All Blogs
Quick Summary: How to secure your web application from ever-growing security threats is the question that pops up in every business owner's mind. Here's when you need to uncover the concept of threat modeling and optimize it. But why and how? Relax, just read this blog, which includes comprehensive information about threat modeling. We're sure your search for robust security for your web application will cease with this guide.
Are you aware that businesses worldwide are ramping up their cybersecurity budgets? It’s no surprise, given the increasing sophistication of cyberattacks. In fact, Gartner says, global spending on information security is expected to reach $212 billion in 2025, marking a 15.1% increase from 2024’s $183.9 billion.
This surge in investment highlights the urgent need to combat cyber threats, especially those targeting web applications. That’s why we’re committed to providing you with effective security solutions. Today, we’re diving into threat modeling, a crucial strategy for securing your web apps.
Stay with us to uncover valuable insights on implementing robust threat modeling practices and fortifying your web app security.
Tired of Searching for Robust Web App Security Solutions? Your Search Ends Here Sign Up For Airtight Security
Table of Contents
- What is Threat Modeling?
- Understanding the Threat Modeling Process
- Seven Effective Threat Modeling Examples
- Top Five Threat Modeling Tools
- How Can You Enhance Your Web App Security with ZeroThreat?
What is Threat Modeling?
Threat modeling is the process that allows organizations to discover security loopholes in the system of web apps. With threat modeling, organizations can determine critical areas of the system that should be safeguarded and identify weak spots that are more likely to be vulnerable to security threats. It also helps in defining the security measures that should be enforced to enhance the entire security structure of web apps.
Understanding the Threat Modeling Process
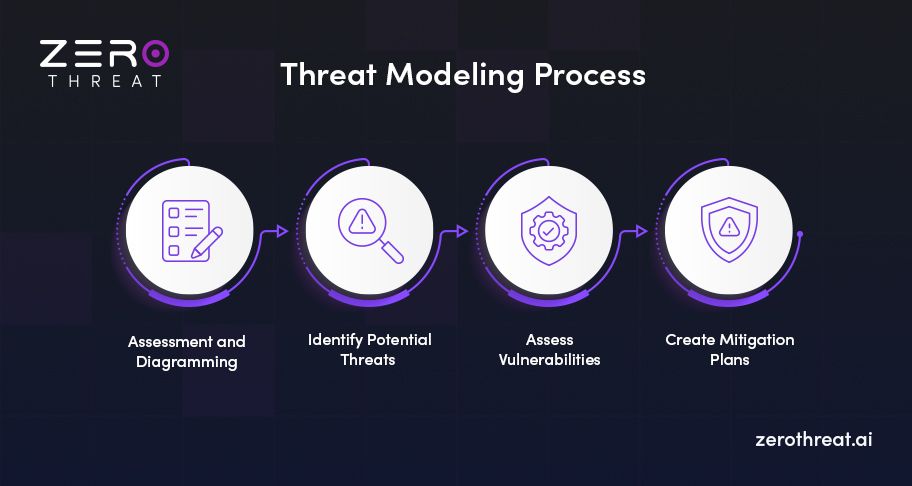
It’s essential to understand how threat modeling works in securing web applications before implementing it. Take a look at how threat modeling operates and its importance in identifying and mitigating potential security risks.
Assessment and Diagramming of Web Apps
The first and foremost step is having a clear understanding of the system's architecture, including all the components and data flows.
Diagramming application systems helps organizations understand which are the crucial spots that are more likely to be exploited, such as sensitive data, critical functionalities, and user interactions.
Identify Potential Threats
Discover different types of potential threats that are more likely to affect web applications. This includes attacks such as unauthorized access, data breaches, and denial-of-service attacks.
Optimize threat modeling frameworks like STRIDE or DREAD to carry out extensive identification and categorization of these threats.
Assess Vulnerabilities
Once you have appropriately examined the system, check for weak spots where the chances of vulnerabilities are higher. Once detected, examine each of the vulnerabilities and prioritize fixing them on the basis of their potential impact on the system.
Create Mitigation Plans
Create suitable strategies to act upon identified threats and vulnerabilities. This could include applying security controls such as encryption, access controls, and input validation. Enforce these strategies within the system to alleviate the risk effectively.
7 Effective Threat Modeling Examples
Now that you know the standard process of threat modeling, there are certain frequently optimized threat modeling framework examples that you must know about. Let's check them out.
S.T.R.I.D.E
- Spoofing: Identify deception or simulation
- Tampering: Unauthorized alteration of data
- Repudiation: Denying actions or transactions
- Sensitive Data Disclosure: Unauthorized access to confidential data
- Denial of Service (DoS): Disrupting service availability
- Elevation of Privilege: Obtaining unauthorized access to higher privilege
The STRIDE methodology is optimized as a framework in Microsoft's threat modeling tool. With its application, organizations can effectively examine every aspect of the system to detect threats and perform efficient security measures to minimize these risks.
P.A.S.T.A (Process for Attack Simulation and Threat Analysis)
PASTA is a kind of threat modeling methodology that impersonates actual attacks to discover and assess potential security vulnerabilities and threats. It is covered in mainly 7 stages.
- Stage 1: Defining goals and scope
- Stage 2: Defining the technical scope
- Stage 3: Application decomposition and examination
- Stage 4: Threat identification and examination
- Stage 5: Vulnerability assessment
- Stage 6: Attack modeling and imitation
- Stage 7: Risk identification and management
O.C.T.A.V.E. (Operationally Critical Threat, Asset, and Vulnerability Evaluation)
O.C.T.A.V.E. is a threat modeling framework or methodology that emphasizes analyzing organizational and operational risks. O.C.T.A.V.E. allows businesses to understand and handle risks by focusing on safeguarding assets and operational considerations. Check out its phases.
- Phase 1: Create asset-based threat profiles
- Phase 2: Recognize infrastructure vulnerabilities
- Phase 3: Create threat scenarios and discover their impact
Attack Trees
With this threat modeling technique, organizations can create a tree-like diagram where each node represents a potential attack or threat. Businesses can break down high-level attacks into sub-attacks to understand the paths and methods that could be used to exploit the security.
V.A.S.T (Visual, Agile, and Simple Threat)
This threat modeling framework mainly focuses on integrating threat modeling into agile workflows and optimizing visual tools to rationalize the process.
- Visual: Optimize visual diagrams to represent the system and key security threats.
- Agile: Incorporate threat modeling frameworks into development processes
- Simple: Ensure keeping it simple and clear to make threat modeling accessible and viable.
L.I.N.D.D.U.N
LINDDUN is a threat modeling methodology that primarily emphasizes privacy threats and helps in analyzing privacy risks and impacts. Check out how.
- Linkability: The ability to link multiple aspects of data to the same user
- Identifiability: Identification of entities on the basis of data.
- Non-repudiation: Ensuring that actions cannot be opposed by users.
- Detectability: Detection and identification of events and actions
- Exposure of Data: Unauthorized access to sensitive information
MITRE ATT&CK
MITRE ATT&CK helps organizations by providing an extensive framework for understanding and defending against real-world attack techniques. See its key features below.
- Adversarial Strategies: Understand the various tactics that adversaries might use, such as initial access or execution.
- Techniques and Process: Recognize particular techniques and processes that are used to perform tactics.
- Mapping and Detection: Map these tactics and techniques to the system to assess potential weak spots.
Let ZeroThreat Be the Escort of Your Web Apps to Keep Security Attacks at Bay Take a Tour
Top 5 Threat Modeling Tools
Check out some of the highly used tools to perform the threat modeling process in an ideal manner.
Microsoft Threat Modeling Tool
Microsoft threat modeling is known for its simplicity and easy usage, which allows organizations to generate data flow diagrams and recognize threats using the STRIDE methodology. It provides a comprehensive approach to threat modeling and seamlessly integrates with other Microsoft tools.
O.W.A.S.P. Threat Dragon
An open-source threat modeling tool that supports the creation of threat models and visualizes potential threats by using diagrams. It runs according to standard O.O.W.A.S.P.'security practices and is useful for integrating with agile development processes.
ThreatModeler
ThreatModeler is an extensive threat modeling tool that offers automated threat analysis and risk assessment. It allows businesses to build detailed threat models and smoothly integrate them with other security tools for continuous risk management.
IriusRisk
IriusRisk is a threat modeling platform that enables users to design and examine threat models by offering integration with multiple development and security tools. It supports different methodologies and helps with comprehensive risk assessments and mitigation strategies.
CAIRIS
CAIRIS is an open-source threat modeling tool with many excellent features. It supports DREAD, STRIDE, and PASTA methodologies. It automates threat model generation, attack tree, and data flow diagrams.
Let Our DAST Tool Handle Your Web App Security with Its Steadfast Protection Go For It
How Can You Enhance Your Web App Security with ZeroThreat?
In web app security, there are many techniques that contribute through their specific character traits and ensure the security becomes more robust. In a nutshell, web app security is a collective effort of many threat modeling techniques, one of which is threat modeling.
In this blog, you learned how threat modeling and threat modeling tools and frameworks play a massive role in making web app security steadfast. And we are sure you will optimize the concept of threat modeling in cybersecurity to conquer potential threats.
But, to fast-track and streamline the process of scanning potential vulnerabilities and other cybersecurity threats, automation is indispensable. Hence, we present to you ZeroThreat: an automated next-gen AI tool for carrying out accurate scanning and vulnerability detection for web applications and APIs, which ensures 98.9% accuracy at $0 cost!
Are you up for trying this blazing-fast DAST tool that helps you detect all kinds of hidden vulnerabilities in a jiffy? Sign Up now.
Frequently Asked Questions
How can you identify threats through threat modeling?
Threat modeling detects security threats by mapping out an architecture, pinpointing vulnerabilities, and evaluating potential attack vectors to prioritize security measures.
What are the advantages of the threat modeling process?
What are the disadvantages of the threat modeling process?
Is threat modeling effective for web app security?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


