All Blogs

Brief Overview: Not able to decide which pen testing software to choose? Check important considerations recommended by security professionals to choose the right pen testing software. These considerations not only help you narrow down your choices but also highlight the key aspects you must keep in mind when making the decision.
Just like a soldier needs the right weapon to combat enemies, so does your security team need the right penetration testing software to secure your assets. What if they fail to identify a critical vulnerability just because the software they are using isn’t able to detect it. Result? An attacker may exploit that vulnerability and steal your sensitive data, while you believe there is no such risk.
Penetration testing tool is quite useful to discover vulnerabilities by simulating real-world attacks without human intervention. They are specialized cybersecurity tools designed to help security teams assess various assets for common and complex vulnerabilities.
Now the question arises – which software is right for your security team? There is a wide range of such software, each with its own pros and cons, so making a choice can be confusing. Therefore, we have come up with this blog to help you pick the right pen testing software for the security team.
This blog provides essential considerations and other important information to help you make a better decision. So, keep reading to make a correct choice.
Your Chances of Cyberattacks Double If Fail to Detect Vulnerabilities Accurately – Achieve 98.9% Accuracy with ZeroThreat and Avoid the Risk! Try Now for Free
On This Page
- What is Pen Test Software?
- Understanding the Importance of Pen Test Software
- Key Considerations to Choose Pen Testing Tool
- Best Tools for Penetration Testing
- Final Thought
What is Penetration Testing Software and How Does It Work?
Penetration testing software or tools perform automated simulated attacks on target applications, systems, or networks to discover security weaknesses. It works by mimicking various attack techniques like exploiting known vulnerabilities, social engineering, and DDoS.
These tools are often referred to as ethical hacking tools because they work like an ethical hacker who tries to identify and exploit vulnerabilities to discover security weaknesses. They mimic the ethical hacker’s techniques like reconnaissance, vulnerability assessment, and exploitation.
Some pen testing software replicates a hacker-like scenario, while other software examines vulnerabilities without affecting the production environment. However, they help in continuous security assessment to identify and fix vulnerabilities before an attacker can exploit them.
Understanding the Crucial Role of Penetration Testing Software
Pentesting software helps streamline vulnerability assessment and allows security teams to get instant alerts on vulnerabilities. Additionally, they also help meet compliance requirements. They are vital to understand your attack surface, prioritize remediation, and mitigate risks.
The use of different types of pen testing software will help your security teams to assess various assets and uncover critical vulnerabilities. In essence, pentest tool is vital to identify, prioritize, and mitigate security risks to improve security posture making your organization more resistant to cyber threats.
Key benefits of penetration testing software:
- Automation: These tools automate the process of penetration testing or vulnerability scanning that will otherwise take significant time.
- Reduce Cost: Automated penetration testing tools reduce the cost of the process because the pricing of tools is less than manual pen tests.
- Proactive Security: Using pentest software ensures proactive security because it can be used for continuous testing.
- Fast Results: While manual pen tests take a lot of time, your security team can easily scan and generate pen test reports in a few minutes or hours, depending on the app’s complexity.
- Detailed Insights: Often, pen test tools generate comprehensive reports with proper prioritization of vulnerabilities based on severity, business impact, etc. It reduces time in remediation.
- Integration into SDLC: Easy integration of pen test software into your SDLC enables your developers to build secure applications by testing and resolving issues before deployment.
7 Key Considerations for Choosing a Penetration Testing Tool
The following are important considerations for choosing the right pentesting software or tool. Keep them in mind while making a decision.
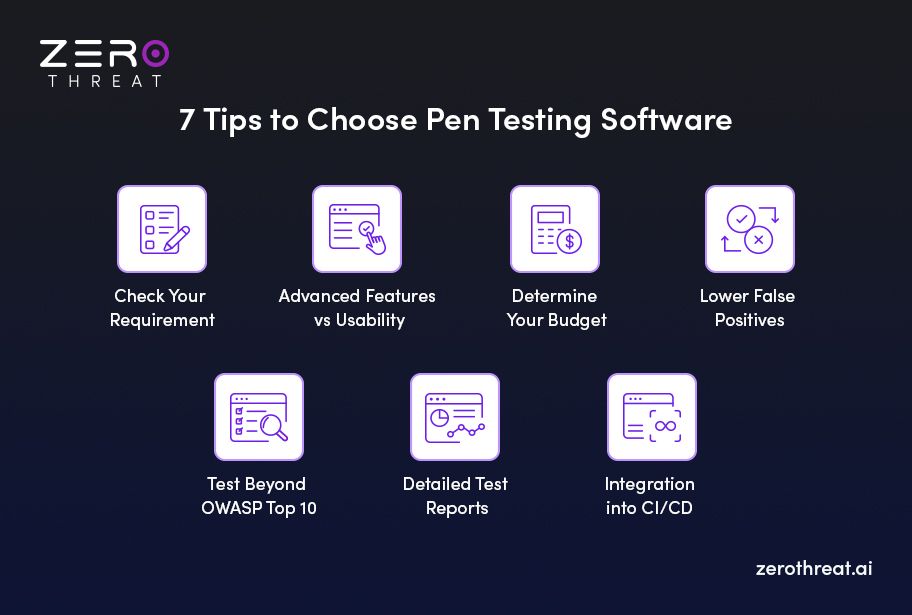
1. Check Your Requirement
Understanding your specific requirements is essential to make the right choice when it comes to choosing a pentest tool or software. Define the scope of pentesting like the specific application, network, or system you want to test, your goals, and the desired features.
Different pentest software has varying capabilities, features, and cater to different requirements. You can choose the most effective tool by understanding what you need to achieve with pentest.
2. Advanced Features vs Usability
Ease of use and features must go hand-in-hand when making a selection. If you prefer advanced features over usability, there will be a learning curve that will make pentesting difficult and time-consuming.
On the other hand, if you prefer ease of use over advanced features, there may not be sufficient features to support your testing needs. So, you can look for a tool that offers a balance between features and usability.
However, it also depends on your team’s skillset. You can pick pen test software with advanced features if your team has good technical skills and vice versa.
3. Determine Your Budget
To choose the perfect pen test software, start by understanding your budget. Can your business afford expensive tools, or do you need something budget-friendly? For cash-strapped businesses and startups, there are many open-source tools like Nikto, OpenVAS, and ZAP.
These tools are available for free and reduce the overall cost of penetration testing for businesses with limited budgets.
Say Goodbye to Restless Nights with AI-driven Automated Pentesting to Keep Your Assets and Data Secure Secure Your Assets
4. Lower False Positives
False positives are a big roadblock to successful identification and remediation of vulnerabilities. They are false red flags, which means pen test tools can indicate a vulnerability when it may not actually exist. Why are they bad? False positives waste your time and resources.
Just imagine your team spent hours only to find that the vulnerability they were hunting was merely a feature. Obviously, it leads to frustration and fatigue among your team. Hence, you should be careful about false positives when choosing a pen test tool.
While most pen test software tools generate false positives between 5- 20%, there are pen testing tools like ZeroThreat that generate less than 1% false positives, which is negligible and saves crucial time and resources.
5. Test Beyond OWASP Top 10
Smart hackers know OWASP top 10 are common vulnerabilities, and all businesses focus on them. So, they explore more complex vulnerabilities like business logic. It is crucial to choose a penetration testing tool that can discover vulnerabilities beyond OWASP.
A good tool will test your application or system for business logic flaws and other complex vulnerabilities. These vulnerabilities are beyond the standard OWASP top list.
6. Detailed Test Reports
Proper test reports are vital to identify critical vulnerabilities and take prompt actions to fix such issues. Therefore, pick a pen test tool that offers a prioritized overview of vulnerabilities and actionable reports to help fix issues easily and quickly.
The tool should offer audit-ready reports with compliance status. There are many tools that generate great reports like Acunetix, ZAP, ZeroThreat, and Burp Suite. Besides, these reports should also offer remediation steps to reduce MTTR (Mean Time-to-Remediate).
7. Integration into CI/CD
A good pen testing tool easily integrates into your CI/CD pipeline and existing security tools. This will enable you to continuously test applications within your SDLC. Consequently, you can identify and fix vulnerabilities early to protect your application post-deployment. Early testing reduces the risk of data breaches and strengthens the security posture.
Best Penetration Testing Tools Used by Diverse Businesses
Although there are lots of pen testing tools in the market now, there are some top tools that businesses of all sizes and types use, as mentioned below.
ZeroThreat
It is a next-gen penetration testing tool that combines automated vulnerability scanning with DAST capabilities. ZeroThreat is known for its 10X faster scanning speed and 98.9% accuracy rate. It discovers OWASP top 10, business logic flaws, and more complex vulnerabilities. Key Features of this include zero false positives, AI-based remediation reports, zero-configuration, compliance-based test reports, and easy integration into CI/CD.
Metasploit
It is a pen testing framework that offers diverse tools and features for security testing. With a library of 1600+ exploits, it offers extensive attack methods to pentest a target. Metasploit is an open-source framework that supports both defensive and offensive security methods. Key features include customizable testing, prioritized reporting, ready-made code for testing, and more.
W3af
W3af is specifically created for web application pentesting that helps discover 200+ vulnerabilities. It helps discover a wide range of vulnerabilities, including SQL injection, unhandled errors, misconfigurations, cross-site scripting, and more. Key features of w3af include scans of all kinds of web apps, even complex ones, extensions, proxy support, and export reports in HTML, CSV, and text formats.
Nessus
It is one of the most commonly used pen testing tools with many good features. Nessus helps discover a wide range of vulnerabilities and configurations in applications and networks. It simplifies the process by automating the detection of vulnerabilities, malware, and missing patches across applications. Key features include authenticated or non-authenticated scanning, comprehensive coverage, lower false positives, compliance scanning, and more.
ZAP
Zed Attack Proxy (ZAP) is a well-known open-source pen testing tool that is widely used by cybersecurity professionals. This tool is available for free and helps discover numerous vulnerabilities, including those listed in the OWASP top ten. Key features of this tool include automated scanning, fuzzing, spidering, passive scanning, authenticated/unauthenticated scanning, and more.
Be Smarter Than Hackers with Continuous Testing and Remediation of Security Weaknesses to Foil Their Malicious Attempts Let's Connect with the Team
Final Thought
Failing to secure your application, system, or network from cyberattacks not only causes heavy financial and reputational damage but also degrades customers’ confidence in your business. Pentesting is an offensive cybersecurity strategy that enables you to actively assess your assets and mitigate risks instead of solely relying upon your defense mechanism.
Various considerations we have discussed in this blog can help you choose the right penetration testing software or tool. However, if you are looking for a budget-friendly, easy-to-use, and advanced pentest tool, then ZeroThreat is the best choice. With its automated penetration testing and AI-powered remediation reports, you can reduce your attack surface and strengthen your cybersecurity posture.
Security teams seeking deep and accurate pen testing results can rely on ZeroThreat. It offers vulnerability detection and goes beyond known OWASP risks. It is a go-to platform for security teams and developers to perform regular vulnerability testing and reduce the risk of cyber threats. Try it now to learn more about it.
Frequently Asked Questions
Are there different types of pentesting tools?
Yes, there are many types of pen testing tools, as mentioned below.
- Vulnerability scanners
- Port scanners
- Web proxy
- Network sniffer
- Social engineering
- Web app pen testing
- Network pen testing
- Cloud pen testing
Who uses pen testing tools?
Which are the top free pen testing tools?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


