All Blogs

Quick Summary: Penetration testing reports play an important role in cybersecurity. Explore everything about pentesting reports in this blog, what their structure is, how they are generated, and the key benefits of using them. This blog will help you understand pen test reports in depth, so you can utilize them effectively to strengthen cybersecurity, meet compliances, and build stronger defenses.
Pen tests give you a reality check of how secure your applications, websites, systems, and networks are. They also expose hidden vulnerabilities and weaknesses that might be escaping your security team’s eyes. After a penetration test, a report is generated that provides an analysis of the vulnerabilities detected.
These reports are essential documents for identifying and mitigating cyber security risks for your organization. They don’t just summarize vulnerabilities; they offer a comprehensive outlook of your security posture enabling you to understand and act promptly to protect your data and assets.
Pen testing reports let you know the risks, their impacts, and possible steps you can take to secure your applications and systems. In this blog, we will explore penetration testing reports in detail to help you understand their significance in cybersecurity.
Understand Your Attack Surface with a Clean and Detailed Pentest Report - Test and Generate a Report in Minutes! Try Now for Free
On This Page
- An Overview of Pentest Report
- Importance of Penetration Testing Reports
- Internal vs External Pen Testing Reports
- How are Pentest Reports Generated?
- Key Penetration Testing Report Components
- AI-powered Remediation Reports with ZeroThreat
What is a Penetration Testing Report?
A penetration testing report is a document that provides detailed summaries of vulnerabilities and misconfigurations discovered in an application, system, or network. Apart from this, it also provides necessary information about the risks, severity, and business impact of vulnerabilities.
The pentest report will also provide recommendations for fixing those vulnerabilities. Moreover, a penetration testing report is like a health report that offers vital information on the health of an application, system, or network.
All in all, the pen test report provides detailed information on vulnerabilities detected during a security test along with their risk potential and remediation steps. Usually, these reports follow a standard structure and are divided into multiple sections like executive summary, methodology, remediation, etc.
Why Does Penetration Testing Report Matter?
Pen testing reports serve as a roadmap to strengthen your cybersecurity posture and take the appropriate steps to prevent potential cyberattacks. Additionally, it is an important document for various stakeholders like executives, developers, customers, and regulatory authorities.
These reports are essential to understand your attack surface and take the right steps to mitigate cybersecurity risks before they hit your organization. Besides these reports is vital to build a robust incident response plan by understanding gaps and filling them with suitable measures.
Hence, pen testing reports are important documents reflecting the strengths and weaknesses of your organization’s cybersecurity readiness. The following points elaborate on the benefits of pen testing reports for you.
Vulnerability Details
A pentest report offers a detailed analysis of vulnerabilities providing crucial information that helps CISOs, CTOs, and CXOs make decisions promptly and strengthen security posture. These reports help them understand potential risks, severity, and impact based on the vulnerabilities detected in applications, networks, or systems. A prioritized view of vulnerabilities helps identify the most critical risks easily.
Build Credibility
Regular penetration testing demonstrates your commitment to cybersecurity. It helps foster confidence among your stakeholders and customers. It also paves the way for more security-conscious customers to be attracted. Pen test reports and certificates provide proof that you take concrete steps to protect customers’ data.
Assure Compliance
A penetration testing report is a vital document that ensures compliance. Organizations can serve this document to regulatory and auditing bodies as evidence of their cybersecurity efforts. This enables your organization to meet compliance requirements like PCI DSS, HIPAA, GDPR, and more. The reports also highlight any gaps in compliance that you can promptly address by taking the right steps.
Risk Mitigation
In order to mitigate the risks of security weaknesses, you need a proper understanding of the vulnerabilities and their impact. A penetration testing report provides the necessary information that will help you cut time in mitigation and remediation steps. These reports offer remediation steps or recommendations to mitigate risks. It sets a clear roadmap for security teams to address vulnerabilities.
Assess Security Posture
Just like a health report provides essential information about your health and wellness, the pentest report uncovers the weaknesses and strengths within your existing security posture. It enables you to understand whether your existing security posture can withstand a cyberattack or if there are hidden loopholes that attackers can exploit. Consequently, you can harden the security controls and make them stronger to prevent any potential cyberattack.
Cybersecurity Awareness
Pen testing reports are also instrumental in raising awareness about cybersecurity risks. It helps executives or management make appropriate decisions to boost cyber defenses and implement policies that encourage a security-first mindset.
Supercharge Your Security Team with Next-Gen DAST Capabilities to Ward Off Cyber Risks Give It a Try
Internal vs External Penetration Testing Reports
Pen testing reports are essential documents that allow CISOs, security teams, and business owners to make the right decisions. However, when it comes to cyber threats, they not only arise from outside an organization, but they can also originate within an organization. Hence, penetration testing reports can be divided into external and internal pen test reports.
Internal Pen Testing Report
This pen testing report provides information on internal threats. What does it mean? Well, when a pen tester performs an internal security audit by conducting tests with some level of access to an organization’s network, an internal pentesting report is generated.
This report helps you identify potential risks from a disgruntled employee or business partner. It helps understand what systems or resources such bad actors can compromise. You can discover weaknesses in access controls, policies, and other internal procedures.
External Pen Testing Report
External penetration testing is a security audit that helps evaluate your system or application against an external cyber threat. This is a testing method that identifies threats like an actual hacker. The tester tries to attack the application or system from outside without any access.
The outcome of such testing is an external pen testing report that provides information on vulnerabilities and their impact. It helps identify the risks to an organization from real hackers.
How are Penetration Testing Reports Generated?
Penetration testing can be manual done by ethical hackers, or it can be automated with pen testing and reporting tools. In the case of a manual pen test, the ethical hacker will conduct comprehensive security assessments for your application, system, or network by identifying and exploiting vulnerabilities like a real hacker.
The result of these tests will be reflected in the pen testing report created by the ethical hacker. Such a report is manually created following specific standards like CERT, CREST, CHECK, and PCI DSS. The reports highlight the test scope, methodology, findings, and recommendations.
Alternatively, you can leverage penetration testing reporting tools like ZeroThreat, ZAP, Metasploit, Nessus, and Burp Suite Community Edition to automate this process and generate reports without human intervention. These tools perform automated pen testing and generate detailed test reports.
While manual pentesting is costly and time-consuming, you can save costs and generate pen test reports quickly (as fast as a few minutes) with pen test reporting tools.
Key Components of a Typical Penetration Testing Report
What does a penetration testing report look like or what is its structure? There can be variations in different pen test reports. However, they all follow some crucial components that provide essential information about vulnerabilities and risk factors for your organization. Let’s see the key components of a typical pentest report.
Executive Summary
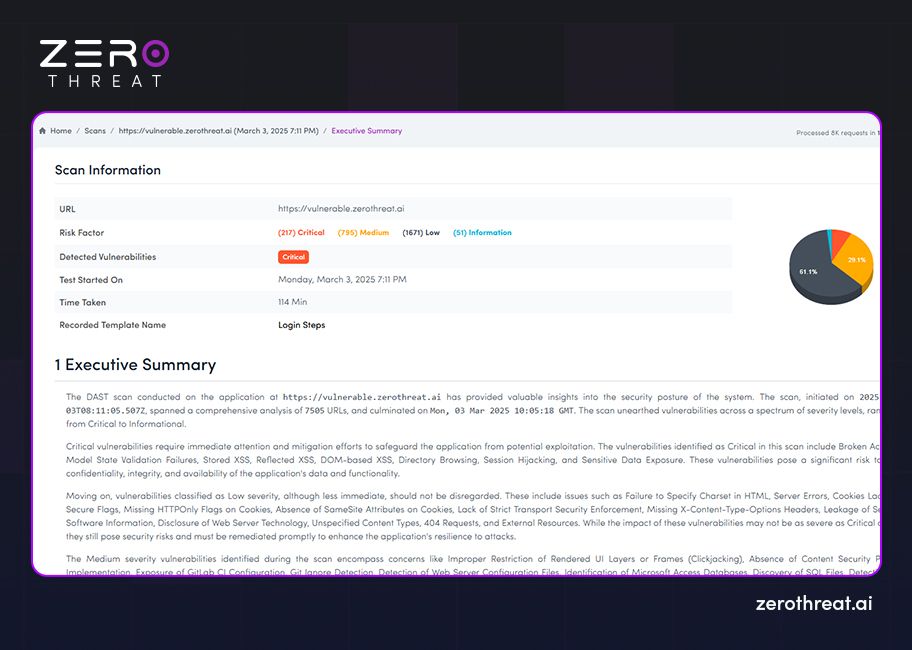
The executive summary is the detailed highlights of the findings during the pen test and the vulnerabilities detected. This is non-technical information that is written for C-suite executives, business owners, and non-security professionals. This component of a pen testing report enables the executives to understand the significance of vulnerabilities discovered and their impact on the business. It highlights critical information like severity, range of risks, and status of the current security posture.
Scan Summary
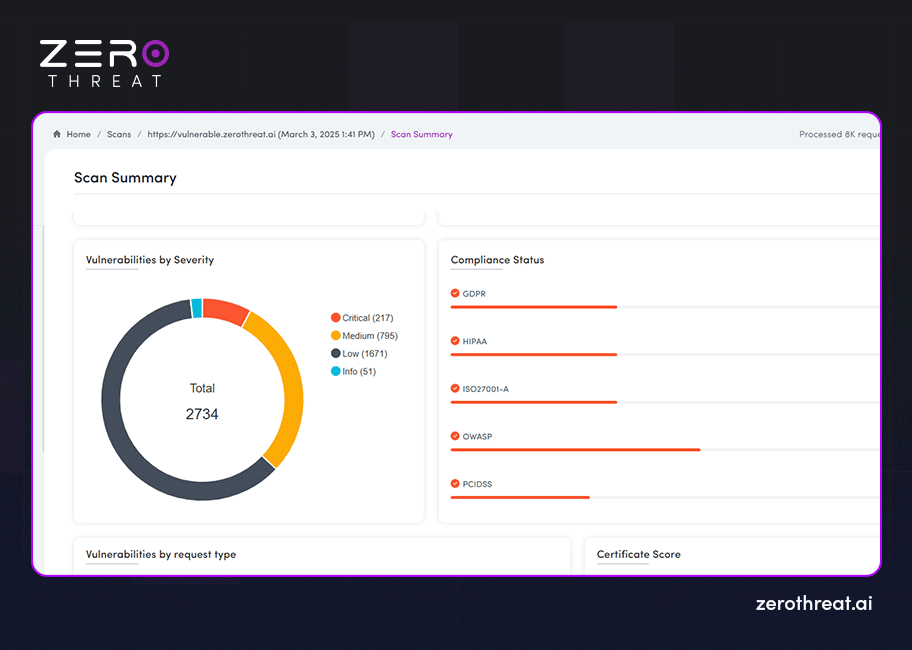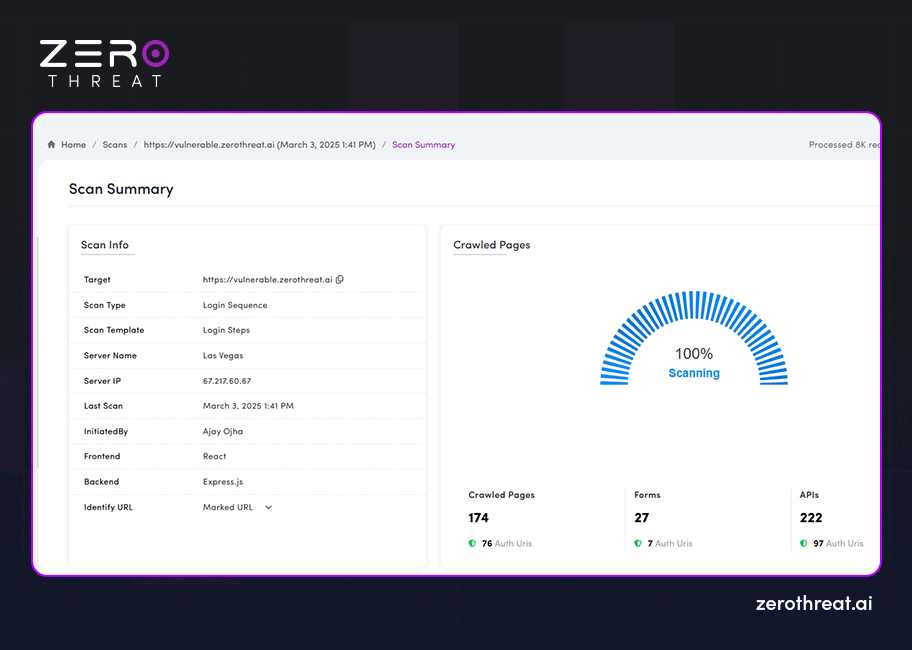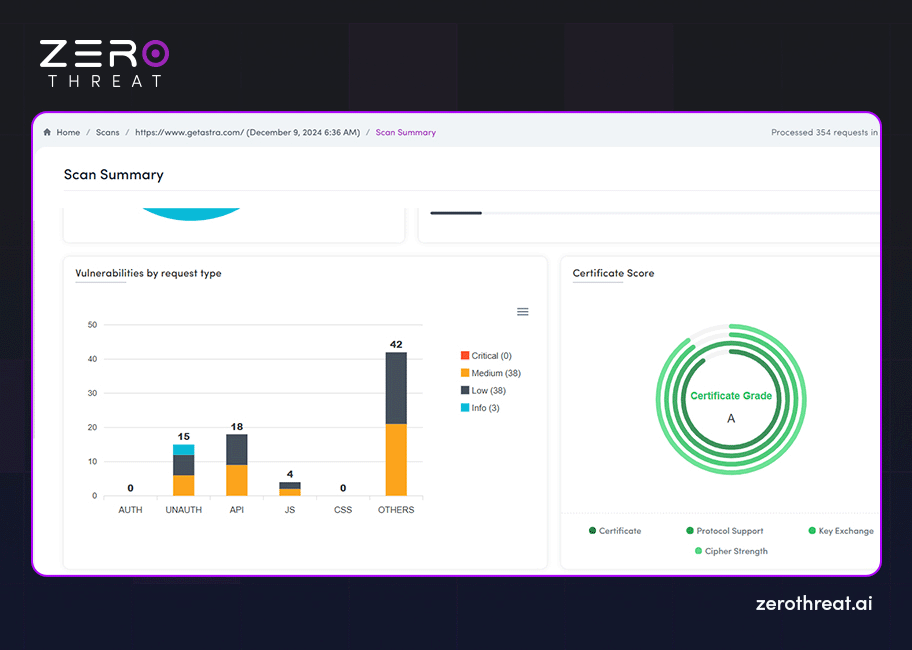
This is another section of the pentesting report that provides information like the scan type, target, host IP, underlying technologies used, number of crawled pages, and more. You get a quick overview of vulnerabilities detected and compliance status with this section through charts and visuals. It provides information about the scope of penetration testing and overview of the scan results.
Findings of the Assessment
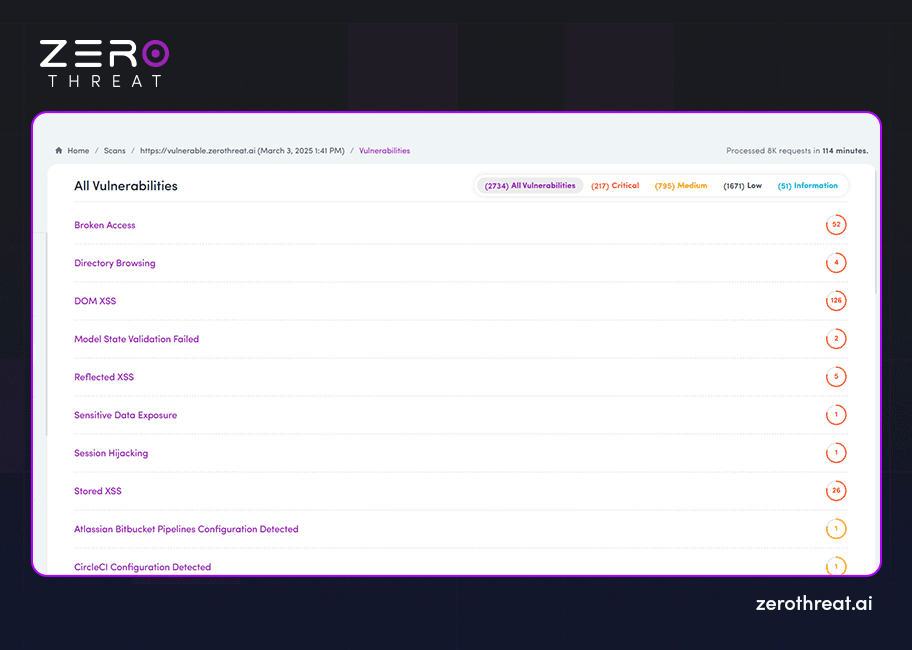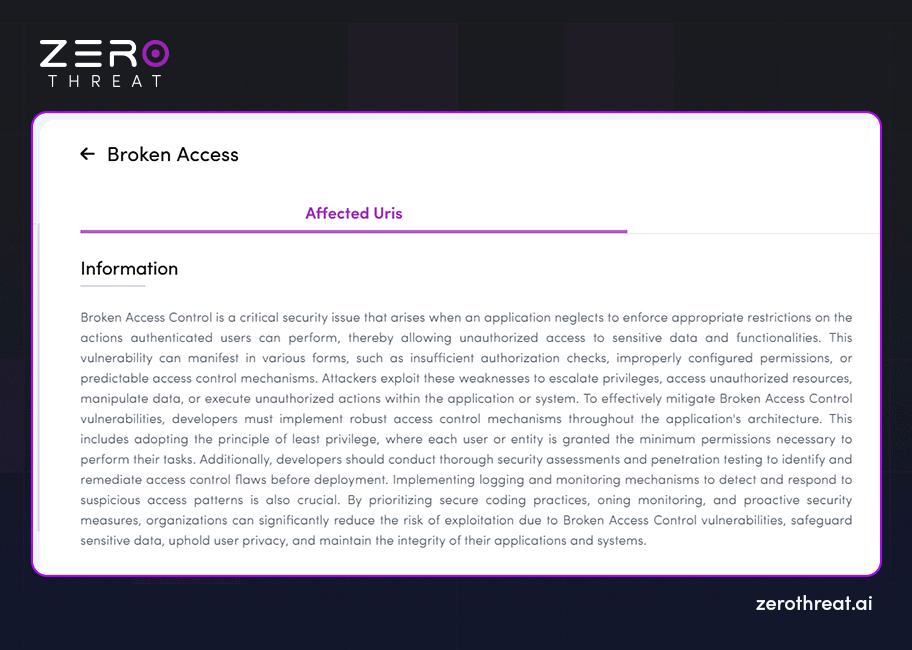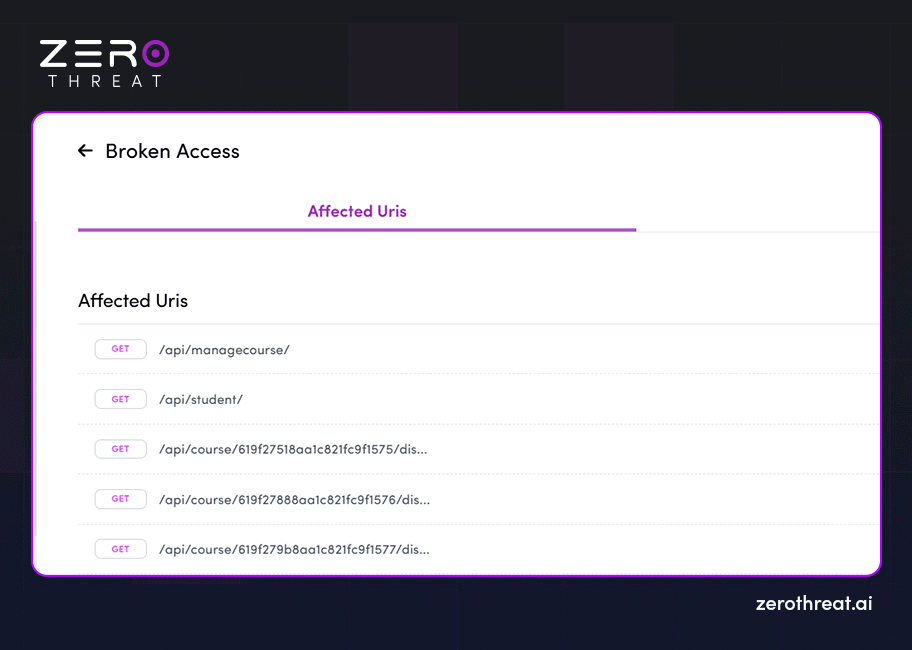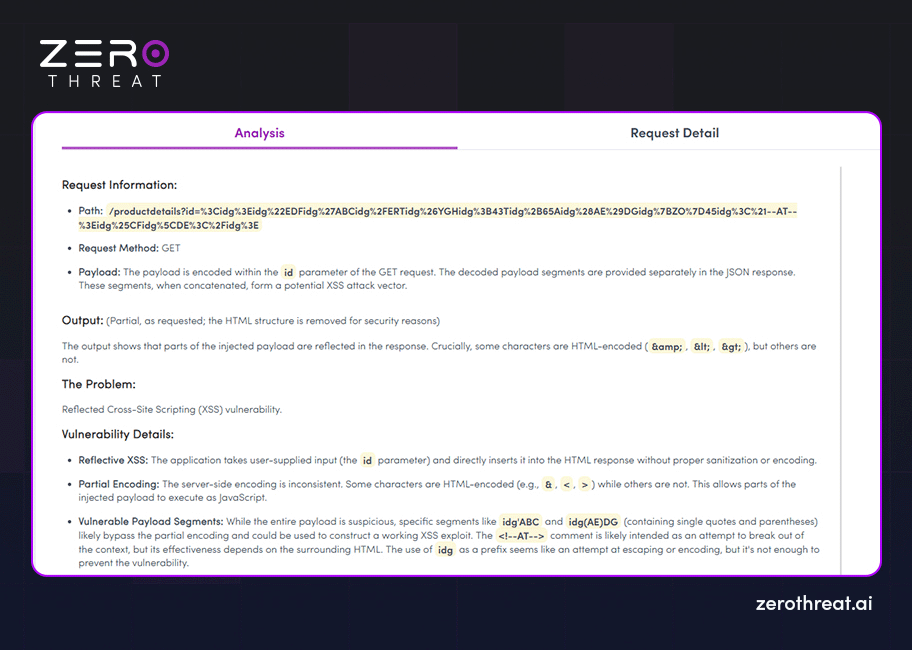
Now this section describes the vulnerabilities discovered along with necessary information like type, severity, status, impact, and more. Additionally, it offers details on how an attacker can exploit those vulnerabilities and what kind of data or resources can be compromised with such exploitation. This section broadly describes the following things.
- Overview: Give a description of the vulnerability along with details like how it works and how an attacker can exploit it.
- Business Impact: Provides information on how it can affect your business and what resources can be compromised. For example, affected URLs, software, configurations, IP ports, etc.
- Risk Level: It provides information about the severity level of a vulnerability like high, medium, or low.
- Status: Indicates the current status of the vulnerability whether resolved or unresolved.
- Score: The vulnerabilities are scored according to CVSS (Common Vulnerability Scoring System) between 0.0 and 10.0 indicating higher risk with a greater score and lower risk on the opposite.
- Compliance: This provides information about which compliance is affected by the identified vulnerability.
Recommendations
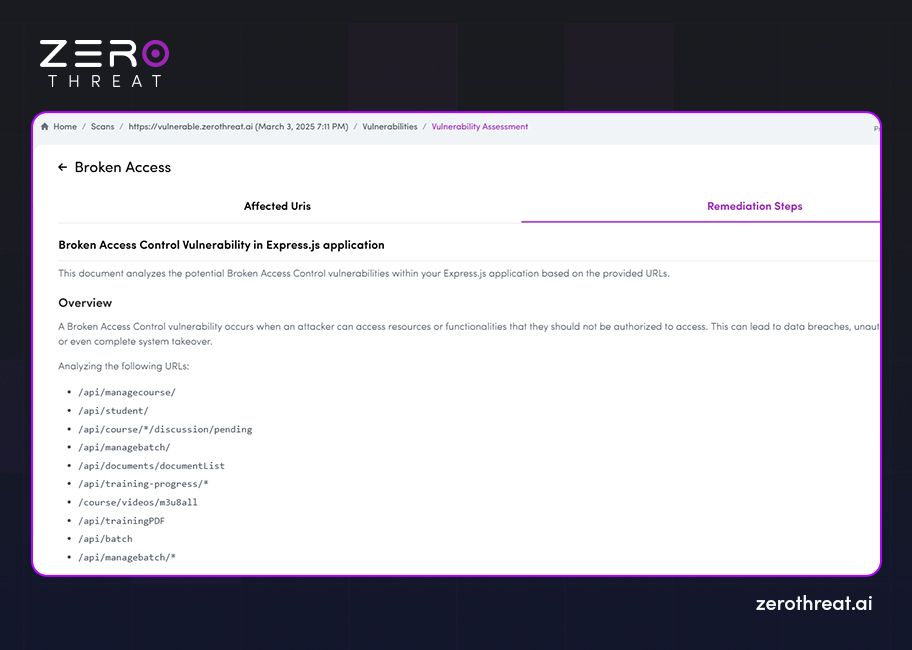
Good pentesting reports also provide suggestions for remediating vulnerabilities. They offer recommendations for developers or security teams to fix vulnerabilities. It provides information on how detected vulnerabilities can be fixed to speed up remediation. The remediation steps could include code changes, configuration updates, improvements in security controls, etc.
Hackers are Never Asleep! Stay Ahead of Them by Deploying Continuous Pentesting Get Instant Access
Automated Pen Testing and AI-powered Reports with ZeroThreat
Continuous security audits are crucial to maintain a healthy and secure digital infrastructure. It can be achieved with the automated pentest reporting tool – ZeroThreat. It is a next-gen pen test tool that goes beyond traditional vulnerability scanning tools.
It offers comprehensive pen testing and generates AI-powered remediation reports that accelerate the remediation process. You get actionable reports that provide suggestions and code examples for remediation that reduce your Mean Time-to-Remediation (MTTR) by 85%.
Start with a free sign-up to conduct in-depth security testing and get actionable reports.
Frequently Asked Questions
What is a pentesting report?
A penetration testing report is a document that explains the vulnerabilities found during the assessment and their impact. It outlines what was tested, how weaknesses were discovered, and what they mean for your system. The report also includes evidence and remediation steps. This report acts as a clear guide for engineering and security teams.
Why is a penetration testing report important?
What should a penetration testing report include?
How are vulnerabilities ranked or prioritized in the report?
Can penetration testing reports be automated?
What are common mistakes in pen test reporting?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


