All Blogs
ZeroThreat and the Future of AppSec: A Technical and Operational Review

Quick Overview: ZeroThreat is reshaping AppSec by unifying continuous scanning, exploit-aware detection, and developer-aligned workflows. The blog reviews technical foundations, operational benefits, and how ZeroThreat’s approach reduces noise, accelerates remediation, and positions teams for the next generation of application security.
Application security has reached a level where teams are surrounded by various tools, dashboards, and recommendations. The problem isn't a lack of scanners or reporting systems. The problem is the gap between what these tools claim to do and what actually helps teams secure an application.
The reality is:
- Scanners catch patterns. Pentesters catch logic.
- Developers fix what is clear. They ignore what is vague.
- Leaders need visibility, but they also need results.
Amidst this chaotic environment, teams want something simple: A reliable way to understand where real risk exists, without drowning in noise.
This is where ZeroThreat comes into existence. Everyone thought and expected another automated tool with a new angle. However, after several months of testing, launching, and being used by 5,000+ organizations across various environments, ranging from small APIs to complex web apps, we are proud to claim that ZeroThreat behaves differently.
ZeroThreat redefines the value by:
- Approaching problems through reasoning.
- Scanning based on assumptions.
- Validating issues the way a human pentester would.
- Keeping the workflow simple.
This article is a detailed walkthrough of how ZeroThreat works, how teams can use it, and where it fits in the broader AppSec landscape.
Ready to try next-gen AppSec? Sign up and start instantly for FREE. Get Started FREE
On This Page
- What Is ZeroThreat?
- “Zero” Philosophy of ZeroThreat
- How ZeroThreat Bridges the Gap in AppSec
- What Powers ZeroThreat’s Automated Testing
- The AI Engine: More Than Just a Scanner
- Core Scanning and DevOps Integration
- How to Integrate ZeroThreat’s Pentesting into CI/CD Pipelines
- ZeroThreat vs Snyk, Veracode & Aikido
- ZeroThreat’s Role in an AI-Driven World
- What the Next Generation of Pentesting Will Look Like
- Final Thoughts
What is ZeroThreat? A Beginner’s Guide to AI-Powered Pentesting
ZeroThreat is an autonomous pentesting platform designed to identify, triage, and mitigate vulnerabilities from modern web apps and APIs. In simpler terms, it's designed to simulate real-world attacks on your live, running web applications and APIs to find exploitable vulnerabilities.
ZeroThreat stands out as a tool that makes AI-driven penetration testing easier, especially with its “zero setup” approach.
It uses a multi-layer analysis approach to simulate how a security engineer investigates and validates issues. Instead of relying on static rules, payload lists, or surface-level scanning, ZeroThreat behaves like an active attacker, dynamically probing applications to uncover and validate real-world vulnerabilities.
The challenge ZeroThreat is trying to address is something most AppSec teams already feel: development cycles are moving at a rapid pace with CI/CD, but security testing doesn’t always keep up. This creates a dangerous gap.
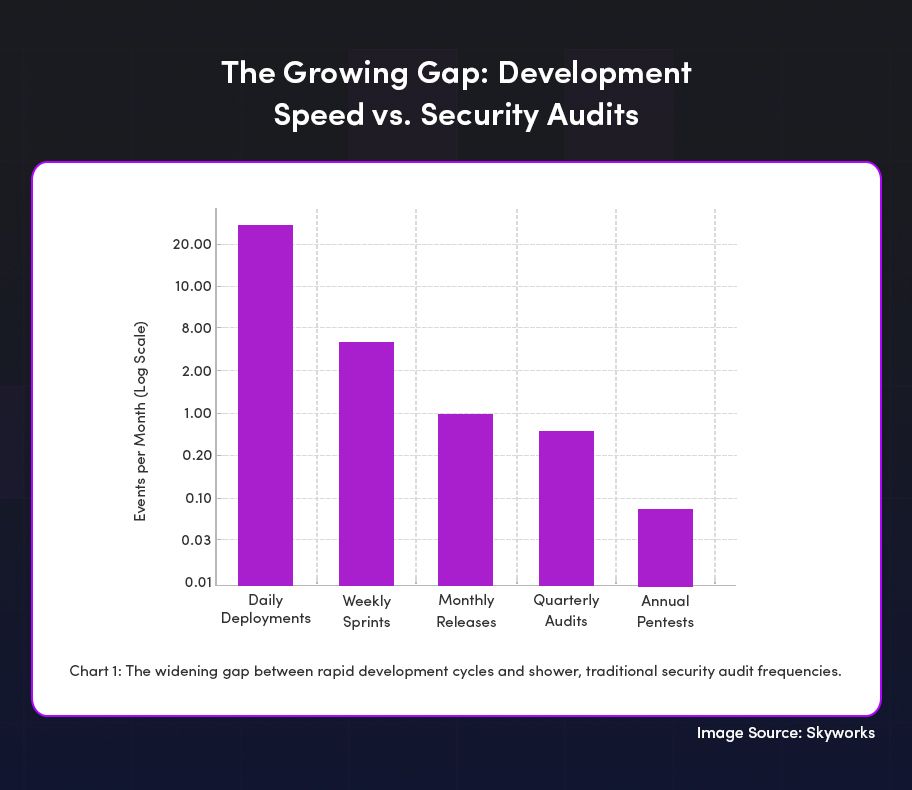
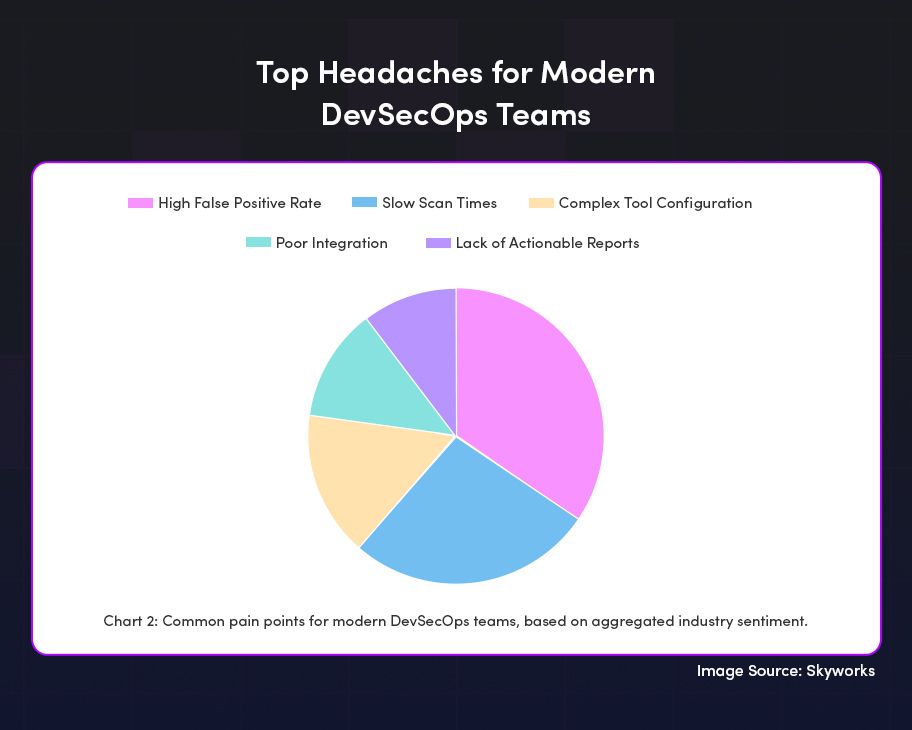
At its core, ZeroThreat is built to:
- Understand how an application behaves
- Detect weak points based on that behavior
- Run targeted exploitation
- Confirm vulnerabilities from 40,000+ database
- Provide AI-driven remediation reports
How ZeroThreat Approaches Pentesting
When you start scanning with ZeroThreat, it will:
- Map the application
- Identify input points
- Send controlled, context-aware requests
- Analyze every response in depth
- Continue testing based on observed behavior
This creates a feedback loop where the engine keeps learning as it progresses.
What “Zero” Philosophy Really Means for Setup and Trust
ZeroThreat is built on a Zero Trust architecture. This operates under the “never trust, always verify” principle, as defined by NIST. It means ZeroThreat’s solution security continuously verifies the security posture from an attacker’s perspective.
Secondly, ZeroThreat is designed around a simple idea: eliminate unnecessary complexity. Many AppSec tools require extensive configuration before scanning. They ask for rule tuning, path exclusions, framework-specific settings, and custom scripts.
ZeroThreat takes the opposite direction.
It works with minimal input:
- Target
- Credentials
- Environment context
This “zero friction” configuration helps teams start testing without operational load.
Zero Trust in Results
The “zero” part also reflects ZeroThreat’s approach to trust. It generates results only if they are validated. If something cannot be confirmed, it does not surface it as a finding. This means: near-zero false positives.
Security teams spend a significant amount of time filtering false positives. ZeroThreat tries to eliminate this stage by validating every issue.
Zero Dependency on Static Signatures
ZeroThreat doesn’t rely on:
- Static payload lists
- Rule packs
- Signatures tied to specific frameworks
Instead, it creates its own testing strategy from application behavior. This makes it better at handling:
- New frameworks
- Custom logic
- APIs with evolving schemas
- Authentication workflows
Its strength lies in adaptability rather than static knowledge.
Discover how automated pentesting delivers faster, deeper security insights. Try Automated Pentesting
How ZeroThreat Fills the Missing Layer in AppSec
Many organizations and developers use a mix of tools across different stages of the SDLC. Each tool solves a specific problem but also has limitations.
Here’s how ZeroThreat becomes a bridge in application security.
1) SAST (Static Application Security Testing)
SAST tools like Snyk or Veracode’s static engine analyze source code. They find:
- Insecure patterns
- Dependency vulnerabilities
- Configuration issues
These tools are useful for early detection, but they often:
- Produce many false positives
- Cannot validate impact
- Cannot understand runtime behavior
ZeroThreat doesn’t scan code. It focuses on runtime behavior and exploitability.
2) DAST (Dynamic Application Security Testing)
While comparing SAST with DAST, traditional DAST tools run passive and active checks. They:
- Crawl the app
- Test endpoints
- Run fixed payloads
Their limitations include:
- Limited logic testing
- Difficulty with stateful flows
- Weak support for role-based access issues
- Lack of deep validation
ZeroThreat approaches testing more like an analyst:
- Fewer requests
- More reasoning
- Validated proof
3) Manual Pentesting
Human pentesters remain essential. They find deep logic issues that automation can miss. But manual testing:
- Requires scheduling
- Is expensive
- Is not continuous
- Covers a small snapshot in time
ZeroThreat does not replace human pentesters. Instead, it:
- Automates repetitive tasks
- Finds consistent issues
- Helps maintain coverage between human-led assessments
4) Continuous Security
This is where ZeroThreat fits best.
Security experts and dev teams want constant visibility without constant manual work. They want findings that:
- Are real
- Come with proof
- Fit into their DevOps cycle
- Do not slow engineers down
ZeroThreat was built for this operational model.
The Intelligence Layer: What Powers ZeroThreat’s Automated Testing
ZeroThreat may lead with “simplicity,” but its real impact comes from the tech underneath. Here’s what we are going to talk about: ZeroThreat’s core capabilities.
1) Application Mapping and Enumeration
ZeroThreat builds a deep understanding of the application, much like a human tester would. Instead of blindly crawling everything, it prioritizes what matters for the attack flow.
It does this by:
- Crawling all reachable pages
- Detecting and categorizing input fields
- Enumerating parameters and request variations
- Identifying API endpoints and their use cases
- Tracking authentication states and session transitions
This targeted approach helps ZeroThreat focus on sections most likely to have real and critical vulnerabilities.
2) Behavioral Analysis
Once the structure is mapped, ZeroThreat starts observing how the application behaves. It watches for small but meaningful signals that reveal workflow logic and security controls.
It evaluates:
- Response codes under different conditions
- Timing patterns that hint at backend processing
- Error messages that expose internal behavior
- Redirects and state transitions
- Authentication or session changes
- Token issuance and usage patterns
- Multi-step workflow transitions
From these, it extracts deeper insights, such as:
- API semantics and expected behavior
- Session management rules
- Privilege boundaries for each role
This layer is crucial for catching logic flaws, areas where traditional scanners tend to fall short.
3) Payload-based Testing
Instead of firing thousands of payloads blindly, ZeroThreat forms small, intelligent payloads. Each payload is about how something might be exploitable.
Examples include:
- “This endpoint might support IDOR.”
- “This parameter might allow injection.”
It then sends targeted requests to prove or disprove the hypothesis.
This results in:
- Fewer overall requests
- Higher-quality results
- Minimal noise and false positives
It’s closer to how a human pentester reasons, not how a legacy scanner brute-forces.
4) Full Validation Before Reporting
Before anything reaches the report, ZeroThreat performs a complete validation cycle. Every confirmed finding includes:
- A clear, human-readable explanation
- Proof-of-impact backed by evidence
- Step-by-step reproduction details
- A list of affected parameters or components
- Actionable remediation guidance
ZeroThreat refuses to report an issue unless it has concrete proof.
This drastically reduces noise and helps engineering teams focus on real, verifiable problems.
Strengthen your web apps with continuous, AI-driven pentesting. Start Web App Pentest
The AI Engine: More Than Just a Scanner
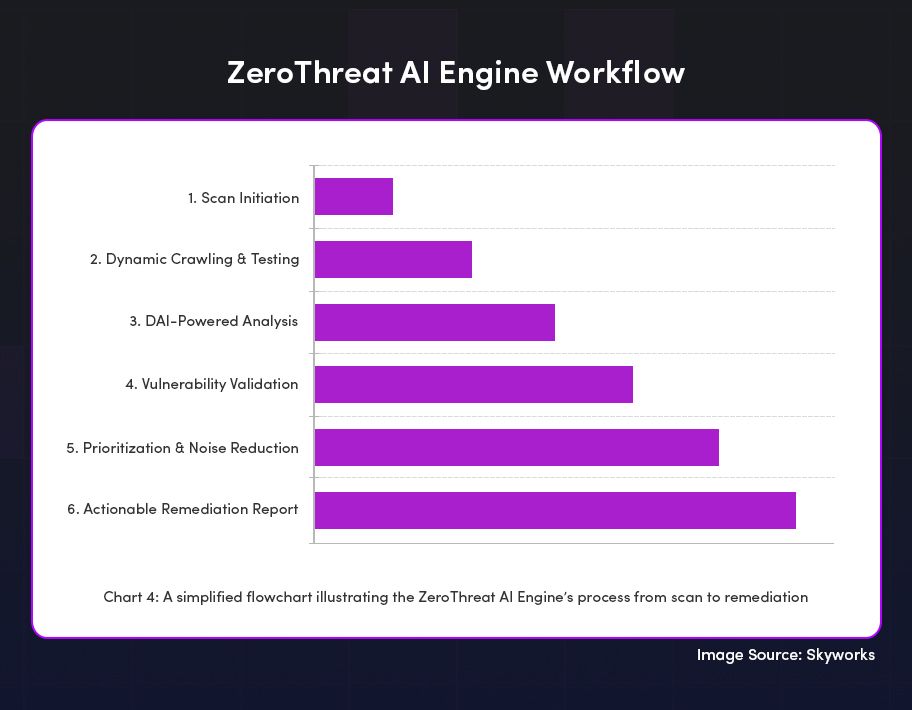
ZeroThreat doesn’t behave like a traditional vulnerability scanner. Because a scanner simply runs pre-set checks. On the other hand, ZeroThreat makes decisions. It observes the application, evaluates how it behaves, and adjusts its testing strategy in real time.
For example:
- If it detects unusual behavior, it immediately adapts its testing path.
- If a workflow shifts or behaves inconsistently, it re-evaluates and adjusts its approach.
Key Capabilities Behind This Behavior
ZeroThreat’s adaptive behavior comes from several capabilities:
- Context Retention: It remembers previous states, inputs, and responses, allowing it to perform multi-step tests.
- Multi-Step Reasoning: Instead of testing endpoints in isolation, it reasons across sequences, workflows, and dependencies.
- State Tracking: It monitors authentication, tokens, sessions, and role transitions continuously.
- Handling Incomplete Information: Like a human tester, it forms hypotheses even with partial or ambiguous data.
- Adaptive Testing: It modifies payloads, sequences, and assumptions based on how the application responds.
Therefore, this allows ZeroThreat to perform tests that go well beyond traditional scanning.
Why This Matters
Since ZeroThreat has various capabilities, it can uncover classes of vulnerabilities that other top DAST tools or traditional scanners often struggle with, such as:
- IDOR (Insecure Direct Object References)
- BOLA (Broken Object Level Authorization)
- Broken session or token management
- Faulty or missing access controls
- Sequence-dependent workflow vulnerabilities
These aren’t surface-level issues; they’re deep, contextual flaws that require an understanding of how the application behaves, not just how it responds to a single request.
Core Scanning and DevOps Integration
ZeroThreat is built for modern developers and security experts - the ones who deploy weekly, daily, or even multiple times a day. Traditional security tools often can’t keep up with this pace, but ZeroThreat is designed to fit directly into fast-moving development cycles.
- It can run scans at every key stage of the delivery pipeline:
- On every pull request to catch issues before code is merged
- On feature branches so developers get feedback early
- During deployment to validate newly released functionality
- After deployment to continuously check production behavior
- On a fixed schedule for routine assurance and compliance
This flexibility ensures that the security process never becomes a bottleneck.
Integration Philosophy
ZeroThreat takes a straightforward approach to integration. This leads to reduced friction.
It focuses on:
- Minimal configuration so teams spend less time on setup
- Clear inputs that tell the tool exactly what to test
- Predictable behavior that avoids surprises in CI pipelines
- Consistent outputs that can plug into any workflow
This matters because many web app security testing tools often-become operational overhead when they require heavy tuning or frequent adjustments. ZeroThreat avoids that trap.
How to Integrate ZeroThreat’s Pentesting into CI/CD Pipelines
A Walkthrough with GitHub Actions
Let’s integrate ZeroThreat into your CI/CD pipeline using GitHub Actions to automate security scans into your pipelines with github Actions.
Prerequisites
Before you begin, ensure the following:
- Your target application is verified on ZeroThreat.
- You’re familiar with the basics of GitHub Actions.
- Your GitHub repository has workflows enabled.
Step 1: Enable GitHub Actions Integration in ZeroThreat
Once confirmed, a unique ZT_Token will be generated. This token is used to start scans CI/CD for its associated target from the Ci/CD.
Step 2: Choose Scan Settings
Step 3: Setup GitHub Actions Workflow
- Open your target's GitHub repository.
- Navigate to the Actions tab.
- Click "New Workflow" and select "Simple Workflow" as your starting template.
- Name your workflow file (e.g., .github/workflows/scan.yml).
Step 4: Configure the Workflow File
name: ZeroThreat Vulnerability Scan Action
on: workflow_dispatch:
permissions: contents: read issues: write pull-requests: write
jobs: scan: runs-on: ubuntu-latest
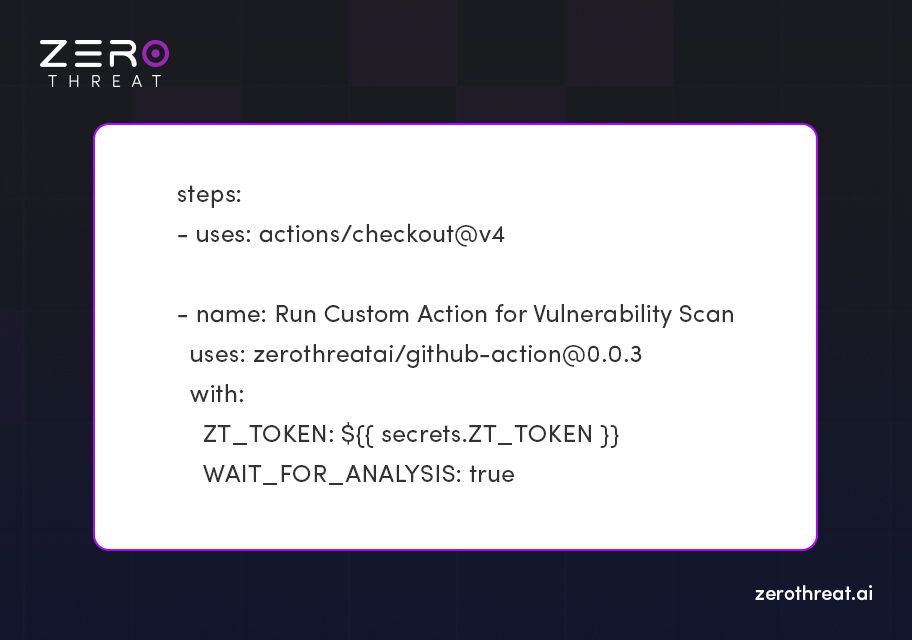
Step 5: Add ZT_TOKEN as GitHub Secret (optional)
It is recommended and advised to use the ZT_TOKEN as Github Secret and avoid hardcoding or exposing it.
Step 6: Run the workflow
Since this example uses workflow_dispatch, you can manually start a scan.
The workflow will begin and a scan will be triggered in ZeroThreat portal.
Automating with Push or Pull Requests
To automate scans on every code change, you can replace the on: block in the workflow with:
on:
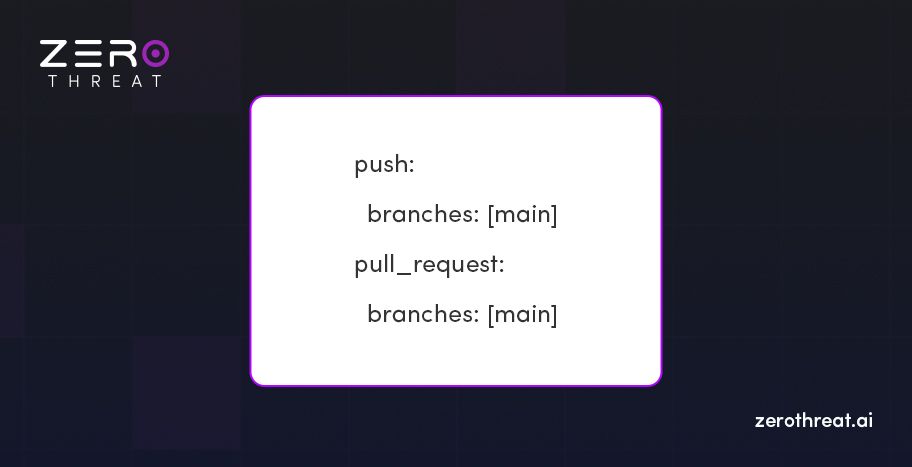
This will trigger ZeroThreat scans automatically for pushes or pull requests to the main branch.
How This Helps Developers
- Issues are flagged before merging
- Validated findings reduce guesswork
- Devs receive clear proof and remediation
How This Helps Security
- Continuous visibility
- Consistent baseline testing
- No need to manually request scans
- Integrated reporting
How This Helps Leadership
- Reduced risk exposure
- Predictable testing coverage
- Traceability for audit and compliance
Validate your API security with automated, exploit-level testing. Run API Pentest
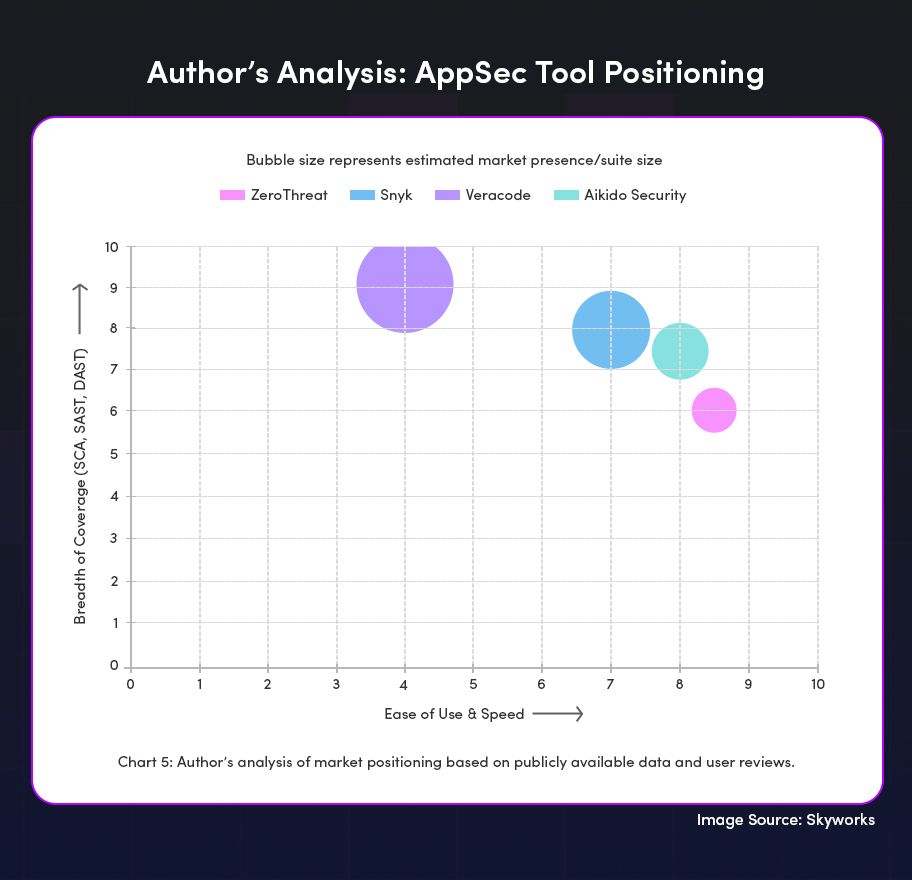
The Competitive Landscape: ZeroThreat vs Snyk, Veracode & Aikido
In this section, we are going to talk about ZeroThreat’s position against common penetration testing tools available in the market as per Skywork article.
The goal is not to promote or criticize any tool, but to understand where ZeroThreat fits.
1) Snyk
Snyk primarily focuses on multiple layers of the SDLC, including:
- Dependency scanning for vulnerable libraries
- Container scanning to identify image-level risks
- Infrastructure-as-Code checks for misconfigurations
- Code analysis to detect insecure patterns early
Strengths
- Broad coverage across the SDLC
- Strong ecosystem integrations
Limitations
- Limited ability to test runtime logic
- Doesn’t validate whether a vulnerability is actually exploitable in real workflows
2) Veracode
Veracode is widely used for:
- Static analysis (SAST) at scale
- Enterprise-wide scanning across large application portfolios
- Governance, policy enforcement, and reporting
Strengths
- Mature static analysis engine
- Proven enterprise governance capabilities
Limitations
- Dynamic testing relies on predefined test suites and structured patterns
- Less adaptive when evaluating real, changing application logic
3) Aikido
Aikido takes a modern approach to automated security testing, offering:
- DAST for dynamic risk detection
- Scanning across apps and APIs
- Limited logic checks to identify surface-level behavioral issues
Strengths
- Simple setup
- Modern UX and streamlined reporting
Limitations
- Logic testing depth is still limited
- Exploit simulations are relatively basic
| Aspect | ZeroThreat | Snyk | Veracode | Aikido Security |
|---|---|---|---|---|
| Primary Focus | AI-Powered DAST & Automated Pentesting | SCA & Developer-First Security | Enterprise AppSec Suite (SAST, DAST, SCA) | All-in-One, Low-Noise Security Platform |
| Ease of Setup | Very High (Zero Config) | High (Dev-friendly) | Low (Complex) | High (Easy Setup) |
| False Positive Rate | Very Low (Claimed near-zero) | Medium (User-reported noise) | Low-Medium (Tuned for enterprise) | Low (AI-filtered) |
| Ideal User | Startups, SaaS, DevOps Teams | Developers, Teams focused on Open Source | Large Enterprises, Regulated Industries | Startups, SMBs, Teams wanting consolidation |
Future of AppSec: ZeroThreat’s Role in an AI-Driven World
Application security is undergoing a major transformation. As systems or applications grow more dynamic and interconnected, static and pattern-matching tools are no longer enough to keep pace.
Modern applications increasingly rely on:
- Dynamic workflows that change based on user actions and business logic
- Multi-role logic, where permissions and outcomes vary by identity, context, and state
- Complex API sequences that must be executed in the correct order to reveal vulnerabilities
- Session-based states, making many security issues dependent on prior steps, tokens, or transitions
These evolving patterns introduce security gaps that traditional scanners were never designed to detect. As a result, the future of AppSec depends on systems that can interpret, reason, and experiment within an application rather than simply scan it.
AI-powered tools like ZeroThreat are better suited for this new landscape because they excel at:
- Adaptive decision-making based on responses
- Chaining actions to reach deeper vulnerabilities
- Contextual understanding of workflows, roles, and data paths
- Chaining request flows to probe complex state transitions
- Exploring unknown or hidden behaviors beyond predefined test cases
ZeroThreat’s architecture was intentionally built around these principles, positioning it as one of the first platforms engineered for the next era of AppSec.
Need help choosing the right AppSec approach? Talk to us. Talk to an Expert
What the Next Generation of Pentesting Will Look Like
The future of application security testing is rapidly shifting toward intelligence, continuity, and real-world validation. Next-generation tools will prioritize:
- Reasoning instead of payload spraying: AI agents will analyze the application and test intent-driven exploit paths rather than blasting static payloads.
- Continuous testing rather than periodic snapshots: Security validation will happen with every build, deploy, or workflow change, not once a quarter or before a release.
- A deeper understanding of user roles: Multi-role analysis will become baseline; tools will test as admins, normal users, attackers, misconfigured roles, and anonymous sessions.
- A focus on exploitability instead of theoretical findings: The emphasis will shift to validated, reproducible exploit chains instead of long lists of potential issues.
- Seamless integration into developer workflows: Results will appear directly in pipelines and issue trackers, enabling fixes before code ever hits production.
- Automated verification of fixes: Tools will rerun exploit paths automatically to confirm whether a patch truly resolves the vulnerability.
ZeroThreat is already operating within this future model. Its intelligent engine and AI-driven approach to AppSec make it one of the first practical implementations of reasoning-based security testing. It bridges today’s needs with tomorrow’s expectations, bringing modern, context-aware security validation to teams right now.
Final Thoughts
ZeroThreat represents a different model of automated testing. It aims for accuracy, not volume. It focuses on behavior, not patterns. It integrates with development, not as an afterthought but as part of the workflow.
In a nutshell, ZeroThreat is
- For security engineers, it reduces repetitive testing.
- For developers, it provides clear, validated issues.
- For leaders, it offers steady visibility and reduced risk.
ZeroThreat is not a replacement for human expertise.
It is a reliable system that handles the kind of testing that needs to happen every day, but is too time-consuming to do manually.
So, sign up today for FREE and experience continuous pentesting with ZeroThreat now.
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


