All Blogs

Quick Summary: What is cybersecurity audit and why is it so important for organizations? It is essential for organizations to protect from cyber threats that can threaten the security and integrity of their systems and applications. Keep reading to know everything about it in this blog.
Cybersecurity audit is being widely adopted by organizations today to defend against rising cybercrimes. It helps them assess their digital assets and discover weaknesses that attackers can exploit to compromise security. As per Statista's report, the cost of cybercrime stands at $9.22 trillion worldwide today. It indicates an alarming situation for organizations.
So, there is an urgent need for a robust cybersecurity strategy. A cyber security audit is a vital part of this strategy that helps ensure a proactive measure against cyber threats. It helps organizations improve their security posture and prevent potential data breaches. In this blog, we are going to cover cyber security audits in detail to help you understand their importance in protecting an organization from cyber threats.
Uncover Cyber Security Threats in Minutes to Protect Digital Assets Proactively Scan Now
Table of Contents
- Understanding Cyber Security Audit in Detail
- Importance of Cyber Security Audits
- Differences of Internal and External Cybersecurity Audits
- Steps to Perform Cyber Security Audit
- Areas Covered by a Comprehensive Cyber Security Audit
- To Wrap Up
Understanding Cyber Security Audit in Detail
In simple words, a cyber security audit is a thorough analysis of your information assets from a security point of view. So, the evaluation of networks, applications, APIs, and other digital assets to discover any loopholes that might enable an attacker to gain unauthorized access to them is within the purview of the cyber security audit.
Just imagine there is a security flaw in your application, and it goes into production without getting noticed. It’s not hard to know what the impact could be. In case an attacker finds this flaw, your application could be hacked, or sensitive data could be stolen.
Cyber security audit helps discover these security loopholes or flaws before they become a potential threat to the application’s security. It involves a rigorous assessment of digital assets to uncover security threats.
Importance of Cyber Security Audits
Cybersecurity audits allow organizations to evaluate the current security posture and identify gaps that offer essential insights to boost the existing security mechanisms for enhanced protection. It offers many other advantages as shown in the following points.
Uncovering and Mitigating Risks
Cybersecurity audits aim to discover critical security vulnerabilities that increase the risk factor. This includes an assessment of vulnerable assets, potential threats to them, and security weaknesses that attackers can exploit. You can mitigate cybersecurity risks for your organization by identifying and assessing the threat landscape.
Protect Sensitive Data
Organizations often have sensitive data or information that they must protect from unauthorized access, destruction, modification, and disclosure. Implementing stronger security measures can be a way to protect the data. However, if there is any loophole in these measures, the data is always at risk. With a comprehensive security audit, these loopholes can be detected on time and prevent cybersecurity risks.
Enhance Security Posture
Security audits help organizations discover weaknesses in their current security controls and policies to help them improve overall security posture. By identifying gaps and improving them, your organization can create a better security shield against cyber threats.
Compliances and Regulations
Organizations can stay stress-free about compliances and regulations when security audits are conducted regularly. They can constantly update their security policies according to the changing standards and requirements of regulatory authorities by assessing their existing policies. Hence, cybersecurity audits are quite useful in compliance and regulations.
Gain Customer Confidence
Data security and privacy are important concerns for customers that your organization can address by conducting regular security audits. Your organization can demonstrate that you care about their data security and privacy with these audits.
Understanding the Differences of Internal and External Cybersecurity Audits
There are two options when it comes to conducting cybersecurity audits: internal and external audits. External security audits are performed by a third-party service provider. Cyber security audit services can be used to outsource the process and get the results without investing in resources.
On the other hand, internal security audits are performed by an in-house cybersecurity or IT team in an organization. There are distinct advantages and limitations of both internal and external cyber security audits.
Internal Audit:
- Internal security audits are more cost-effective because your organization need not invest in external resources.
- With a better understanding of your organization’s culture, processes, and internal systems, internal audits can offer a comprehensive assessment.
- Internal audits can effectively address the unique security challenges and requirements of your organization.
- Regular security assessments can be performed with internal auditing to continuously improve security posture.
External Audit:
- Since external security auditors are independent and not involved in your organization’s process, they can offer an unbiased security assessment.
- External audits help your organization align with regulations, compliances, and standards.
- With specialized knowledge and relevant experience, external auditors can effectively address security challenges.
Mitigate Security Threats with 98.9% Accuracy with AI-powered Security Assessment Check It Now
Steps to Perform Cyber Security Audit
Performing cybersecurity audits is a time-consuming and resource-intensive process that involves multiple steps. You must follow cybersecurity best practices to mitigate security risks. The following are the steps to perform a cyber security audit.
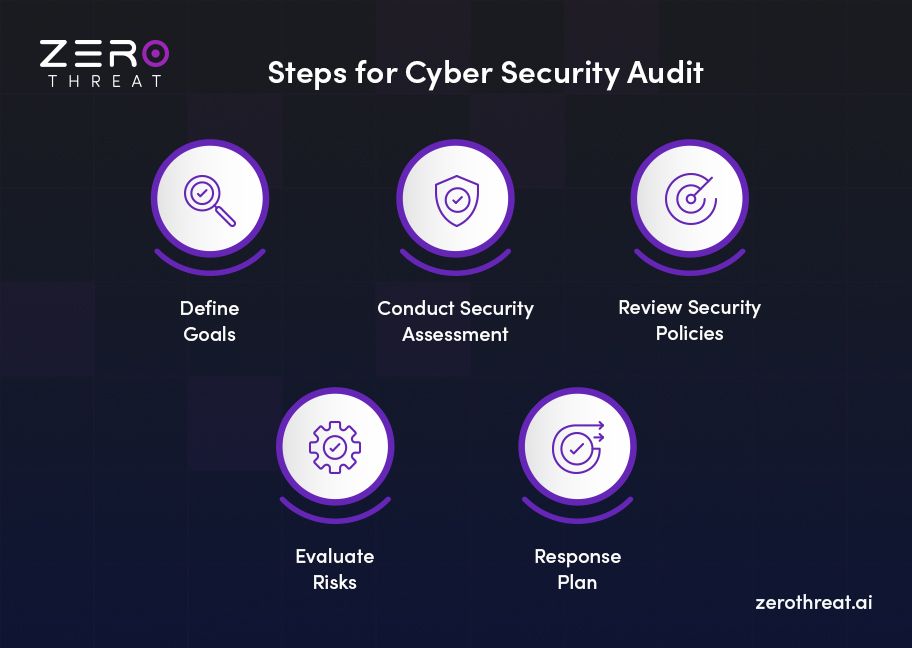
Define Goals
Start by understanding the clear goals and scope of the security audit. The auditor should have an understanding of the organization’s environment and risks. Identify the assets that need to be evaluated for vulnerabilities.
Conduct Security Assessment
Perform a comprehensive security assessment by analyzing your digital assets to discover vulnerabilities and threats to your organization. You can leverage an automated vulnerability assessment tool to discover loopholes and perform penetration testing to uncover more threats.
The following is a cyber security audit checklist of threats.
- Weak Credentials: Cybercriminals can use attacks like brute force to crack passwords. This happens due to weak passwords. Cybersecurity audits can help discover these weak credentials.
- DDoS Attacks: DDoS and DoS are types of cyberattacks in which an attacker overwhelms a system or application with excessive traffic or requests.
- Shadow APIs: APIs are pivotal for the digital systems of an organization as they facilitate communication between disparate systems. However, there are lots of APIs used in organizations that lead to the risks of shadow and zombie APIs. Security audits help discover shadow and zombie APIs to tackle the risks.
- Social Engineering: Today, social engineering has become a threat to data security that attackers leverage to trick users into divulging their information. With a thorough security assessment, you can check the cyber security readiness and employee awareness to defend against such threats.
- Insider Threats: It is another security threat for organizations that involve insiders like past employees. This type of threat occurs when an employee reveals secrets or confidential information to third parties to seek monetary gains or due to a grudge against the organization. Security audit helps protect against this threat by checking for weaknesses in authentication and authorization systems.
- SQL Injections: In this type of cyberattack, malicious code is injected into input fields of a web application to attempt unauthorized access to the database. With a security audit, potential vulnerabilities can be detected to thwart this threat to avoid a data breach.
- Zero-day Exploits: This is a type of vulnerability that is unknown and yet to be patched. Attackers can exploit this vulnerability to launch cyberattacks. With methods like dynamic application security testing, it is possible to discover these vulnerabilities and avoid cyberattacks.
Review Security Policies
Assess your existing security policies to identify flaws or gaps that might allow attackers to breach security. This assessment also includes the evaluation of security policies from a compliance point of view. Reviewing security policies can uncover various weaknesses and compliance issues.
Evaluate Risks
Risk evaluation is another step in cybersecurity audit that requires a thorough analysis of vulnerabilities and their potential impact on the organization. It involves prioritizing the vulnerability to identify the most critical threat to an organization.
Response Plan
After a thorough security assessment and identifying the potential threats to your organization, you can now create an incident response plan. It includes several activities as given below.
- A methodology to prioritize risks and remediation processes.
- A plan to ensure continuous business operations after a cybersecurity incident.
- Documenting the tools to detect, prevent, and respond to cyber threats deployed to protect systems.
- A communication plan entailing awareness for employees.
Areas Covered by a Comprehensive Cyber Security Audit
A cyber security audit offers a systematic approach to examine digital assets, identify vulnerabilities, and mitigate security risks. However, it varies depending on the size and type of organization. Yet, the following are the key areas that all cybersecurity audits focus on.
- Network Security: It involves evaluating the networking assets of an organization to identify weaknesses that might allow attackers to launch attacks like DDoS.
- Application Security: It involves auditing application security by evaluating controls like output encoding, input validation, IAM (Identity and Access Management), etc.
- User Security: Assessing the user security controls of an organization that is involved in this process. It helps evaluate how strong security controls are to protect users’ data and access rights.
- Policies for Information Security: Reviewing the information security procedures and policies is an important part of the security audit. It ensures that the measures to protect information are updated, comprehensive, and implemented properly.
Perform Continuous Threat Assessments to Discover Hidden Threats Precisely Let’s Hunt Them
To Wrap Up
Cyber security audit is an essential process for organizations to identify and mitigate security threats. It involves a comprehensive analysis of the digital assets of an organization to identify, mitigate, and prevent cyber security threats. However, you need a robust security testing tool to achieve the objectives.
ZeroThreat is a cutting-edge web app and API vulnerability scanner that can help security teams identify a wide range of CVEs, misconfigurations, and other security weaknesses. With an advanced AI-powered crawler, it can discover vulnerabilities with 98.9% accuracy and near-zero false positives.
ZeroThreat seamlessly integrates into CI/CD pipelines to streamline security audits within SDLC and ensure the delivery of secure applications. Try it now for free to see how it works.
Frequently Asked Questions
What is the role of audit in cyber security?
Auditing in cybersecurity is a process that involves evaluating the IT infrastructure, policies, and procedures of an organization. It aims to discover security weaknesses that can allow attackers to breach cybersecurity resulting in compromised data and information.
What are the main phases of a cybersecurity audit?
How is a cyber security audit different from an IT audit?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


