All Blogs

Quick Summary: Choosing a good vulnerability detection tool is essential for identifying and fixing vulnerabilities. But it can be a bit tricky if you don’t know where to start. Look for the must-have features in this blog to pick the right tool to manage vulnerabilities efficiently and secure your assets.
Vulnerability detection and remediation aren’t merely tasks; they are necessary to safeguard your data and assets. It becomes even more crucial when there is a constant rise in cyberattacks. But there is a catch – finding and choosing the right vulnerability detection tool can be tricky.
It’s like finding a needle in a haystack. In that scenario, you must be careful which tool you choose. Remember, vulnerabilities are the primary cause of cyberattacks , and a mediocre tool may fail to discover all weaknesses that increase your chances of being a victim.
There are multiple factors to consider before choosing a vulnerability detection tool, such as accuracy, compatibility, scalability, performance, and more. We have curated a list of the most essential expert-guided considerations that you should keep in mind to make the best choice.
Let’s check them out without further ado!
Scan for 40,000+ Vulnerabilities and Secure Your Web Apps – Fast, Simple, and Accurate Scanning! Choose Preferred Plan to Scan
On This Page
- An Overview of Vulnerability Detection Tools
- Key Features to Look for in a Vulnerability Detection Tool
- Top Tools for Vulnerability Assessment
- Important Tips to Choose a Vulnerability Scanner
- Final Thought
A Short Sketch of Vulnerability Detection Tool
A vulnerability detection tool is a kind of software that helps analyze applications, networks, and systems for known vulnerabilities such as cross-site scripting, SQL injection, broken authentication, misconfigurations, encryption failure, etc.
These tools scan, prioritize, and report vulnerabilities in an actionable format that allows developers and security teams to fix issues promptly. They also automate security testing within SDLC to identify and report vulnerabilities in real time as applications are built and tested.
Top Features to Look for in a Vulnerability Assessment Tool
Organizations must look for the essential features in a vulnerability detection tool, as mentioned below, before making a decision. Let’s discuss these essential security features in detail.

Depth of Scanning
The core power of a vulnerability detection tool is the depth and breadth of scanning. It determines the effectiveness of the tool and its capability to discover a wide range of vulnerabilities. A good vulnerability scanning tool offers a comprehensive analysis that will lead to more accurate and actionable results. Hence, vulnerability coverage is an important feature of a vulnerability scanner you must look for.
You should rely on a tool that goes beyond the OWASP top 10 and scans for more complex vulnerabilities such as out-of-band, zero-day, sensitive data exposure, business logic flaws, and more. Besides, you can choose a tool that also offers secret scanning that checks for sensitive data like passwords and API keys that may be exposed in configuration files, repositories, or other sources.
Scanning with Credentials
One of the most important security features that you can find in a good vulnerability scanner is both non-credentialed and credential-based scanning. What’s the difference? Non-credentialed, also known as unauthenticated scanning, involves vulnerability assessment without providing user credentials or accounts.
Unauthenticated scanning is conducted from an external perspective because it checks an application, system, or network from the public-facing interfaces. It focuses on identifying vulnerabilities like open ports, unpatched software components, misconfigurations, and more.
On the other hand, credentialed, also known as authenticated scanning, requires a valid user account or login credentials to initiate a scan. The main focus of such scanning is to identify internal security threats that may be posed by a disgruntled employee with credentialed access.
Authenticated scanning analyzes pages or resources protected behind the login. Moreover, both authenticated and unauthenticated scanning, when combined, not only help you discover common security weaknesses but also uncover deep-rooted vulnerabilities.
Compatibility and Scalability
Compatibility with your existing security tools and technologies is also a crucial requirement. Many vulnerability detection tools are not able to scan applications that use JavaScript heavily, such as single-page applications (SPAs), or they don’t support specific frameworks and programming languages.
So, it’s essential to make sure that the tool you are eyeing is compatible with the tools and technologies your application is using.
Secondly, you must also check the scalability of the tool to ensure it supports your growing business needs. A tool should be capable of adapting to growing complexity and scanning requirements. So, whether you want to scan a single app or hundreds of apps, it must handle the tasks efficiently.
Performance and Integration
In Agile environments, speed matters, and security testing needs to match the pace of new releases. If application changes are released more frequently, you need a vulnerability scanner that can perform tests within a few minutes to maintain the momentum.
In that scenario, the best vulnerability scanner for you is one that offers faster scanning and results. Apart from this, the tool should easily integrate into your CI/CD pipeline to automate security scans at every build and detect vulnerabilities early in the development phase.
Intuitive Interface and Quick Setup
As you would expect, this good tool has a great user-friendly interface and quick setup that helps with the seamless scanning and detection of vulnerabilities. So, one of the top features of a vulnerability scanner is a clean and user-friendly dashboard that can be easily navigated.
A simple dashboard with centralized information helps manage everything easily and encourages prompt actions. Plus, anyone can easily perform scans without prior technical skills. Both easy setup and intuitive interface reduce the complexity and time required for vulnerability management.
Detailed and Actionable Reports
An essential feature of a security scanner is its ability to generate comprehensive and actionable reports. A good tool doesn’t just provide a list of vulnerabilities it has identified; it offers a clear view by prioritizing vulnerabilities based on severity, business risk, compliance, and other factors.
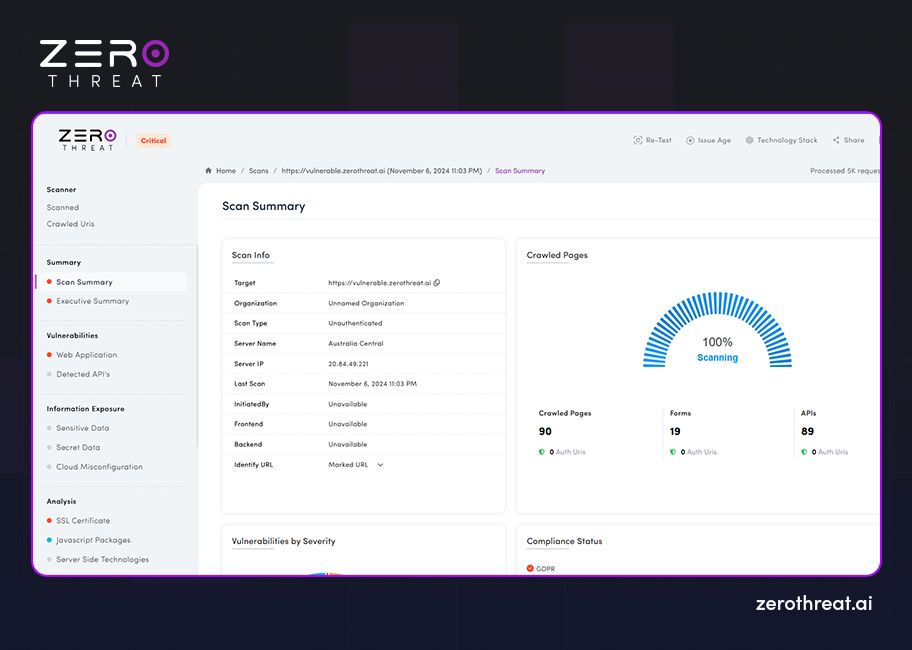
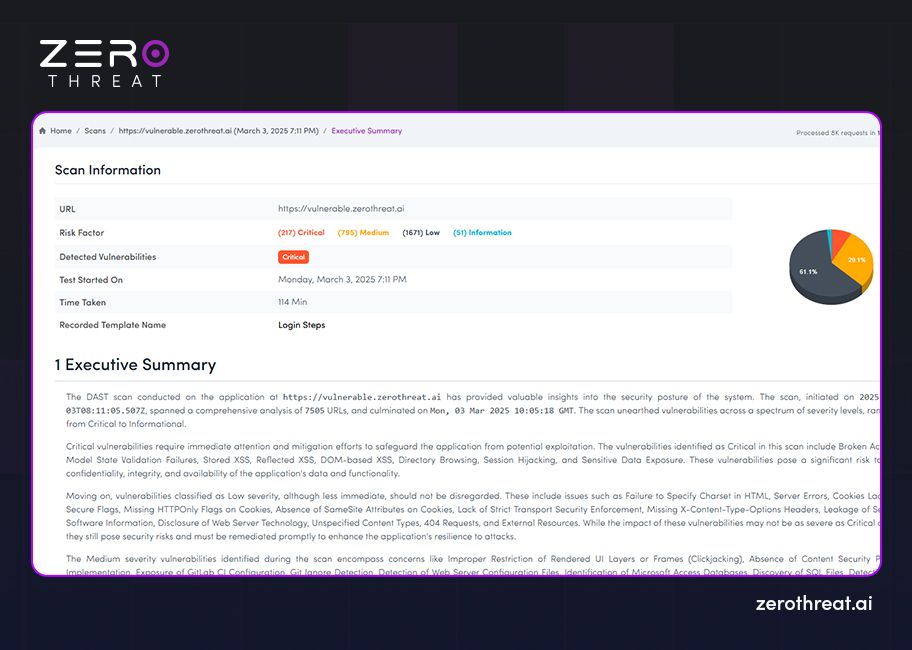
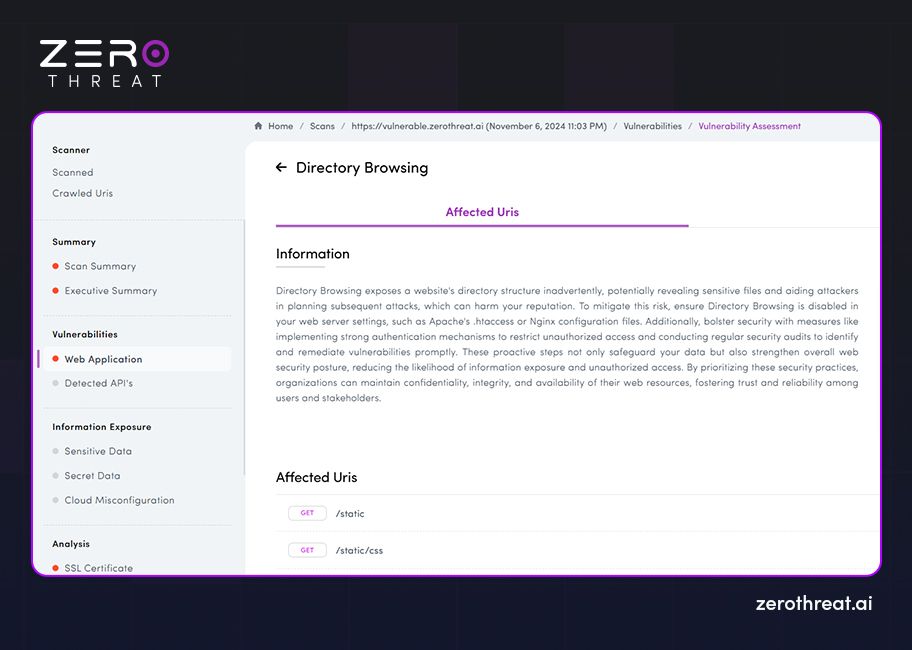
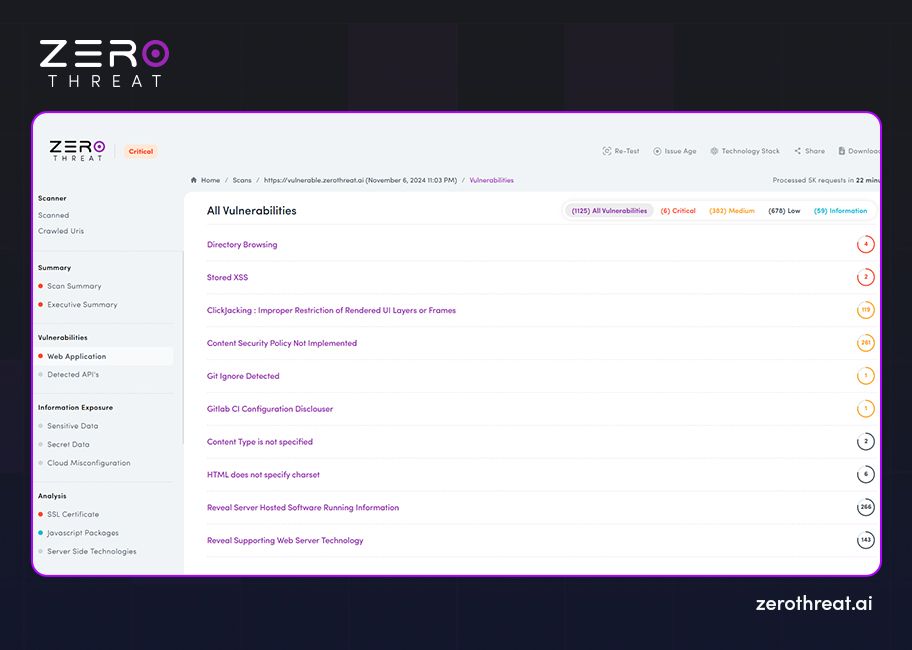
Besides, the tool offers actionable remediation guidance or suggestions to fix the security loopholes it has identified. A typical scan report provides information like the number of scans, scan summary, executive summary, detected vulnerabilities (prioritized: Critical, Medium, Low, CVSS risk score), detailed vulnerability insights, and recommendations for remediation.
Besides, the tool should also offer compliance reports to help easily discover any issues and fix them to meet regulations like HIPAA, PCI DSS, GDPR, etc. The following are screenshots of sample scan reports from the ZeroThreat vulnerability scanner.
Automated Scanning and Alerts
Automated scanning and real-time alerts are among the must-have features of vulnerability assessment tools. Besides, they must automatically discover APIs, web apps, and other target assets to conduct scans for vulnerabilities. Automated scanning helps in continuous vulnerability assessment.
Also, look for scheduled scanning that enables you to set up automated scans at specified intervals, like every week, every month, or even every day. With continuous automated scanning, you can discover vulnerabilities early before a hacker finds them and take timely actions to mitigate risks.
When the tool is integrated into your development environment, it provides real-time notifications once a vulnerability is detected and triggers quick responses to fix it.
Accuracy and Low False Results
Low false results and accuracy are essential vulnerability scanner features that correspond to its ability to detect vulnerabilities with the highest accuracy and lower false positives. Both these features play a vital role in the quality of vulnerability assessment.
You won’t like to spend your resources on vulnerabilities that don’t exist. It will only waste your time and resources. Hence, picking a tool that generates a lower number of false positives and offers accurate detection is essential to get quality results. It will prevent alert fatigue and let your team focus on actual risks.
Top Vulnerability Detection Tools for Organizations
Which vulnerability scanning tool is best for you? Well, the answer to this question is subjective because it depends on the specific requirements of organizations. Nevertheless, the following are the top tools for vulnerability scanning that you can use to identify and remediate security weaknesses. Each of these tools has top-notch security features that help you protect your web apps, APIs, and other digital assets from a wide range of cyberattacks.
- ZeroThreat
- Nmap
- W3af
- ZAP
- Acunetix
- OpenVAS
- Nessus
- Burp Suite
- Rapid7
How to Choose the Right Vulnerability Scanning Tool?
Choosing a vulnerability scanner may be confusing, given so many options and the variety of tools. Therefore, you need to carefully compare different options to pick the right tool. The following steps will help you make the best choice.
Know Your Requirements
Start by understanding your needs. Find out which asset you want to scan, like a web application, network, database, API, etc. Determine the type of scanning you want – for example, you need a SAST tool to examine source code and a DAST tool to test applications at runtime. Consider other factors like compliance requirements, technologies used, and specific vulnerabilities to be addressed.
Frequency of Scanning
How frequently do you want to perform vulnerability scanning? Many scanners allow scheduled scanning, which enables you to perform scans at regular intervals or on a specific day every month or week. But many don’t have such a feature. Hence, look for options that align with your requirements.
Features vs Ease of Use
Would you prefer features over ease of use or vice versa? It is possible that a vulnerability detection tool has advanced features but is not user-friendly. Similarly, the opposite is also possible. However, you can also find tools that offer a balance between these two characteristics. Depending on your team’s skill, you should invest in the tool that aligns with your requirements.
Budget
Businesses with sufficient budgets can invest in high-end vulnerability scanning tools that offer top-notch features. However, if your business is struggling with funds or has a limited budget, you can invest in free vulnerability scanning tools. These tools have zero costs and offer excellent features to perform vulnerability scans.
Secure Every Application Before It Reaches Production and Stay Ahead of Hackers – Catch Vulnerabilities with 98.9% Accuracy! Get Started Now
Final Thought
Vulnerabilities are critical security risks that can be effectively tackled with continuous and real-time security assessments. Choosing the right vulnerability detection tool wins half the battle in this case, which helps you identify critical vulnerabilities with pinpoint accuracy
From scanning and prioritization to remediation of risks, vulnerability scanners automate tasks and simplify the overall process to secure your web apps, networks, and systems. You can reduce your manual efforts and speed up vulnerability assessment by choosing the modern vulnerability scanner – ZeroThreat.
With its advanced DAST capabilities, you can scan web apps and APIs for 40,000+ vulnerabilities. It offers a next-gen crawler and actionable AI-powered remediation reports. It is fast, accurate, and user-friendly, which makes vulnerability scanning a breeze. With seamless integration into CI/CD pipelines, developers can catch vulnerabilities in SDLCs.
ZeroThreat goes beyond the OWASP top 10 and discovers out-of-band, zero-day, and other complex vulnerabilities without requiring additional settings or extensions. Give it a try and see all its benefits live.
Frequently Asked Questions
Which are the most popular vulnerability scanners?
There are many popular tools for vulnerability scanning used by organizations; some of them are given below.
- ZeroThreat
- ZAP
- Acunetix
- Burp Suite
- Nessus
What are the different types of vulnerability detection tools?
Why is a vulnerability detection tool important?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.