All Blogs
NIST Cybersecurity Framework: Definition, Components, and Benefits

Quick Summary: NIST Cybersecurity Framework helps organizations improve cybersecurity risk management with a strategic approach to it. It offers various guidelines and best practices that organizations can follow to mitigate cyber risks effectively. Read on to learn more about this cybersecurity framework to know how it can help you protect your organization against rising cyber threats.
Every CISO or security leader has a huge responsibility to protect their organization’s networks, systems, applications, and other digital assets. However, this task can be both cumbersome and nerve-wracking without proper planning and guidance.
This is where cybersecurity frameworks come in handy as they provide the necessary guidance, practices, and methods to protect an organization’s digital assets against cyber threats. One of them is the NIST Cybersecurity Framework, which is widely adopted by organizations.
CISOs or security leaders can adopt this framework for their organizations to manage cybersecurity risks. It helps align cybersecurity strategies as per business objectives and relevant compliances. Keep reading to learn more about it.
Prevent Cyber Threats with 98.9% Accuracy and Avoid Costly Data Breaches Start for Free
Table of Contents
- An Overview of the NIST Cybersecurity Framework
- Benefits of the NIST Cybersecurity Framework
- What are the Components of NIST CSF?
- To Wrap Up
Understanding the NIST Cybersecurity Framework
The NIST Cybersecurity Framework (NIST CSF) defines different rules, guidelines, and practices that organizations can follow for cybersecurity risk management to protect their information assets. This framework is created by the National Institute of Standards and Technology (NIST) which comes under the U.S. Department of Commerce.
Cybersecurity has become a vital function of modern organizations due to rising incidents of cyberattacks and increasing costs of data breaches that stand at $4.88 billion currently, as per IBM’s report. However, cybersecurity can be challenging without planning and guidance.
NIST CSF provides guidance and a roadmap to ensure robust cybersecurity by following different activities and practices. It was launched as a voluntary guideline in 2014 to help organizations boost their cybersecurity posture. After this, several iterations of this framework have been launched, with NIST CSF 2.0 being the latest.
How Does the NIST Cybersecurity Framework Benefit Organizations?
Today, cybersecurity is a huge concern for organizations, and its changing landscape poses more critical challenges. Hence, organizations must adopt a proactive approach to cybersecurity. NIST CSF provides a robust framework to ensure cybersecurity with standard guidelines and practices. Adopting this cybersecurity framework offers many advantages to organizations, as mentioned below.
- Flexible and Scalable: NIST CSF is a flexible and scalable framework that adapts to organizations of different sizes and industries. It offers a risk-based and outcome-driven approach to cybersecurity.
- Proper Risk Management: The framework provides a clear method to identify, evaluate, and manage security risks to web apps, networks, and other digital assets while these efforts are aligned with the overall organizational strategy.
- Develop Cyber Resilience: Strategic detection and remediation of security threats, as well as implementing the learnings, help build cyber resilience.
- Recognized Framework: NIST CSF is widely recognized across industries. It is widely adopted in the private and public sector companies.
- Long-Term Risk Management: The NIST security framework takes organizations from the mindset of “one-off” risk assessment to adaptive and proactive cybersecurity risk management.
Components of the NIST Cybersecurity Framework
There are three primary components of the NIST Cybersecurity Framework: the Core, Implementation Tiers, and Profiles. The core functions are the vital features of this framework that define different aspects of an effective cybersecurity program. These functions involve various activities for organizations to manage and reduce cybersecurity risks. Let’s discuss these components in detail.
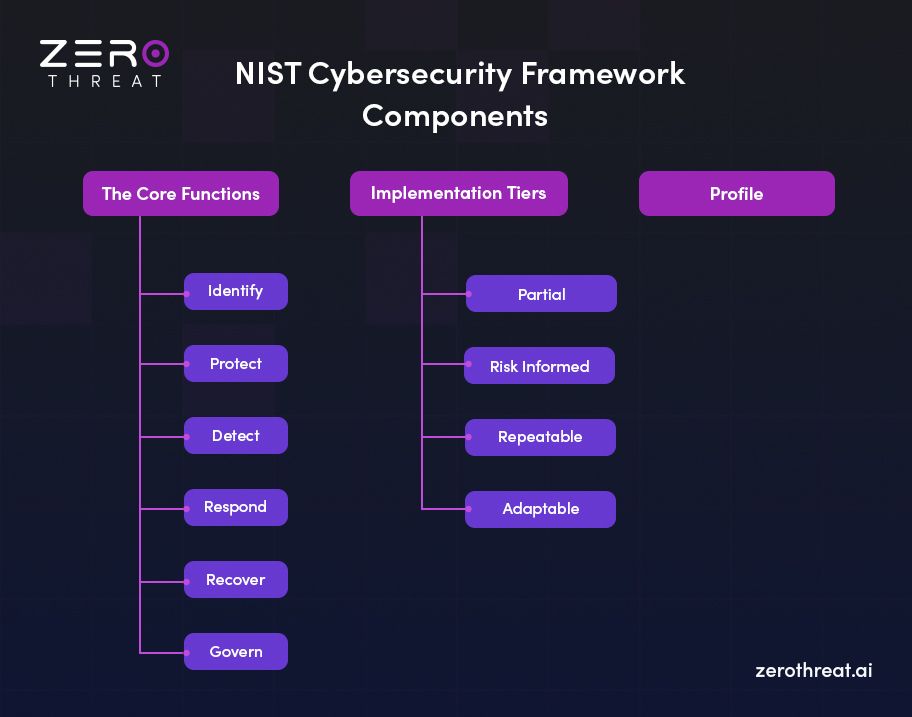
The Core Functions
The following are the five core functions described in the NIST cybersecurity framework.
Identify
This is the primary function of any successful cybersecurity program. It involves understanding the environment of an organization and the risks associated with it. The cybersecurity team needs to find out which resources and assets are the most important for their organization.
With a thorough understanding of the business context, critical assets, and associated risks, a cybersecurity team can prioritize and streamline their actions. This function includes several categories like asset management, risk assessment, supply chain risk management, business environment, etc.
It involves the following activities:
- Identifying software and physical assets.
- Identifying business environment and role in the supply chain.
- Checking existing cybersecurity policies as well as identifying legal/regulatory requirements.
- Discovering asset vulnerabilities and threats to an organization’s internal or external resources.
- Identifying risk tolerance and forming a risk management strategy.
With these activities, a cybersecurity team or CISO can understand the current security posture and find out gaps. It helps to determine the preparedness of an organization in managing and mitigating cyber threats.
Protect
As the name suggests, this activity in NIST involves implementing adequate safeguards to protect critical infrastructure. These safeguards ensure seamless availability of critical infrastructure services and limit/contain the impact of a cybersecurity incident.
Protect activity aims to build a strong security shield that can thwart potential cybersecurity risks. It includes several categories like data security, training and awareness, identity management and access control, protective technology and maintenance, etc.
It involves the following activities:
- Conducting security awareness training to ensure awareness about role-based or privileged access.
- Leveraging maintenance to protect the organization’s resources.
- Implementing methods and procedures to protect the organization’s assets and information systems.
- Ensuring proper management of technology to make systems secure and resilient while aligned with the organization’s policies and procedures.
- Implementing stronger access and identity management protection including remote access.
So, in this activity, the focus is to implement stronger safeguards to protect an organization’s systems and assets from cybersecurity threats. It ensures that critical services are available even if there is a cybersecurity incident.
Detect
The next function, according to the NIST Cybersecurity Framework, is “Detect,” which refers to the activity of identifying the occurrence of a cybersecurity incident on time. It is vital to quickly respond to a potential cyber threat by promptly identifying the issue and resolving it.
In short, this function focuses on prompt response to cyber threats and provides guidance on how organizations can do it with different categories of actions. Continuous monitoring and adverse event analysis are the two categories of the Detect function.
It involves the following activities:
- Ensuring continuous monitoring to detect anomalies and determine the potential impact.
- Verifying the effectiveness of existing security measures and implementing continuous monitoring.
So, the Detect function involves activities that empower an organization to identify and respond to cyber threats promptly.
Gain a Clear View of Potential Security Threats with an AI-powered DAST Tool Scan Now
Respond
Respond is complementary to the Detect function, which lays down the approach to control the impact of a detected cybersecurity incident. So, it involves creating an appropriate response plan to contain and minimize the impact of cybersecurity events.
Different categories in this activity include incident response planning, incident analysis, reporting and communication, and incident mitigation.
It involves the following activities:
- Ensuring the robustness of the response plan that must be executed during and after an incident.
- Communications with internal and external stakeholders.
- Analyzing the incident to find gaps and make an effective response plan.
- Performing mitigation activities to stop the further spread of threats or minimize the loss.
- Implementing lessons learned from previous incidents.
So, the activities in the Respond function provide guidance for organizations in responding to cybersecurity incidents promptly and effectively. Consequently, it helps organizations minimize the damage and ensure rapid recovery.
Recover
The next function in the NIST CSF is “Recover,” which refers to the activities and plans to restore services or processes impacted by a cybersecurity incident. It aims to recover affected services to normal operations at the earliest. Besides, it also helps build resilience against future occurrences of such incidents.
In simple words, the Recover function enables organizations to focus on quick restoration of disrupted operations and making the processes more resilient to any incidents in the future. It has two categories – incident recovery communication and incident recovery plan execution.
It involves the following activities:
- Applying improvements based on the learnings from existing or previous activities of detection/response plans.
- Making sure that there is a proper recovery plan in place for the restoration of processes or assets affected in an incident.
- Ensuring seamless coordination among internal and external stakeholders during or after an incident.
So, the activities involved in the Recover function aim to minimize the impact of an incident and reduce the time it takes to restore services.
Govern
Goven is a new function that was added to NIST Cybersecurity Framework 2.0. This addition was made to underline the importance of governance in effectively mitigating and avoiding cybersecurity risks. So, it lays the guidelines for effective governance structures in organizations that are conducive to managing cybersecurity risks according to an organization’s business objectives and necessary compliances.
The different categories of “Govern” include risk management strategy, managing cybersecurity risks to the supply chain, risk management strategy, organizational context, as well as responsibilities, roles, and authorities.
It involves the following activities:
- Defining objectives of risk management in accordance with different stakeholders.
- Determining a standard method to calculate, categorize, and prioritize cybersecurity risks.
- Defining and communicating the roles, responsibilities, and authorities for cybersecurity.
- Cybersecurity risk management strategy review and improvement to ensure wider coverage across the organization.
- Establishing communication lines between the organization’s stakeholders including third parties and suppliers.
The function of “Govern” is focused on enhancing the governance of processes to mitigate cybersecurity threats. It includes risk elements and emphasizes aligning governance to ensure robust cybersecurity.
Implementation Tiers
There are four implementation tiers that enable organizations to see if their cybersecurity practices align with the characteristics described in the NIST CSF. These tiers are designed to integrate cybersecurity risks with overall enterprise risk management strategy. Let’s check out these tiers below.
Tier 1: Partial
In this tier, an organization may be aware of the NIST Cybersecurity Framework and have adopted some practices from it. However, cybersecurity risk management is rather ad hoc or reactive instead of an integral part of the organizational strategy. Awareness of cyber risks is limited.
Tier 2: Risk Informed
Organizations in this tier are better aware of cybersecurity risks. However, the organization lacks a proactive and planned approach to cybersecurity. It doesn’t have a repeatable organization-wide risk management process.
Tier 3: Repeatable
In this tier, the organization and its senior executives are well aware of the potential cybersecurity risks. Plus, there is a repeatable and planned organization-wide cybersecurity risk management process in place. The security team has a plan to monitor and respond to cybersecurity threats.
Tier 4: Adaptable
The organization has developed cyber resilience with predictive indicators and the use of learnings to prevent and mitigate potential risks. Plus, the security team in such an organization continuously adapts the organization’s capabilities and technologies to changes in threats promptly and efficiently.
Profile
This component of the NIST CSF highlights the unique requirements of different businesses. It involves adjusting the Functions, Categories, and Subcategories of the framework according to an organization’s unique requirements, resources, and risk tolerance.
The Profile helps organizations create a tailored roadmap for cybersecurity that aligns with relevant compliances/regulations, industry sectors, business objectives, and priorities. It enables organizations to create a risk profile and spend resources accordingly.
Upgrade Your Traditional Cybersecurity Approach with Continuous Threat Assessment Assess Your Assets
To Wrap Up
Cybersecurity frameworks are essential tools for organizations to develop the right strategies for protecting their applications, networks, and other digital assets from evolving cyber threats. Today, there are a lot of cybersecurity frameworks like CTEM, COBIT, HITRUST, NIST, and more.
We have discussed the NIST Cybersecurity Framework in this blog which provides a set of guidelines and best practices to enhance cybersecurity posture for an organization. Moreover, continuous risk assessment is an essential part of this security framework that requires a robust tool like ZeroThreat.
As an advanced web app and API vulnerability scanner, ZeroThreat is capable of identifying a wide range of vulnerabilities, including those that other scanners cannot detect, such as zero-day exploits and out-of-band vulnerabilities. It is designed for modern security experts, CISOs, and developers to streamline the AppSec process.
Take a look at this tool for more information about it.
Frequently Asked Questions
How is NIST different from ISO 27001?
ISO 27001 is a standard that focuses on improving the information management systems of an organization. On the other hand, NIST CSF is a cybersecurity framework that offers a roadmap to manage and reduce cybersecurity risks.
How do organizations use NIST CSF?
What are the five elements of the NIST CSF?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


