All Blogs
Guide to Prevent SQL Injection Attacks in Node JS Web Apps

Quick Summary: Node JS is widely used for web app development because of its seamless architecture and efficient features. As its community expands, its security threats evolve. Here, we are going to discuss one of the common security threats in Node JS: SQL injection. We’ll discuss common examples of SQL injection attacks along with steadfast security measures to prevent common security threats in Node JS web apps.
Node JS has gained remarkable popularity due to its efficient handling of asynchronous operations, which is substantial for modern web applications. By optimizing JavaScript both on the frontend and backend, Node JS enables developers to use a unified language and data format throughout the entire stack. Also, it streamlines development and maintenance ultimately making itself a top-notch choice to build scalable web applications.
As per the research, 6.3 million websites are using Node JS. This JavaScript runtime environment is the top choice for web development in the United States.
But as Node JS is becoming a prime choice for web applications, we all are witnessing an equal rise in potential security threats that adversely affect Node JS web apps, one of which is SQL injection attacks.
Here we are going to discuss some of the most attention seeking examples of Node JS SQL injection attacks along with sure-shot strategies to prevent SQL injection in Node JS web apps. Refer to this article to eradicate all the potential node JS vulnerabilities that pose notable security threats.
With Zerothreat's Advanced Security Scanning Techniques, There's No Escape for Vulnerabilities Make a Free Attempt
On This Page
- Why Do SQL Injection Attacks Occur in Node JS?
- Common Examples of SQL Injection Attacks
- How to Prevent NodeJS SQL Injection Attacks?
- Harness ZeroThreat to Prevent Node JS SQL Injection Attacks
Why Do SQL Injection Attacks Occur in Node JS Web Apps?
SQL injection attacks in Node JS web applications majorly occur when developers fail to properly handle user inputs that are directly used in SQL queries without doing proper sanitization or parameterization. Let's delve deeper into the common causes behind Node JS SQL injection attacks to pose suitable web app security measures for avoiding future vulnerabilities in Node JS apps.
1. Concatenation of User Input
If the stage of validation and sanitization of user-provided data like form inputs or URL parameters is missed or improperly done by developers, then it leaves room for malicious users to inject SQL code into the query. The user-provided data cannot be directly concentrated into SQL queries without required precautions.
2. Improper Use of ORM or Query Builders
Object-relational mappers (ORM) and query builders like Sequelize or Knex.js help developers in constructing SQL queries, but their incorrect utilization or bypassing can lead to vulnerabilities.
3. Dynamic SQL Query Generation
When SQL queries are dynamically constructed on the basis of user inputs without parameterization, it creates chances of SQL vulnerabilities. If input is not appropriately validated, attackers can inject their own SQL commands. Let's take a prime example: they could input something like "DROP TABLE users; --`, potentially causing unintended actions on the database.
4. Inadequate Input Validation
Avoiding strict validation and sanitization processes of user inputs before using them in SQL queries can leave applications ready to be exploited in front of SQL injection attacks, which results in many unavoidable web app security vulnerabilities.
5. Insufficient Error Handling
Error messages returned from databases operations could sometimes expose SQL query structure or any other sensitive information for that matter. This helps attackers in executing SQL injection payloads.
Common Examples of SQL Injection Attacks
Let’s get into details of common examples of SQL injection attacks that exploit Node JS vulnerabilities and misuse sensitive data.
1. Login Bypass
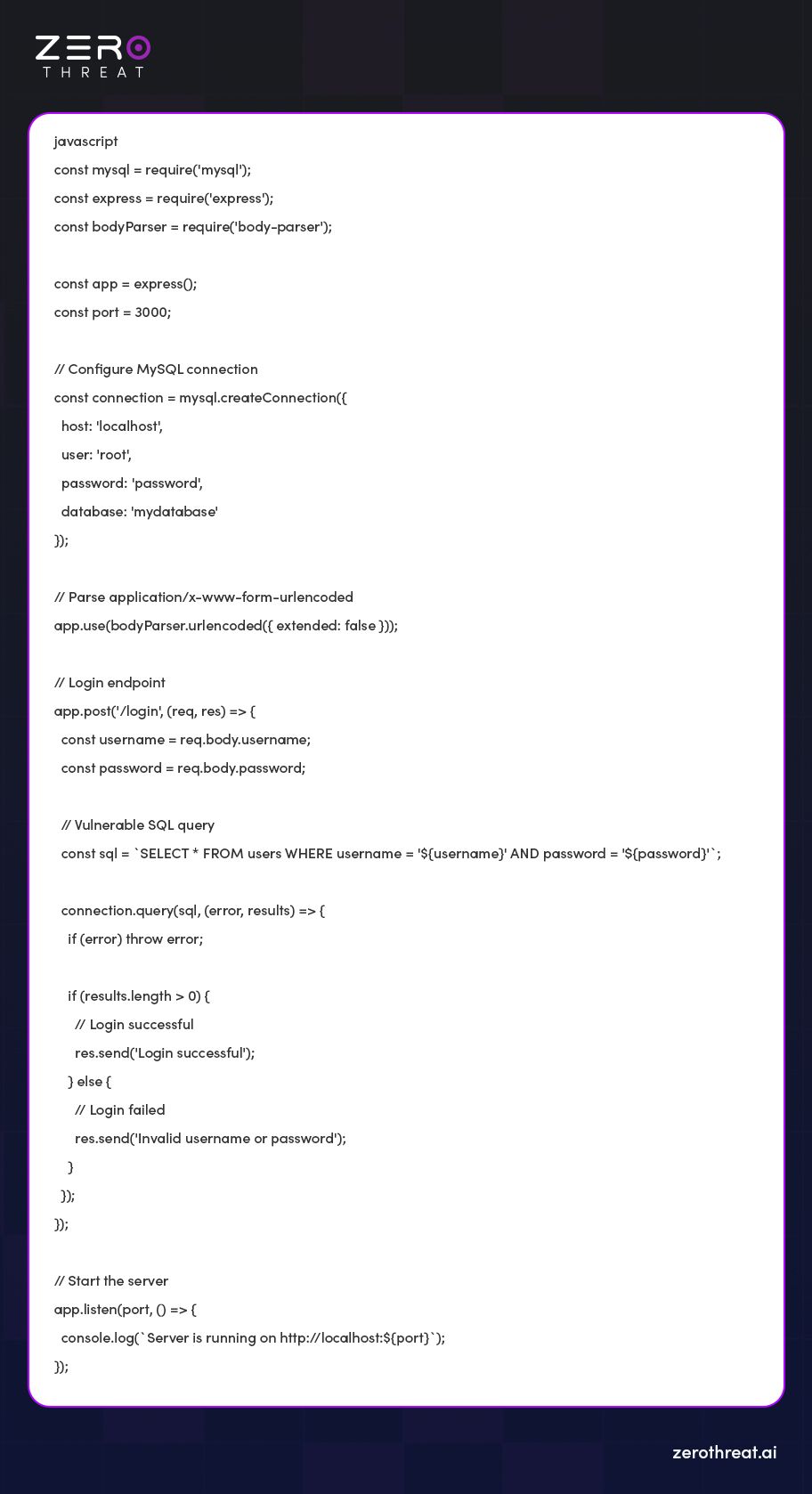
Let’s check the example of a vulnerable code.
Express Setup: Initializes an Express web server (`app`) on port 3000.
My SQL Connection: Connects to a MySQL database (`mydatabase`) on localhost with credentials (`root`, `password`).
Middleware: Uses `body-parser` to parse incoming `application/x-www-form-urlencoded` data.
Logic Endpoint: Defines a POST route `/login` to handle user login attempts.
SQL Query: Constructs a vulnerable SQL query to check user credentials (`username` and `password`) against entries in the `users` table.
Response: Send “Login Successful” if credentials match; otherwise, sends "Invalid username or password".
Server Start: Starts the Express server, listening on port 3000.
Attackers can misuse this vulnerable code by entering a crafted input like OR '1'='1` in both fields.
The resulting query becomes
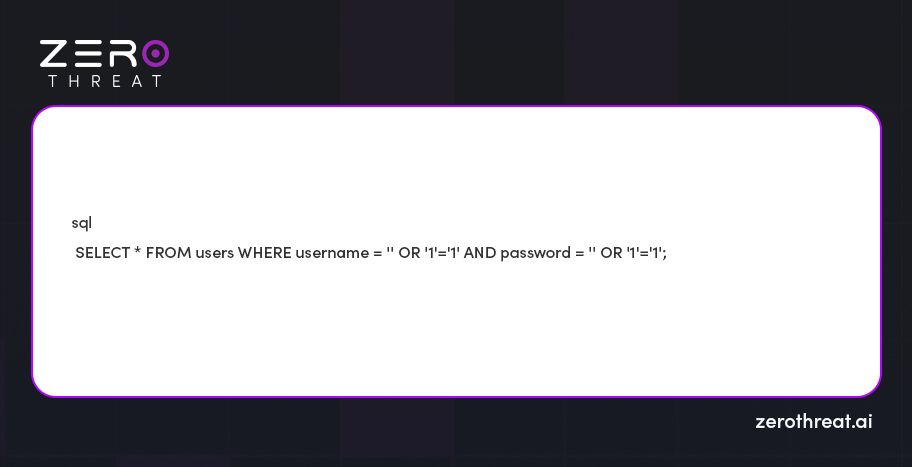
Since `'1'='1'` is always true, the query will return to the first user it captures by effectively bypassing the login check.
2. Retrieving Sensitive Data
Imagine a search feature designed to retrieve user details based on a specified search term.
Let’s check out the vulnerable code.
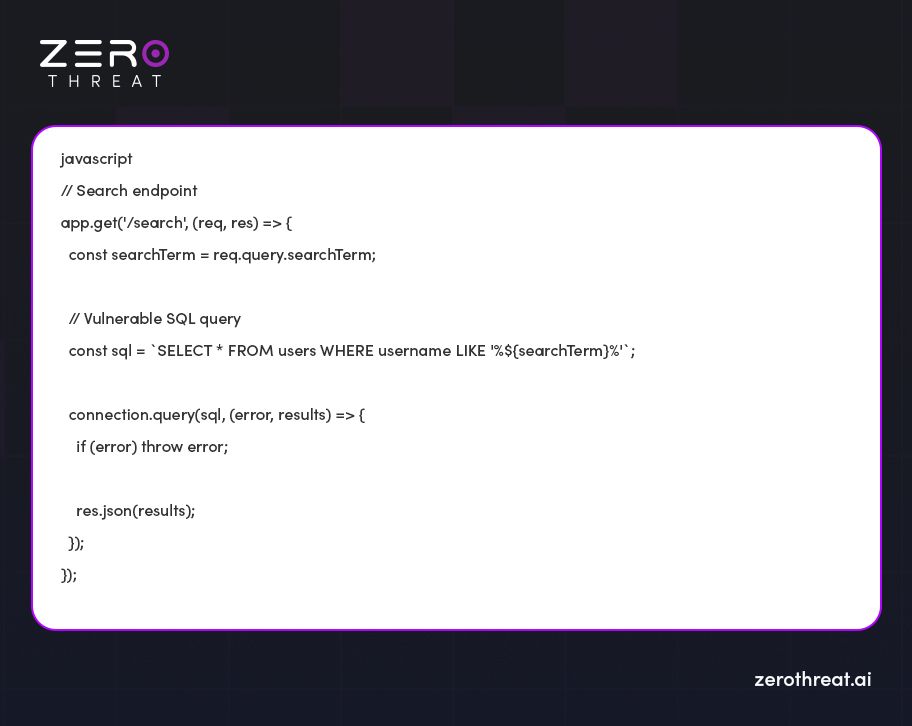
Explanation of Vulnerable Code
In this vulnerable code the “searchterm” variable is directly into the SQL query string with the help of `%${searchTerm}%`.
Attackers can also manipulate the “searchterm” to inject additional SQL commands.
Let’s take an example: Entering `%' UNION SELECT password, 'hack', null FROM users-- ` as `searchTerm' will result in a query that recovers passwords from the ‘users’ table along with the genuine search results.
Security Practices to Follow to Prevent SQL Injection in Node JS
Let's explore detailed methods for preventing SQL injection in Node.js applications to protect them from sophisticated attacks.

1. Use Parameterized Queries
Parameterized queries are quite effective in preventing SQL injection attacks. They separate SQL logic from data inputs to ensure that user-supplied values are perceived just as data and instead of executable SQL code.
Code Example `pg` (PostgreSQL client for Node JS):
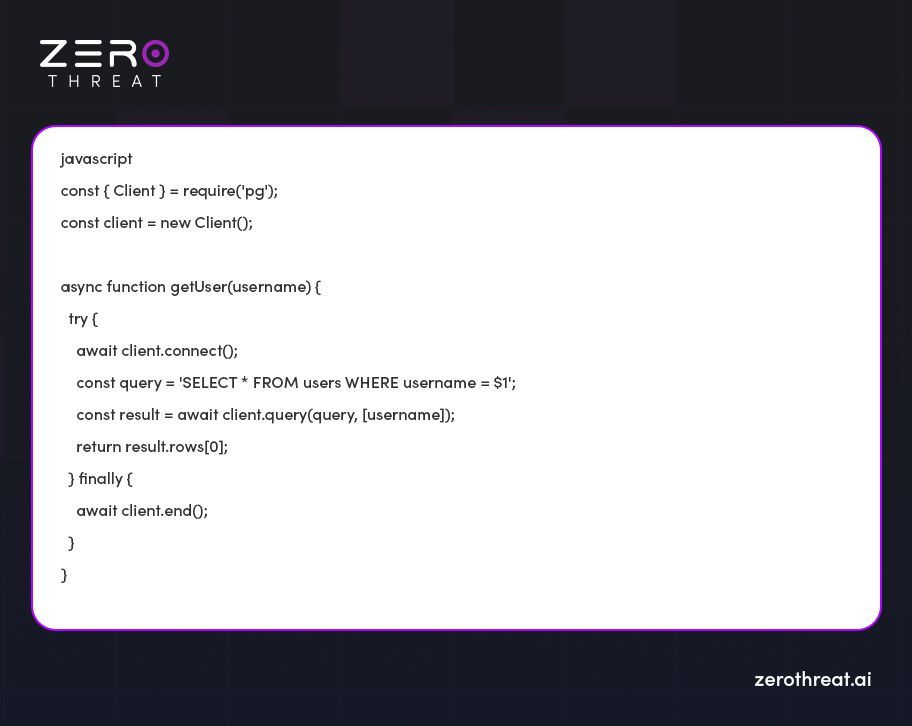
Code Explanation
`query` is parameterized with `$1`, which is equivalent to the `username` parameter.
In `client.query` method, parameterization is handled by ensuring that the `username` value is perceived as a parameter rather than executable SQL code.
2. Optimize ORM (Object-Relational Mapping)
ORM frameworks like Sequelize or TypeORM offer abstraction layers that automate the process of handling SQL queries and parameterization. ORM libraries create safe SQL queries on the basis of JavaScript objects which significantly decreases the risk of SQL injection vulnerabilities.
Let’s take an example using Sequelize:
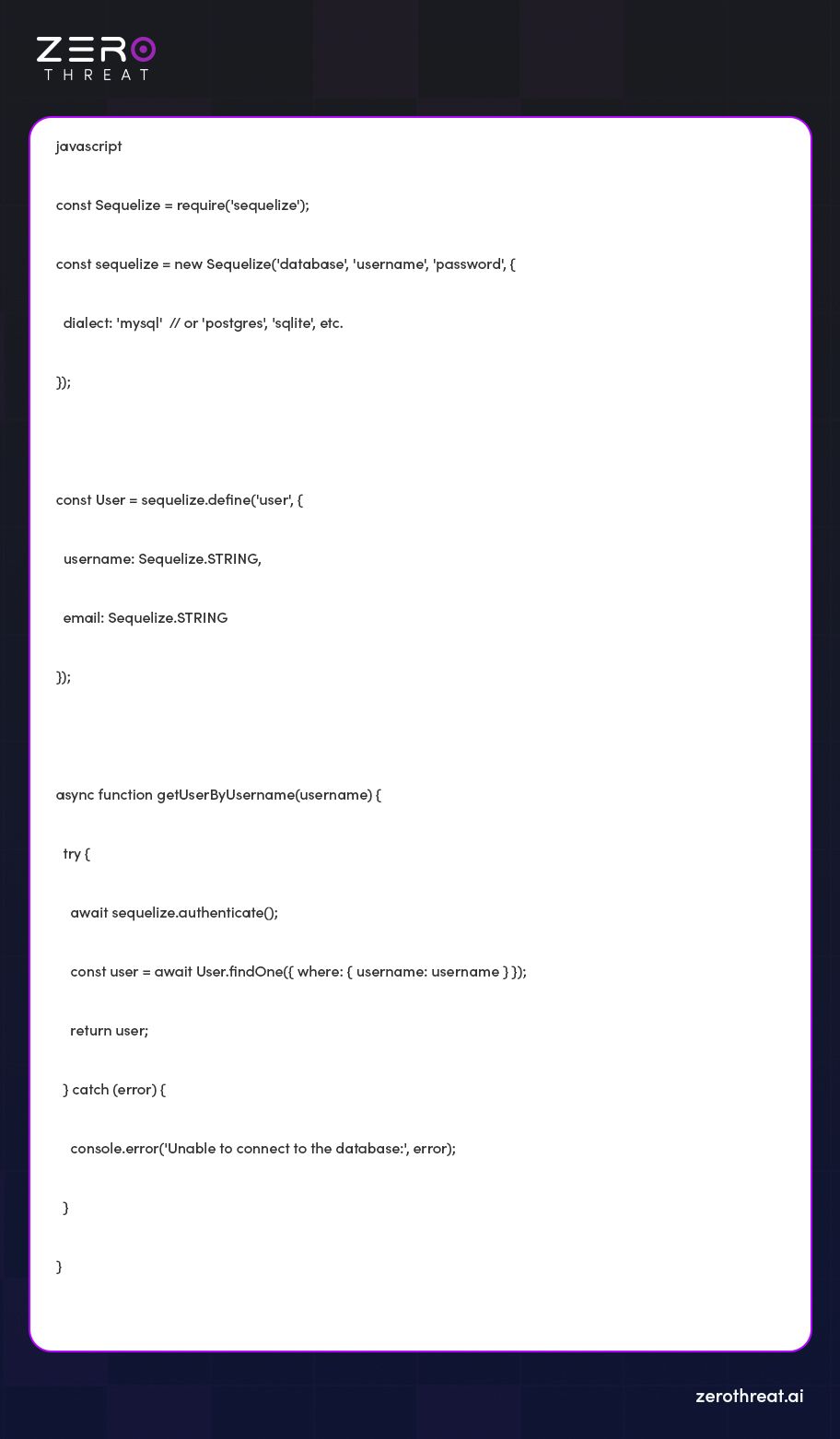
Code Explanation
In this example the `findOne` method automatically creates a parameterized SQL query on the basis of `where` condition (`{ where: { username: username } }`) which ensures that `username` is treated securely.
3. Input Validation and Sanitization
Validating and sanitizing user inputs helps in ensuring that they adhere to expected formats without containing harmful content or files. Deploy libraries such as express validator for powerful input validation.
Let’s take an example using `express validator`
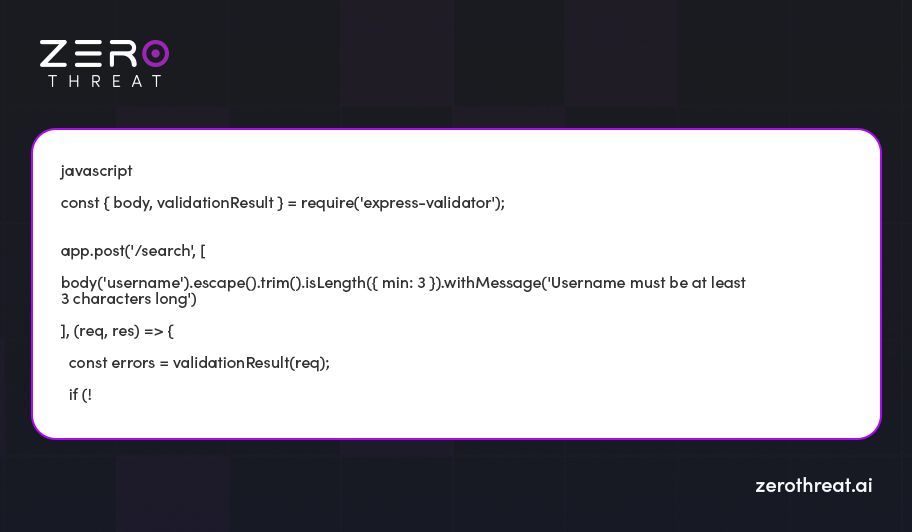
4. Escaping User Inputs
Escaping user inputs while building dynamic SQL queries manually adds an extra layer of protection against SQL injection attacks. Libraries like `sqlstring` (for MySQL) or `pg-format` (for PostgreSQL) help manage potential vulnerabilities in web apps. Additionally, a using a web application vulnerability scanner can help you detect and address these security concerns effectively.
Let’s take an example `sqlstring` for MySQL
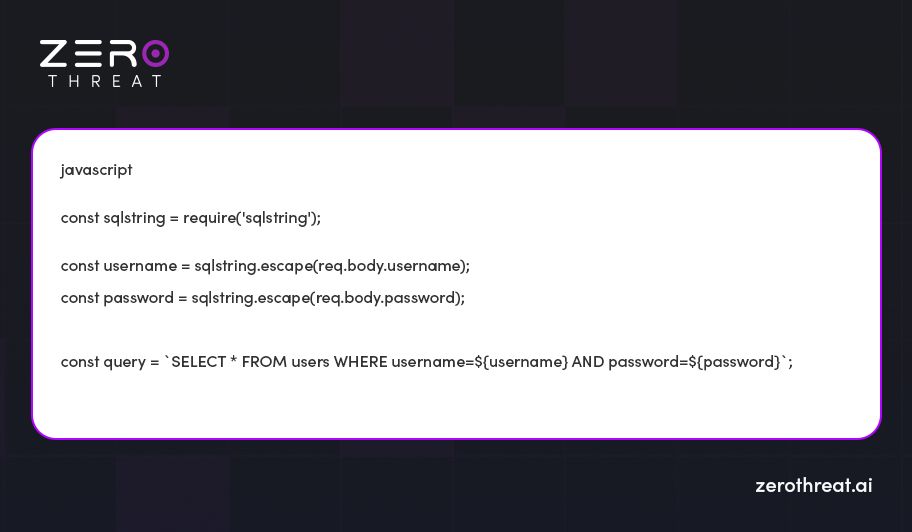
5. Implementation of other Database Security Best Practices
Enforce secured configuration to manage your database and to alleviate web app security risks associated with SQL injection attacks.
Implement strong authentication; avoid using lenient passwords and adopt multi-factor authentication (MFA) for database access.
Ensure consistent monitoring and logging to keep track of web app’s security and detect abnormal activities.
Implement a database firewall to restrict unauthorized access and capture anomalies.
Deploy Best Vulnerability Scanner for your Web Apps to Detect All the Sophisticated Vulnerabilities and Threats at 0 Cost Hunt Them Down
Harness ZeroThreat to Prevent Node JS SQL Injection Attacks
SQL injection attacks can cause noteworthy damage to your Node JS applications if they meet potential vulnerabilities present in your web applications. That's why we've diligently curated some powerful security practices to prevent SQL attacks. By giving this blog a read, you must have learned in detail about SQL injection attacks and practices to implement for their avoidance.
Remember that security is an ever-evolving process, and staying vigilant against sophisticated threats is key to maintaining the integrity and security of your applications.
Also, ensure using the best vulnerability scanner to enforce steadfast security measures by scanning all types of vulnerabilities that are harmful to your web apps and APIs. We've one such tool to offer you that takes care of all your security issues to the core, and that too for free: ZeroThreat! Try this tool and see the surprising results.
Frequently Asked Questions
What are the different types of SQL injection attacks?
There are total 8 types of SQL injection attacks:
- Classic SQL Injection
- Blind SQL Injection
- Error-based SQL Injection
- Union-based SQL Injection
- Time-based Blind SQL Injection
- Out-of-band SQL Injection
- Second-order SQL Injection
- Function Call Injection
What are the multiple vulnerabilities in node JS?
What is injection in node.js?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.



