim’s sensitive data like credit card numbers, account information, etc, or load malware like ransomware on his/her system.
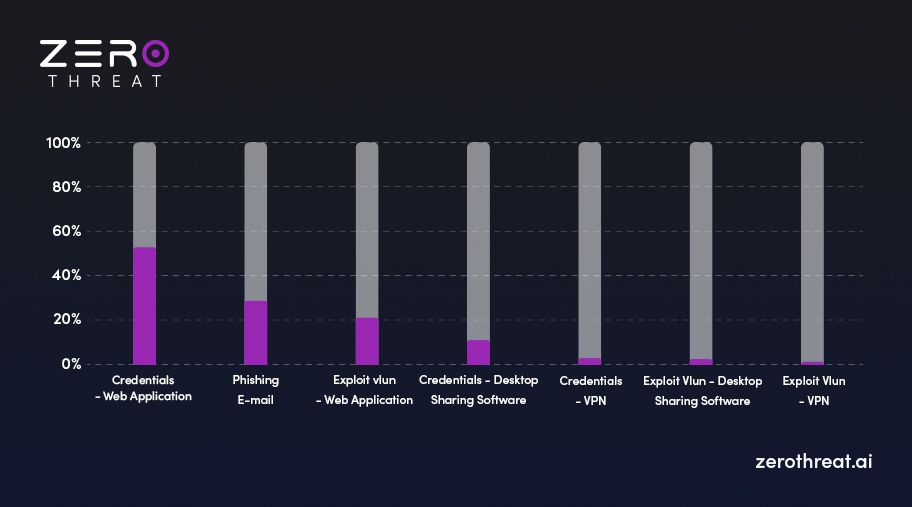
The following is the graphical representation of the different ways attackers use to launch cyberattacks or cause a data breach. As you can see in the image below, Email phishing is the second most common attack vector utilized by attackers to fulfill their malicious objectives.
Spear Phishing
In this method, an attacker targets a specific type of victim or group whose information, such as name, position, contact details, etc., has already been gathered. Often, the attacker attempts to steal the login credentials of a victim through a spear phishing attack.
The attacker sends a personalized email or text message that seems legitimate, creating a sense of fear or urgency to take a dubious action. The victim is lured into providing sensitive information by clicking a link. The attacker can manipulate a victim to perform an action like transferring money.
Whaling
This is a kind of phishing attack that aims to target executives or high-profile people in an organization. Since these individuals possess highly sensitive or confidential information or have deep access to a network, they are a big target for attackers to get high-value information.
Therefore, the attacker designs whaling attacks to lure such individuals into divulging sensitive information that can lead to unauthorized access or huge business loss. For example, one of the founders of Levitas, a hedge fund company based in Australia, fell prey to whaling with a fraudulent Zoom link that resulted in a loss of $800,000.
Smishing and Vishing
Attackers are now leveraging new lines of communication to trick victims into divulging sensitive information. Smishing or SMS phishing is a type of phishing attack in which the attacker sends fraudulent text messages to victims. The attacker includes a malicious link or file in the text message, just like an email.
Vishing (voice call phishing) is a kind of phishing scam in which attackers use fake calls to lure victims into revealing sensitive information. In this case, the attacker poses as a legitimate organization to defraud victims or threaten them.
For example, scammers could pretend to be a government official, a policeman, a shipper, customer support personnel, or anybody else like this to trick victims into divulging information.
Angler Phishing
In this type of Phishing attack, social media becomes the playground for attackers. They exploit the trust people have in legitimate social media accounts of organizations that they have engaged with. The attacker can forge a legitimate account with similar names and profile pictures.
For example, the attacker can use a fake social media handle that seems legitimate, like “@pizzahutcustomercare” to dupe victims into revealing sensitive information on the pretext of providing support or help.
Attackers can use cloned websites, fake URLs, fake posts, and other stuff on social media to trick victims into revealing sensitive information.
Shed Your Cybersecurity Fears with Next-Gen Threat Assessment Tool to Uncover Hidden Loopholes Try It for Free
How to Detect a Phishing Attack?
These days, phishing attacks have become more challenging because attackers are using novel techniques to carry out these attacks. Preventing phishing attacks requires multi-dimensional cybersecurity measures comprising detection of vulnerabilities, employee awareness, and regular network monitoring. The following points provide the signs to detect phishing attacks.
Style of Message
Inconsistency and inappropriate use of language and tone are the vital signs of phishing attacks. So, the unusual tone or language that you cannot expect from the sender should be an indicator of something amiss. You should carefully check your email or message before taking action.
Urgency or Threat
You should consider threats or urgency in messages/emails with skepticism. Phishing attackers use this technique of creating fear or urgency to encourage the recipients to take action in a hurry without scrutinizing the contents of the email or message.
Linguistic Errors
Grammatical mistakes and misspellings are another sign of possible phishing emails. Mostly, organizations use spell-checkers for outgoing emails to ensure they are free of grammatical errors and spelling mistakes. Hence, emails with these kinds of issues should raise suspicion.
Inconsistent Sources
Mismatched domain names in URLs and email addresses are another sign of a phishing attack. You should check previous emails to verify the sender’s domain. If there is any inconsistency, it should raise suspicion. Hovering over a link can provide more information that can help avoid the potential risks.
Request for Sensitive Details
Phishing attacks ask for sensitive information like account number, credit/debit card number, etc. Plus, these attacks take victims to another page, which is fake and created by an attacker. The page includes login forms with various fields asking for personal information or credentials. They are also signs of phishing methods.
How Can You Mitigate the Risks of a Phishing Attack?
Phishing can become a critical challenge for organizations as it can allow attackers to gain access to sensitive information or infect systems with malware that can cause bigger threats. Let’s check out some tips to help prevent phishing attacks.
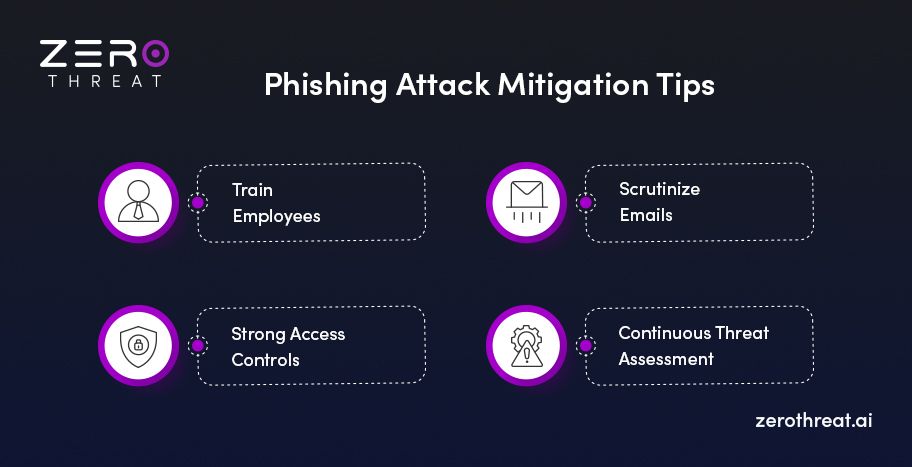
Train Employees
Training employees on security best practices is an effective way to thwart cybersecurity risks like phishing. Employee training helps make them aware of the potential risks and attack methods, enabling them to mitigate the threats.
The training will help educate employees and stakeholders about the impacts and patterns of phishing attacks. The awareness will help prevent employees from falling prey to phishing attacks.
Scrutinize Emails
Scrutinizing emails is another helpful method to prevent the phishing threat. Social engineering attacks like phishing rely on human errors or fallibility. Especially, these attacks become successful when recipients act hurriedly or in a rush.
Hence, email scrutinizing is essential to mitigate the potential threats by thoroughly checking its contents for flaws, grammatical errors, inconsistencies, and other issues. It will help prevent phishing threats.
Strong Access Controls
Make sure that there are stronger access controls to protect against phishing and other cyber threats. A strong access control will prevent unauthorized parties from accessing sensitive data. Plus, you can also follow the least privilege principle.
With this principle, you have to implement strong authentication and authorization for every user. Plus, ensure limited access to data and resources based on their roles. So, even if an account is compromised, an attacker cannot gain access beyond that account’s role.
Continuous Threat Assessment
Another way to mitigate the risk of phishing attacks is regular vulnerability scanning to uncover any loopholes or weaknesses that attackers may exploit. Attackers can take advantage of a vulnerability to deploy malware or gain access to your system.
Discover Potential Security Threats in Minutes and Protect Your Digital Assets Scan for Free
To Wrap Up
Phishing is quite dangerous from a security and privacy point of view as attackers primarily target critical data of an organization. There are many kinds of risks from this cyber threat if remains unaddressed. You need a multi-faceted approach to prevent such threats.
Detection and prevention of security weaknesses is an integral part of this strategy that requires a robust tool, ZeroThreat. As an AI-powered web and API security testing tool, it helps uncover flaws and misconfigurations that go unnoticed by security teams.
It helps strengthen your security posture to prevent threats from social engineering and many other types of cyberattacks. It can effectively detect a wide range of CVEs with near-zero false positives. You can leverage it to detect zero-day exploits and out-of-band vulnerabilities that most tools fail to identify.
Take a free tour of this tool to learn how it can benefit your battle against cybersecurity threats.
Frequently Asked Questions
Which phishing attacks are the most common?
Email phishing, spear phishing, smishing, and vishing are the most common types of phishing methods used by attackers to steal sensitive information from victims.
What are the different stages of phishing attacks?
How is smishing different from vishing?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


