All Blogs
Social Engineering Statistics 2026: Attacks, Costs, and Emerging Threats

Quick Overview: This blog explores the growing threat of social engineering and why it remains one of the most effective attack techniques today. We break down the latest social engineering statistics, common attack methods, real-world impact, and emerging trends. You’ll also learn why these attacks succeed, and the practical steps organizations can take to reduce risk and strengthen their security posture.
Social engineering is the practice of manipulating people into disclosing sensitive information or taking actions that undermine security, not by breaking systems, but by exploiting human trust.
Rather than targeting technical vulnerabilities, attackers rely on deception, persuasion, and psychological pressure to bypass defenses—turning people themselves into the weakest link.
It’s the scammer’s quiet confidence that a well-phrased email, a convincing phone call, or a familiar-looking QR code will get someone to hand over credentials, click a malicious link, or approve a wire transfer.
Why are we here to talk about social engineering statistics in 2026? Because social engineering thrives on anecdote and then scales.
We need hard facts to see the patterns: which vectors are growing, which industries are most targeted, how much breaches cost when the human element is involved, and how modern tools like generative AI are changing the attacker’s toolbox.
To give CISOs a clear, evidence-based view of the threat landscape, we’ve curated some interesting data-backed statistics that reveal how social engineering attacks operate, who they target, and the true cost of these incidents.
Sign up and run your first automated pentest in minutes — no complex setup required. Sign Up Free
On This Page
- TL;DR: Social Engineering Statistics Overview
- What is Social Engineering?
- Important Cybersecurity Social Engineering Stats
- Social Engineering Statistics: The Cost of Human-Focused Attacks
- Social Engineering Statistics for 2026
- Social Engineering Phishing Statistics
- AI-Driven Social Engineering Statistics
- Why People Fall for Social Engineering?
- How Frequently Do Social Engineering Attacks Occur?
- Human Element in Cybersecurity Breaches: Key Statistics
- Business Email Compromise: Key Statistics
- Data Breach Statistics: Key Facts and Trends
- Social Engineering is the Real Zero-Day Risk
TL;DR: Social Engineering Statistics Overview
- Social engineering involves manipulating individuals into disclosing sensitive information or performing actions that weaken security, by exploiting trust, urgency, familiarity, or routine, rather than technical vulnerabilities.
- Social engineering is the leading initial access vector, accounting for 36% of incidents. Social engineering phishing represents 65% of these attacks, 66% target privileged accounts, 60% result in data exposure, and nearly 50% of the global population encounters scam attempts on a weekly basis.
- AI, deepfakes, and automation are significantly increasing attack effectiveness. 82% of phishing emails now contain AI-generated content, deepfake tool trading has surged by 223%, and new techniques such as FileFix exploit everyday user behavior instead of technical flaws.
- Deepfakes now account for 6.5% of all fraud attacks, marking a staggering 2,137% increase since 2022, and emphasizing the need for robust risk mitigation.
- 98% of cyberattacks involve some form of social engineering.
- The average organization experiences more than 700 social engineering attacks per year.
- 90% of data breaches exploit the human element as the primary path to accessing sensitive business information.
- 83% of U.S. businesses have experienced at least one phishing attack; 95% of successful network intrusions rely on spear phishing, yet only 50% of employees can accurately define the term.
- The average financial impact of a single social engineering attack is approximately $130,000.
- One in three individuals who reported a scam also experienced direct financial loss. 25% of nation-state threat campaigns begin with casual conversation or “chit-chat” designed to lower suspicion and establish trust.
- Generative AI has reduced the time required to craft a convincing phishing message to under five minutes, dramatically lowering the barrier to entry for attackers.
- Social engineering, like phishing in finance sector, is the major cause of data breaches, with 78% of the incidents.
What is Social Engineering?
Social engineering is a type of attack where criminals trick people into giving away sensitive information or doing something they normally shouldn’t. This includes clicking a bad link, sharing a password, or approving a payment.
Instead of breaking into systems with code, social engineers target human behavior. They rely on trust, urgency, fear, curiosity, or routine to convince someone to act. If a message sounds right and arrives at the right moment, people may respond before thinking twice. This is something traditional and automated pentesting tool may not immediately detect.
A common example is a phishing email that looks like it came from your bank or your company’s IT team. It may ask you to “verify your account” or “reset your password.” Everything looks normal—but the link leads to an attacker. Once you click, the damage begins.
Social engineering in cybersecurity also occurs through phone calls (vishing), text messages (smishing), QR codes, fake websites, and even face-to-face interactions. Attackers may pretend to be a manager, vendor, customer, or support agent to gain trust.
In a nutshell, social engineering attacks people first, knowing that one mistake can bypass even the strongest security tools.
Important Cybersecurity Social Engineering Stats
Below are the most important social engineering statistics you need to know right now.
Phishing and social engineering are among the top causes of breaches. Verizon’s Data Breach Investigations Report shows social engineering (phishing & pretexting) as a leading action vector in incidents and breaches.
Human behavior remains a huge problem: Around 68% of employees admit to risky behavior that could enable phishing or malware infections. Moreover, more than two-thirds of employees self-report risky choices that increase organizational exposure.
The financial toll is huge: annual internet-crime losses are in the billions. The FBI’s Internet Crime Complaint Center (IC3) reported total reported losses exceeding $16 billion in its most recent annual release. BEC and investment scams are major contributors.
Average cost of a data breach increased, phishing-related breaches show very high cost-per-incident. IBM’s Cost of a Data Breach reports the global average breach cost around $4.88 million, with phishing/social-engineering incidents being among the most costly.
Attackers are shifting tactics: malicious URLs now outnumber malicious attachments, and smishing/QR-based lures are growing rapidly. Reporting from Proofpoint and summaries in industry press note billions of URL-based threats and dramatic percentage increases in smishing and QR-code attacks in recent months.
Social Engineering Statistics: The Cost of Human-Focused Attacks
Social engineering attacks don’t just damage reputation or erode customer trust—they deliver direct, measurable financial losses that hit organizations and individuals immediately.
- U.S. consumers reported $12.5 billion in fraud-related losses in 2024 alone, with government-impersonation scams accounting for $789 million of that total.
- Social engineering is no longer the single top attack vector, but it remains firmly in the top three. According to recent data, vulnerability exploits have overtaken it, while social engineering continues to be a dominant initial access method.
- The average cost of a social engineering attack is approximately $130,000, covering stolen funds or compromised data. When combined with other attack techniques, total losses can rapidly escalate into the millions.
- As per report from World Economic Forum, online scams resulted in more than $1 trillion in global losses over the past year, underscoring the scale at which social engineering-driven fraud now operates worldwide.
- Call center–based scams targeting seniors and cryptocurrency investors generated $1.9 billion in reported losses in 2024, making them one of the most financially damaging fraud categories.
- North Korea’s IT worker infiltration scam is estimated to generate between $250 million and $600 million annually, funding broader state-sponsored operations.
- Even low-effort scams add up: fake road toll payment scams caused nearly $130,000 in reported losses in the U.S. in 2024, highlighting how small-scale deception still produces real financial damage.
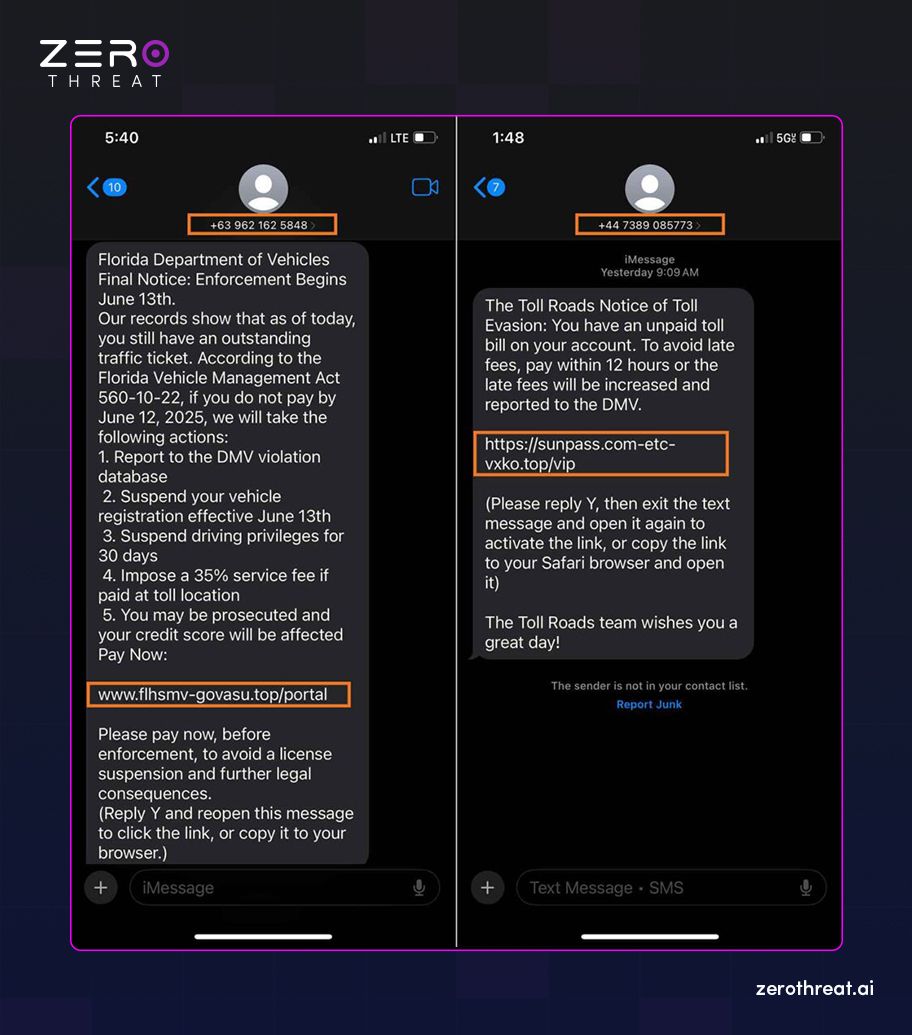
(Image Read: A screenshot of multiple fraudulent road toll SMS messages received over recent months, illustrating the widespread toll-payment scams seen throughout 2024 and 2025.)
Choose a plan that scales with your security needs. View Pricing
Social Engineering Statistics for 2026
As we move into 2026, social engineering continues to evolve rapidly. Let’s take a closer look at the key statistics to better understand how these attacks are changing, who they target, and the growing impact they have on organizations and individuals.
Malware and Ransomware Statistics
- Microsoft’s Digital Defense Report 2025 reveals that ransomware and extortion account for more than half of all cyberattacks worldwide.
- Nearly six out of ten organizations globally (59%) experienced at least one ransomware attack in 2024.
- Ransomware payments reached a record $460 million in the first half of 2024 alone.
- The largest ransomware payment on record—approximately $75 million—was made in 2024 to the Dark Angels ransomware group.
- In 2024, the median financial loss from ransomware and extortion-related breaches was $46,000.
- The median ransom demand increased sharply, rising from just under $200,000 in early 2023 to $1.5 million by mid-June 2024.
- Following a ransomware attack, 46% of organizations worldwide chose to pay the ransom to regain access to their encrypted data.
- 97% of organizations successfully recovered their data after a ransomware incident in 2023, with 70% relying on backups rather than ransom payments.
- Total ransomware payments declined by 35.8% in 2024 compared to 2023, largely due to increased law enforcement disruption.
- In 2025, only 13% of ransomware victims paid the ransom, down from 16.3% in 2024, while 62% restored data using immutable backups.
- Nearly one-third of all data breaches (32%) in 2024 involved ransomware or another form of extortion.
- Ransom payments increased year over year, with 16.3% of victims paying in 2024 compared to 6.9% in 2023.
- 14% of ransomware victims reported their backup systems were also compromised, either encrypted or made inaccessible during the attack.
- More than half of ransomware attacks in 2024 began with email or phishing-based entry points.
- Small organizations remain the primary targets, with 55.8% of ransomware attacks aimed at companies with 1–50 employees.
- Among small businesses hit by ransomware, one in five paid the ransom, and 60% of those payments ranged between $10,000 and $100,000.
- One in ten organizations does not know how ransomware entered their environment, and one in three victims is unsure whether data was stolen.
- 81% of organizations report training employees to recognize and report potential ransomware threats.
- More than half of organizations (55%) have purchased ransomware insurance coverage.
- Desktop sharing tools were used in 40% of ransomware incidents, while email was involved in 35% of cases.
- Ransomware is considered the top cybersecurity threat, with over half of organizations ranking it as their primary concern in 2024.
- The healthcare, financial services, and IT sectors are the most frequently targeted industries for ransomware attacks.
- Ransomware breaches take an average of 326 days to contain, which is 49 days longer than the average data breach.
- Excluding ransom payments, the average cost of a ransomware attack is $4.54 million. (IBM)
- Organizations that refuse to pay the ransom experience breach costs that are 13.1% higher on average.
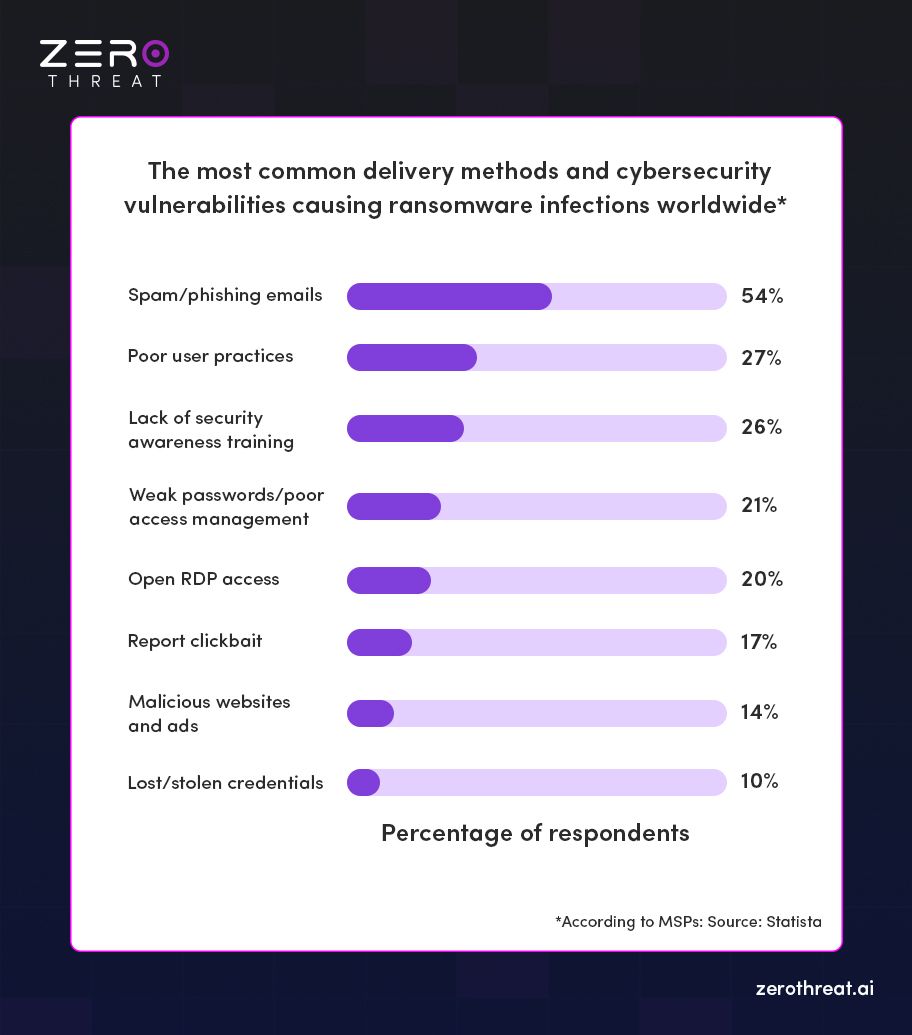
- Email remains the most common delivery method for malware, including ransomware.
- The AV-Test Institute registers approximately 450,000 new malware samples every day.
- Security experts estimate that a ransomware attack targets a business every 11 seconds.
- Social engineering remains the most common initial access method, with phishing responsible for 65% of social engineering-based intrusions.
- More than one-third of all incident response (IR) cases (36%) began with a social engineering technique.
- In early 2025, social engineering accounted for 39% of initial access events, fueled by a 1,450% surge in fake CAPTCHA–based attacks, including campaigns such as ClickFix.
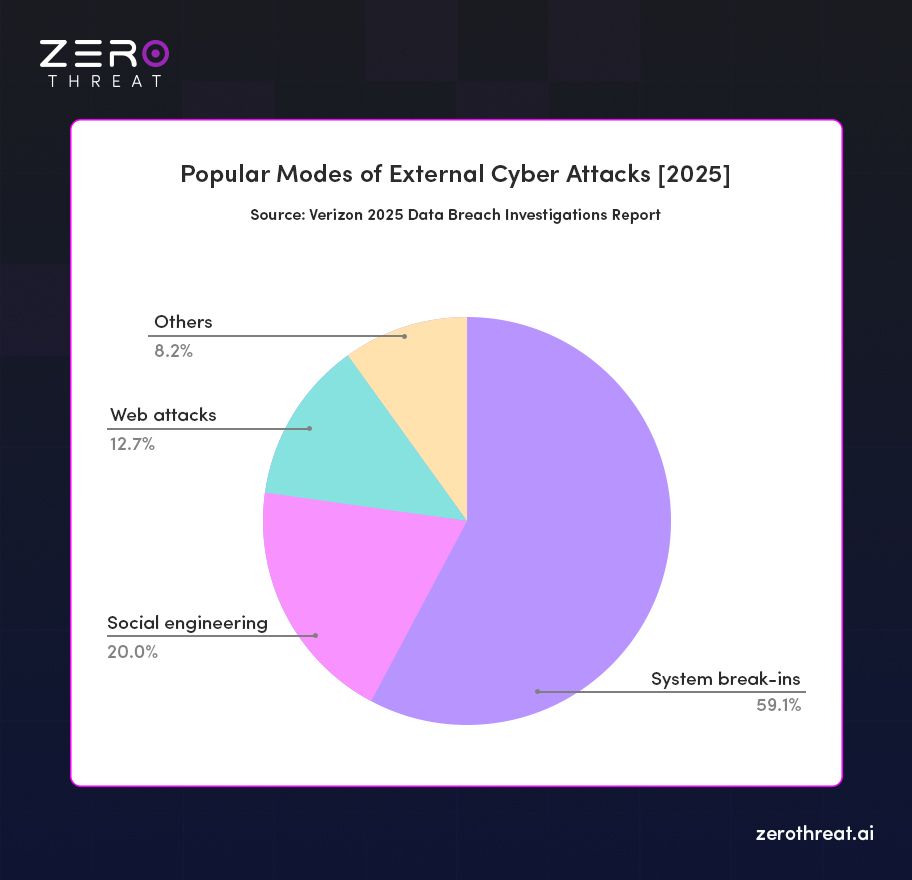
- External threat actors were responsible for 81% of confirmed breaches, making them the dominant source of security incidents.
- Within external-origin breaches, 22% involved social engineering, reinforcing that human manipulation remains one of attackers’ most effective entry tactics.
- Phishing accounted for 25% of social engineering incidents in 2024, continuing a downward trend from 29% in 2023 and 46% in 2022.
- PDF files were the most common malicious attachment type, making up 45.2% of cases, followed by HTML files at 17.4% and ZIP archives at 10.4%.
- Within malicious PDF attachments, 42% concealed links using obfuscation techniques, 28% embedded links within document streams, and 7% relied on password protection to evade detection.
- Stolen credentials became the second most common initial access method in 2024, used in 16% of intrusions, surpassing email phishing at 14%.
- In cloud-based intrusions, initial access most frequently occurred through email phishing (39%), followed by stolen credentials (35%), SIM swapping (6%), and voice phishing (vishing) at 6%.
- Adversary-in-the-middle (AiTM) kits and MFA-bypass tools were widely sold and used to weaken or defeat multi-factor authentication protections.
- Privileged accounts were targeted in 66% of phishing-related social engineering cases, while 45% involved impersonation of internal employees.
- Ransomware represented 28% of malware-related cases and 11% of all security incidents overall.
- Ransomware-related discussions on dark web forums increased by 25% year over year in 2024.
- The most common outcome of social engineering attacks was credential theft (29%), followed by data theft (18%) and extortion (13%).
- Manufacturing remained the most targeted industry, accounting for 26% of reported incidents in 2024.
- Attackers are now able to move laterally within networks in under 60 minutes, and in some cases in less than 15 minutes, making rapid detection and response critical.
- More than 90% of social engineering attacks begin with a friendly or collaborative approach, designed to lower suspicion and build trust.
- Social engineering attacks resulted in data leaks in 60% of cases, which is 16% higher than other attack types. Roughly half of these incidents involved business email compromise (BEC), and nearly 60% of BEC cases exposed sensitive data.
- In 2023, 97% of organizations successfully recovered encrypted data after a ransomware attack. Of those, 46% paid the ransom, while 70% relied on backups and 2% used alternative recovery methods.
- Microsoft Teams has emerged as a common social engineering vector, particularly in campaigns focused on gaining initial access.
- Threat actors increasingly used cloud services to host large-scale phishing campaigns, with Latin America experiencing particularly high impact.
- Attackers leveraged AI to generate phishing emails, build fake websites, and create deepfake content, significantly increasing the persuasiveness of social engineering attacks.
Continuously test your applications that finds exploitable vulnerabilities, not just surface-level issues. Start Automated Pentesting
Social Engineering Phishing Statistics
Phishing remains one of the most effective and widespread cyber threats. The following statistics highlight how frequently phishing occurs, who attackers target most, and why even a single deceptive email can lead to serious security and financial consequences.
- Financial services and online payment platforms accounted for 30.9% of all phishing targets, with attackers distributing millions of QR-code–based phishing emails.
- Phishing and pretexting remain the primary social engineering techniques used against SMBs in 2025, with prompt-bombing attacks increasingly observed.
- The Anti-Phishing Working Group (APWG) recorded 1,003,924 phishing attacks in Q1 2025 and 1,130,393 in Q2 2025, representing a 13% quarter-over-quarter increase.
- Cofense’s Phishing Defense Center analyzed one malicious email every 42 seconds on average in 2024, highlighting the scale of phishing activity.
- 94% of organizations experienced phishing attacks in 2024, and 96% of successful phishing incidents resulted in negative business impact.
- Phishing-as-a-Service (PhaaS) platforms powered 30% of credential-theft attacks in 2024 and are projected to drive up to 50% of such attacks in 2025.
- The median time for a user to fall for a phishing email is under 60 seconds, leaving little opportunity for intervention.
- Once a phishing email is opened, users click a malicious link in a median of 21 seconds, and then take just 28 additional seconds to submit their data.
- Phishing and email-based pretexting are responsible for 73% of all data breaches, making them the dominant attack methods.
- On average, 2.9% of employees click on phishing emails, a small percentage that still leads to significant organizational risk.
- Phishing was the most frequently reported cybercrime, generating 300,497 complaints.
- The average CEO is targeted by 57 phishing attacks per year, reflecting attackers’ focus on high-value executives.
- Microsoft brands are impersonated in 43% of phishing attacks, making them the most abused brand in phishing campaigns.
- IT staff receive an average of 40 targeted phishing attacks annually, due to their elevated access and privileges.
- Spear phishing techniques are used in 95% of successful network intrusions, underscoring their effectiveness.
- Phishing impersonation attacks account for 49% of all socially engineered threats, with attackers posing as trusted brands or services.
- Only 50% of employees can correctly define spear phishing, exposing a significant knowledge gap.
- 62% of organizations use security awareness training programs to reduce the likelihood of successful phishing attacks.
- Phishing is the second most common cause of data breaches and the most expensive, with an average breach cost of $4.91 million.
AI-Driven Social Engineering Statistics
AI is rapidly reshaping social engineering attacks, making them more convincing and scalable than ever. These statistics highlight how automation, generative AI, and impersonation technologies are changing attacker tactics and increasing the success and impact of human-focused attacks.
- 91% of security professionals reported that their organizations were targeted by AI-enabled email attacks within the past six months.
- Over one-third of social engineering incidents in 2025 involved AI-adjacent techniques, such as SEO poisoning and malicious prompt-based attacks.
- Attackers are increasingly using AI to scale phishing campaigns and influence operations, enabling faster, broader, and more convincing attacks.
- 60% of security leaders acknowledged sharing sensitive information with AI tools, increasing the risk of data exposure.
- 67% of IT professionals said generative AI has heightened their concern about becoming targets of ransomware attacks.
- 61% of organizations have adopted some level of AI-driven security and automation within their cybersecurity programs.
- Organizations with fully deployed security AI and automation experienced breach costs that were $3.05 million lower on average, along with a 74-day reduction in breach detection and containment time, compared to those without AI-based defenses.
- AI-driven cyberattacks have surged by more than 4,000% over the past three years, reflecting rapid attacker adoption.
- More than 82.6% of phishing emails analyzed between late 2024 and early 2025 contained AI-generated elements.
- Browser-based phishing attacks increased by 140% year over year, driven largely by generative AI and zero-hour phishing techniques.
Why People Fall for Social Engineering?
Attackers design attacks to trigger cognitive shortcuts:
- Authority bias: Emails or calls purporting to be from senior leaders or trusted vendors trigger compliance.
- Urgency & scarcity: The “pay now” or “reset immediately” creates panic that pushes fast, unvetted action.
- Reciprocity & familiarity: Pretexting that references shared context (a project, a recent meeting) lowers suspicion.
- Information overload: Overwhelmed employees default to quick decisions; Proofpoint’s data showing high self-reported risky behavior (68%) shows how common such shortcuts are.
How Frequently Do Social Engineering Attacks Occur?
Social engineering is now a common reality for individuals and organizations worldwide. The following social engineering statistics show how often these attacks occur and the groups they most frequently target.
- Nearly half of the global population encounters at least one scam attempt every week.
- In 2025, advanced fee fraud rose by nearly 50%, signaling renewed growth in long-running scam models.
- In the time it takes to read a single sentence, Microsoft blocks approximately 27,860 password-based attacks.
- One in five companies experiences at least one account takeover (ATO) incident every month.
- Social engineering is involved in 25% of all advanced cyberattack campaigns.
- The most frequently targeted industries are Healthcare and Pharmaceuticals (41.9%), Insurance (39.2%), and Retail and Wholesale (36.5%).
- Between 2023 and 2024, ransomware attacks disrupted 389 healthcare organizations, leading to operational delays and widespread appointment rescheduling.
- Roughly one-third of employees across industries remain vulnerable to phishing and social engineering, with an average phish-prone percentage of 33.1%.
- More than 1.5 million exposed credentials were discovered between January and June 2024, with 18% of code repositories containing leaked secrets.
- Microsoft mitigated 1.25 million DDoS attacks in the second half of the year, representing a fourfold increase year over year.
- Small businesses continue to be the primary ransomware targets, with 55.8% of attacks aimed at organizations with 1–50 employees.
- Espionage-driven activity accounted for 52% of social engineering breaches, reflecting increased intelligence-gathering operations.
- Financial gain was a motivating factor in 55% of social engineering breaches, reinforcing profit as a primary driver.
- The two most common intrusion methods were exploiting internet-facing applications (30%) and using stolen or misused credentials (30%).
Human Element in Cybersecurity Breaches: Key Statistics
- Human actions are involved in roughly 74–90% of cybersecurity breaches, making people the most exploited attack surface.
- Social engineering techniques play a role in more than one-third of all breaches, including phishing, pretexting, and business email compromise.
- Over 60% of data breaches involve compromised credentials, often obtained through phishing or password reuse.
- One careless click is enough—on average, 2–4% of employees click on phishing emails, which is sufficient for attackers to gain a foothold.
- Privileged users are disproportionately targeted, with nearly two-thirds of social engineering attacks aimed at accounts with elevated access.
- More than half of employees admit to risky security behavior, such as reusing passwords, bypassing controls, or sharing information under pressure.
- Phishing emails are opened and acted upon within minutes, often before security teams can respond.
- Organizations with poor security awareness training experience significantly higher breach rates compared to those with ongoing training programs.
- Mistakes during routine tasks—invoice processing, password resets, file sharing—are among the most common triggers for successful breaches.
- Breaches involving human error take longer to detect and contain, increasing overall financial and operational impact.
Uncover security gaps using real-world attack simulations powered by intelligent automation. Scan Your Web App
Business Email Compromise: Key Statistics
- Wire-transfer–based BEC scams rose by 33% in Q2 2025 compared to the previous quarter, indicating a sharp increase in payment-focused fraud.
- More than 21,000 BEC complaints were recorded in 2024, with reported losses exceeding $2.7 billion, making BEC the second most financially damaging cybercrime category.
- Business Email Compromise represents roughly 24–25% of all financially motivated cyberattacks, underscoring its role as a primary fraud mechanism.
- Cloudflare emerged as the most commonly used domain registrar among BEC scam operations in early 2025, reflecting attacker preference for certain infrastructure providers.
- Global losses attributed to BEC attacks between 2013 and 2023 surpassed $55.4 billion, highlighting the long-term financial impact of this threat.
- The median monthly volume of BEC attacks in the first half of 2025 increased by 54% compared to 2023, reaching a peak of 20 attacks per 1,000 mailboxes in mid-2024.
- One out of every ten social engineering attacks is a business email compromise incident, demonstrating how prevalent BEC has become.
- Most BEC attacks (77%) target employees outside of finance and executive roles, with sales teams alone accounting for one in five BEC targets.
- More than half of BEC incidents involve compromised or spoofed legitimate email accounts, making them difficult to detect with basic email filtering.
Data Breach Statistics: Key Facts and Trends
- The average cost of a data breach has reached nearly $5 million, making breaches more expensive than ever for organizations.
- More than half of data breaches involve compromised credentials, often obtained through phishing or other social engineering tactics.
- The average time to identify and contain a data breach is over 300 days, allowing attackers extended access to systems and data.
- Breaches involving ransomware take significantly longer to resolve than other breach types and result in higher overall costs.
- Organizations with strong incident response and automation experience lower breach costs, reducing both recovery time and financial impact.
- Cloud misconfigurations and third-party access are growing contributors to data breaches, particularly in hybrid environments.
- Small and mid-sized businesses account for a significant share of breach victims, despite having fewer resources for defense.
- Personally identifiable information (PII) remains the most commonly exposed data type, followed by financial and credential data.
- Breaches caused by human error are among the most costly and disruptive, often due to delayed detection.
- Regulatory fines, legal fees, and reputational damage frequently exceed the immediate technical recovery costs of a breach.
- 86% of social engineering incidents resulted in business disruption, including downtime, operational delays, or reputational harm.
- Human error was responsible for 68% of data breaches in 2024, often involving social engineering scams.
- The average global cost of a data breach in 2025 reached $4.4 million, reflecting rising remediation and recovery expenses.
- Small and mid-sized businesses were targeted nearly four times more often than large enterprises in 2025.
- The financial sector (17.4%) and business services industry (11.1%) ranked among the most frequently targeted industries in 2024.
- Social engineering attacks led to direct financial loss in 50% of cases, fraud in 28%, and data exposure in the remaining incidents.
- Cyberattacks involving stolen or compromised credentials increased by 71% year over year.
- More than one-third of social engineering incidents in 2025 used non-phishing techniques, such as SEO poisoning, fake prompts, or help-desk manipulation.
- Stolen credentials accounted for 16% of initial access incidents in 2024, overtaking email phishing at 14%.
- Cybercrime complaints in 2024 totaled 859,532, with reported losses reaching $16.6 billion, a 33% increase over the previous year.
- External threat actors were responsible for approximately 80% of data breaches.
- Social engineering techniques were involved in 98% of cyberattacks, highlighting their widespread use.
- The average business encounters more than 700 social engineering attacks each year.
- The average cost of a single social engineering attack in 2024 was approximately $130,000.
- Social engineering played a role in 20% of confirmed data breaches.
- More than 70% of employees admit to engaging in risky behaviors that increase organizational exposure to cyber threats.
- 90% of cyberattacks directly target employees, rather than systems or infrastructure alone.
- Organizations face an average of over 700 social engineering attack attempts annually, underscoring the scale of the threat.
- Financial gain motivated 89% of social engineering attacks, while 11% were driven by espionage objectives.
- Pretexting accounted for 27% of all social engineering-related breaches.
Don’t wait for a breach to test your defenses. Secure your apps with automated pentesting today. Get Started Now
Social Engineering is the Real Zero-Day Risk
Social engineering doesn’t break systems. In fact, it bypasses them by exploiting trust, urgency, and human behavior. The statistics are clear: even with an advanced security tool and a vulnerability scanner in place, attackers continue to succeed because people remain the most targeted and scalable attack surface.
For organizations, social engineering is not just a training issue or a compliance checkbox. It is a business risk that spans identity, access, financial workflows, vendors, and incident response. Resilient security programs assume social engineering will happen and focus on limiting impact through strong verification, layered controls, and rapid containment.
Security must be designed around how people actually behave, but not how we wish they would.
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


