All Blogs
Zerothreat: The Missing Layer Between Dast and Human Pentesting

Quick Overview: A new feature goes live in apps. Everything looks perfect, until a hidden flaw slips through and exposes data. It’s a familiar story in fast-moving development. Traditional DAST misses it, and manual pentests come too late. That’s why ZeroThreat exists to bridge that gap. Let’s talk about automated pentesting – a missing layer between DAST and human pentesting.
Everyone in the software world knows that speed rules. Apps ship fast. APIs change daily. Yet security often falls behind. Traditional security testing can’t keep pace. On one side, you have automated pentesting and scanning tools. On the other side, you have expert human pentesters. Both have strengths. But both have gaps. That’s where ZeroThreat comes in.
ZeroThreat is the missing layer between next-gen dynamic application security testing (DAST) and full-scale human penetration testing. It blends automation, intelligence, and developer-friendly workflows.
In this article, we’ll explore what that means. We’ll dig into how ZeroThreat works, why it matters, and what business benefits it brings.
Join the next generation of AI-powered security validation. Sign Up for FREE
On This Page
- Challenges with Today’s Testing Methods
- What ZeroThreat as a Pentesting Tool Does
- Why ZeroThreat Fits as a Missing Layer
- How ZeroThreat Works
- Business Advantages of Using ZeroThreat
- Primary Use Cases
- Limitations and Considerations
- Start Scanning in Simple Steps
- Final Thoughts
Challenges with Today’s Testing Methods
1. DAST (Dynamic Application Security Testing)
DAST tools scan running applications. They simulate attacks from “outside-in”. They can find many common flaws: SQL injection, cross-site scripting (XSS), and misconfigurations.
For example, ZeroThreat describes DAST as a black-box testing method.
But limitations remain. Some of the drawbacks:
- They often require heavy configuration.
- They struggle with complex logic flaws or business-workflow vulnerabilities.
- False positives and noise can hamper remediation efforts.
- They may not integrate smoothly into fast CI/CD workflows.
2. Human Penetration Testing
Penetration testers bring expertise. They explore business logic, chained exploits, design flaws. They can find what automated tools miss.
Yet:
- They are slow and expensive.
- They are episodic (often once per release or per quarter).
- They don’t always fit into modern, continuously-delivered software development cycles.
- Because they take time, vulnerabilities may dwell in production longer.
3. The Gap
So, we have a gap. On one side automation (fast but limited). On the other side manual (deep but slow).
What’s needed is a layer that sits in between — fast, automated, developer-friendly — yet deep enough to catch more than classic DAST. That layer is what ZeroThreat claims to provide.
What ZeroThreat as a Pentesting Tool Does: Bridging the Gap
ZeroThreat is an automated pentesting and DAST platform for web applications and APIs. Let’s break down its capabilities to understand more.

Automated Pentesting + DAST
ZeroThreat doesn’t just run automated scans. It combines dynamic scanning with simulated attack techniques akin to pentesting. In fact, it detects over 40,000 vulnerabilities, including those from the OWASP Top 10 and CWE Top 25, such as sensitive data exposure, XSS, CSRF, and session hijacking.
ZeroThreat tool is designed to go beyond typical DAST by uncovering logic flaws, business workflow vulnerabilities, and API weaknesses.
Zero Configuration/Built for Developer
A primary functionality that ZeroThreat stands out for is No Setup Required. It is known for “zero configuration required” and “no expertise needed”. That means development teams with less security expertise can adopt it. This enables you to integrate pentesting into the development cycle more quickly.
API and Web App Coverage
Modern applications are API-rich, microservice-based, and single-page applications (SPAs). ZeroThreat covers web apps and APIs (REST, GraphQL, SOAP) and supports authenticated scanning, multi-factor authentication, and more.
Continuous, Developer-First Integration
Since scanning is faster and automated, ZeroThreat’s pentesting tool supports a “shift-left” security approach. It integrates into CI/CD pipelines, providing results immediately rather than waiting for a dedicated penetration testing phase.
Evidence-Driven and Actionable Reports
ZeroThreat emphasizes actionable, remediation-ready reports. It prioritizes vulnerabilities based on exploitability and business context. This reduces noise.
See how much time and cost you can save with ZeroThreat’s autonomous validation engine. Calculate Your ROI
Why ZeroThreat Fits as a Missing Layer
Calling ZeroThreat the “missing layer” is apt because:
- It bridges the gap between pure automation (typical DAST) and full manual pentest.
- It adds depth above simple scanning: logic flaws, API issues, complex workflows.
- It adds speed and scalability above manual pentesting: continuous, automated, integrated.
- It helps cover the gap where development pace outstrips security throughput.
Let’s consider it in a simple way:
- DAST finds many defects but may miss business logic or API chain exploits.
- Manual pentesting finds deep flaws but can’t scale for frequent releases.
- ZeroThreat offers a hybrid: automated DAST but deeper and more developer-friendly than typical vulnerability scanners.
How ZeroThreat Works
Let’s examine some of the technical mechanics.
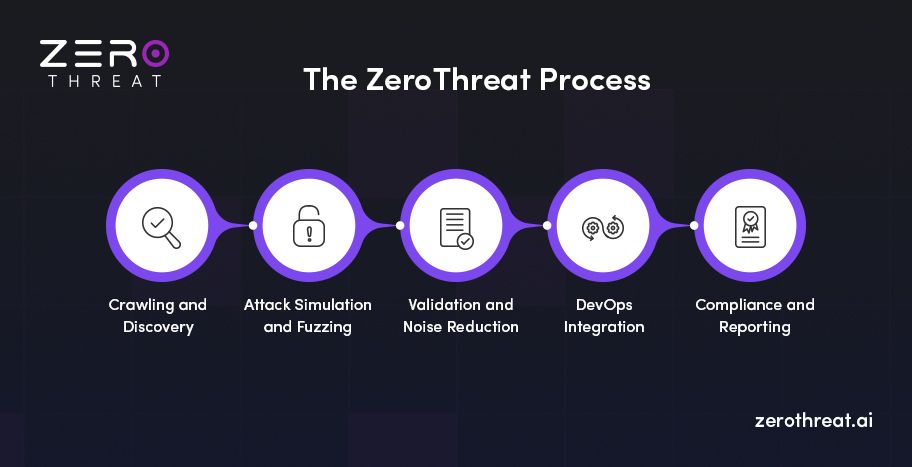
Crawling and Discovery
First step of this penetration testing tool is to identify the attack surface. For web apps and APIs, this means mapping endpoints, sessions, authentication paths, JavaScript front ends. The platform uses an intelligent crawler capable of handling SPAs and heavy client-side apps.
Attack Simulation and Fuzzing
Once discovered, the tool simulates over 40,000 attacks: injections, logic faults, API parameter abuses, data flow anomalies. Automated fuzzing and anomaly detection help catch zero-day-style flaws or unusual flows.
Validation and Noise Reduction
ZeroThreat emphasizes “near zero false positives” and 98.9% accurate vulnerability detection. That leads to fewer wasted remediation cycles. Additionally, validation ensures that findings are actionable and realistic.
DevOps Integration
Scans can be easily integrated into CI/CD workflows. The platform offers project management tool integrations with Jira, Slack, GitHub, and more. That means security becomes part of the build/release pipeline rather than a gate at the end.
Compliance and Reporting
Beyond vulnerability detection, the platform offers audit-ready reporting aligned with standards - PCI-DSS, HIPAA, GDPR, ISO, and shows business risk metrics.
Business Advantages of Using ZeroThreat
Here are the major business benefits of using ZeroThreat for your organization:
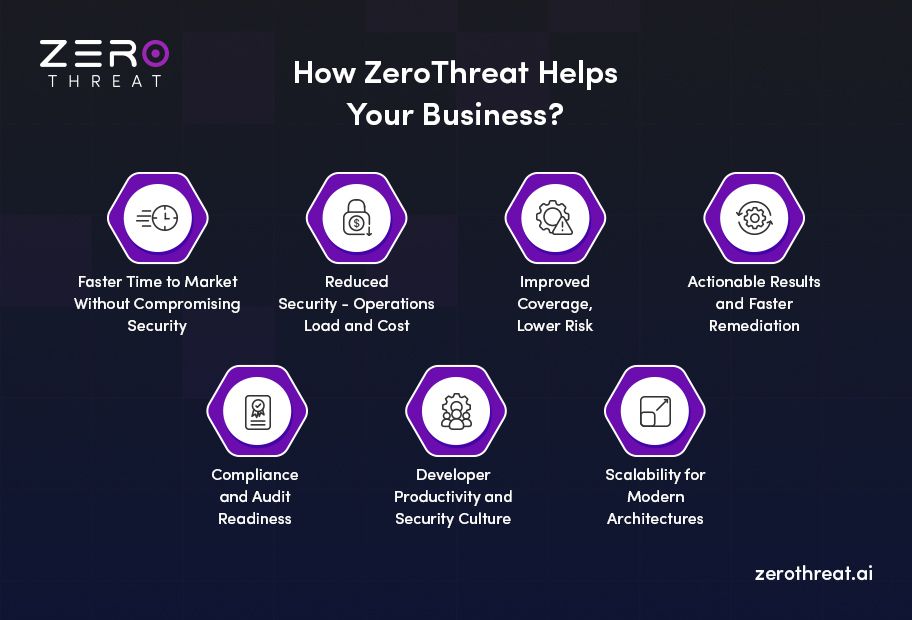
Faster Time to Market without Compromising Security
Developers can shift features faster because the security layer is automated and integrated. With ZeroThreat, you can start scanning your web applications in under 10 minutes and receive a remediation report quickly, within 0.5–2 hours. This helps developers spend less time waiting for security sign-off and more time building features.
Reduced Security-Operations Load and Cost
Traditional pentesting consumes significant budget and resource time. Whereas ZeroThreat reduces the manual pentesting effort by up to 90%. That means fewer dedicated hours, fewer expensive external consults, fewer bottlenecks.
Improved Coverage, Lower Risk
Since scanning is continuous and automated, hidden vulnerabilities, especially in APIs, logic flows, and microservices, get caught more frequently. That improves the overall security posture, reduces the risk of data breaches, and provides better assurance to stakeholders.
Actionable Results and Faster Remediation
High-quality findings with low false positives mean remediation teams spend less time investigating noise. Prioritisation based on business context ensures real threats get addressed first. That reduces mean time to remediation (MTTR).
Compliance and Audit Readiness
Automated reporting aligned with compliance standards means security teams are better prepared for audits. It also builds trust with management, regulators, and customers.
Developer Productivity and Security Culture
When security tools are developer-friendly, there’s very few chances of friction. Developers adopt them, feedback loops improve, and security becomes part of the culture rather than a gate. That helps mature the application security posture.
Scalability for Modern Architectures
As organizations adopt microservices, frontend SPAs, APIs, and cloud-native stacks, older security tools can’t keep up and often struggle. ZeroThreat is built for modern architecture. This means you can easily scan modern APIs, AI-native applications, microservices, GraphQL, SPAs, and JavaScript-heavy web apps. So, you can scale your business along with security solutions.
Discover how AI-driven pentesting is redefining security validation. Explore Automated Pentesting
Primary Use Cases
Here are some realistic scenarios where ZeroThreat adds value:
- A SaaS startup launching new features biweekly. Therefore, they would need continuous pentesting integrated into the CI/CD pipeline. We all know that manual pentesting per release is too slow. Here, ZeroThreat allows continuous pentesting at each release, helping you identify business logic flaws and other critical threats early and quickly.
- A mid-sized enterprise with many web apps and APIs. They lack deep security resource coverage. They adopt ZeroThreat to continuously scan all exposures, reduce dependency on external pentesters, and focus internal resources on complex threats.
- A regulated business (financial services, healthcare) needing compliance, audit-ready reports, and proof of security. ZeroThreat provides automated compliance-aligned reports and pipeline-integrated scanning, reducing audit risk.
Limitations and Considerations
We all know that no vulnerability scanner or DAST tool is perfect. Here are some limitations that you have to consider:
- Even the best automated tool cannot replace expert human pentesters entirely. Some logic flaws, chained exploits, and insider attack vectors still require human expertise.
- Integration and culture matter. Scanning alone doesn’t fix vulnerabilities; teams must act on findings, track remediation, and improve over time.
- Cost vs benefit: While automation reduces cost compared to traditional pentesting, organizations must still invest in training, processes, and possibly hire security engineers to act on the results.
Start Scanning with ZeroThreat in Simple Steps
If you are planning to fill this “missing layer” of security into your SDLC, here’s a roadmap you need to follow:
Define Baseline
- Inventory web apps, APIs, and microservices.
- Determine critical business workflows and high-exposure endpoints.
Integrate ZeroThreat
- Choose ZeroThreat as your automated continuous pentesting tool.
- Integrate into your CI/CD pipeline: build → test → scan → report → fix.
- Set up authentication for scanning protected endpoints and APIs.
Tune and Run Regular Scans
- Configure scan schedules (nightly, per commit, per release).
- Monitor results: ensure the tool crawls the full surface, handles sessions, and SPAs.
Investigate and Remediate
- Use prioritized reports to assign remediation tasks.
- Track mean-time-to-fix (MTTR), number of vulnerabilities closed, etc.
- Feed insights back into dev teams (secure coding, logic review).
Combine with Human Review
- Periodically schedule full manual pentests for high-risk areas.
- Use automated tool findings to guide manual efforts (triage, validate, explore deep logic attacks).
Govern and Improve
- Use metrics: scan coverage, vulnerabilities found vs fixed, time to fix, etc.
- Report to leadership: reduced risk, faster delivery, compliance-status.
- Improve over time: code reviews, security training, and more sophisticated logic-flaw detection.
Get a live session with our security experts — no sales fluff, just insights. Book a Demo Call
Final Thoughts
In a world where development moves fast and attack surfaces grow constantly, organizations cannot rely solely on traditional DAST or periodic human pentesting. They need the “missing layer” - a continuous, automated, developer-friendly security posture that bridges these gaps.
ZeroThreat offers that layer: combining DAST, automated pentesting, modern architecture support (APIs, SPAs), and developer-friendly workflows.
If your organization is facing pressure to deliver features quickly while staying secure, this missing layer may be what you need. Adopting an automated pen testing tool like ZeroThreat doesn’t mean ignoring manual pentesting or static testing. Rather, it means complementing them, using automation to handle the repetitive and broad tasks, while reserving expert human time for deep, sophisticated, business-logic threats.
Security is no longer a gate at the end of the line. With the right missing layer in place, it becomes a continuous part of delivery - faster, smarter, and more aligned with the business.
Frequently Asked Questions
What gap does ZeroThreat fill between DAST and manual pentesting?
ZeroThreat bridges automation and expertise by offering deeper, smarter scans than DAST and faster, continuous coverage than manual pentests. It detects logic flaws, validates results, and integrates seamlessly into development cycles for real-time, actionable security insights.
Can ZeroThreat replace a human penetration test?
How does ZeroThreat reduce false positives?
Does ZeroThreat integrate with CI/CD and developer workflows?
Will ZeroThreat help with audit readiness (HIPAA/PCI/ISO)?
Is ZeroThreat suitable for APIs and modern SPAs?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.


