All Blogs
Laravel SQL Injection: Risks, Best Code Practices, and How to Prevent It

Quick Summary: SQL injection attacks are a prevalent issue if we talk about the matter of Laravel security. If left unchecked, they can significantly affect the workflow of an entire web application. This blog outlines typical examples of SQL injection attacks and essential security measures to effectively combat them. Give this blog a thorough read to minimize the risk of SQL injection attacks by learning from common examples.
As a developer, it's your duty to build powerful and secure applications for your end users. However, it's your responsibility to ensure that your app data remains secure and safe. In fact, all data that has been utilized in your app is stored in SQL Server. To secure and protect your SQL Server, you must follow the best security practices.
Here, SQL injection remains one of the most critical vulnerabilities, allowing attackers to manipulate databases and access sensitive information. That's why developers who build applications using PHP's Laravel framework must understand the risks of SQL injection and implement best practices in order to prevent SQL injection vulnerability.
According to BuiltWith, Laravel stands out as one of PHP's most popular frameworks, with over 2.5 million live websites using it.
However, it's important to consider that Laravel can be optimized to the core but can also be exploited. SQL injection is an old and very common security issue in Laravel.
In this blog post, we will explain what is SQL injection in Laravel and how to prevent it. Also, we will go through some examples of Laravel SQL injection, along with steadfast practices on how to prevent other potential PHP vulnerabilities. Let's begin with it.
Unlock The Power of an Advanced Vulnerability Scanning Tool to Lock the Door for All Potential Vulnerabilities Give it a 'GO'
On This Page- What is a Laravel SQL Injection Attack?
- Common Types of Laravel SQL Injection Attacks
- Laravel Anti-Patterns That Lead to SQLi
- How to Prevent SQL Injection in Laravel
- How ZeroThreat Can Help You Prevent SQL Injection in Laravel
- What is a Laravel SQL Injection Attack?
- Common Types of Laravel SQL Injection Attacks
- Laravel Anti-Patterns That Lead to SQLi
- How to Prevent SQL Injection in Laravel
- How ZeroThreat Can Help You Prevent SQL Injection in Laravel
What is a Laravel SQL Injection Attack?
SQL injection in Laravel is a type of cyber attack when an attacker manipulates SQL queries by injecting malicious data into a Laravel application's database interactions. This allows attackers to retrieve data, modify database entries, and even execute administrative operations.
Let's look at some of the SQL injection attacks that affect major organizations.
In 2011, Sony's network was affected by a severe SQL injection vulnerability, which compromised their digital infrastructure. In fact, around 77 million PlayStation Network accounts were affected, costing Sony an estimated $170 million.
In the same way, in 2023, Microsoft SQL Servers were affected by SQL injection, which led to breach cloud environments. In fact, this lateral movement technique has been seen in attacks on servers like VMs and Kubernetes clusters.
Let's learn how Laravel SQL injection attacks occur:
1. Usage of Raw SQL Queries
Embedding user input into SQL queries directly without detailed sanitization, validation, and parameter binding.
Let's take an example of the vulnerable code:
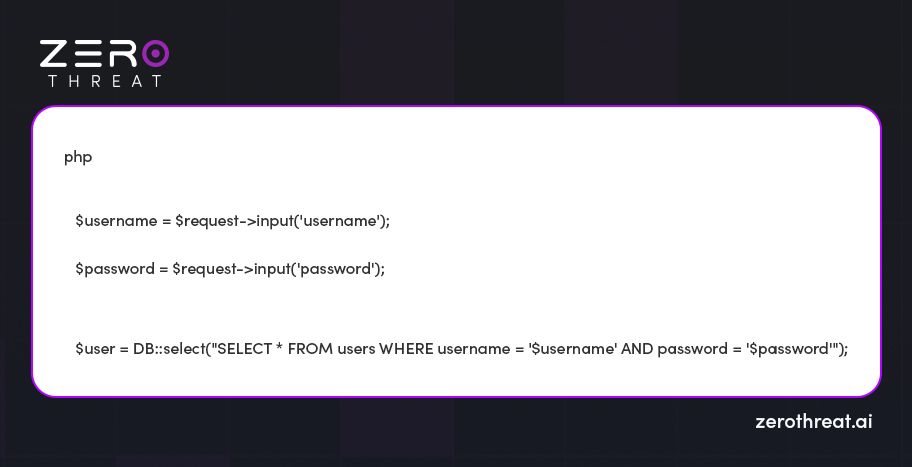
In this example, if an attacker aims to provide malicious input like 'OR 1=1 --, the results will appear something like this:
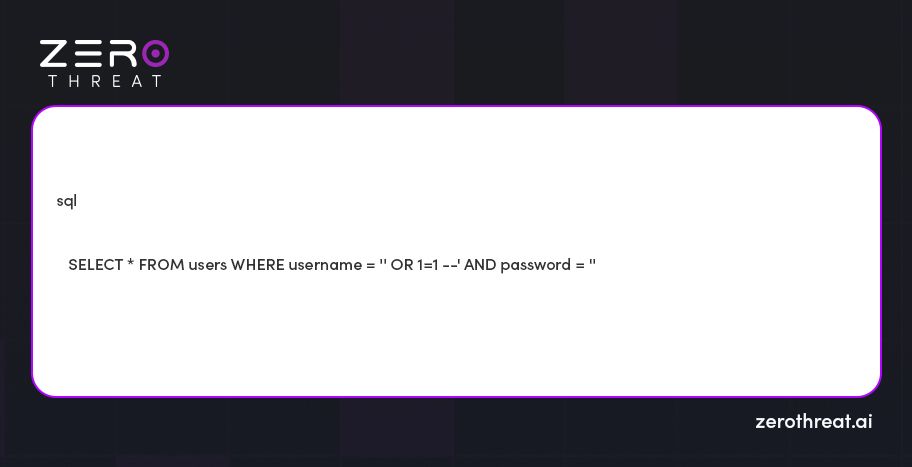
This can allow the malicious input to go for direct user input without a proper authentication check and return all users from the users table.
2. Insufficient Input Validation
Failing to conduct proper validation and sanitization of user inputs before embedding them into database queries.
Let's take an example of the vulnerable code:
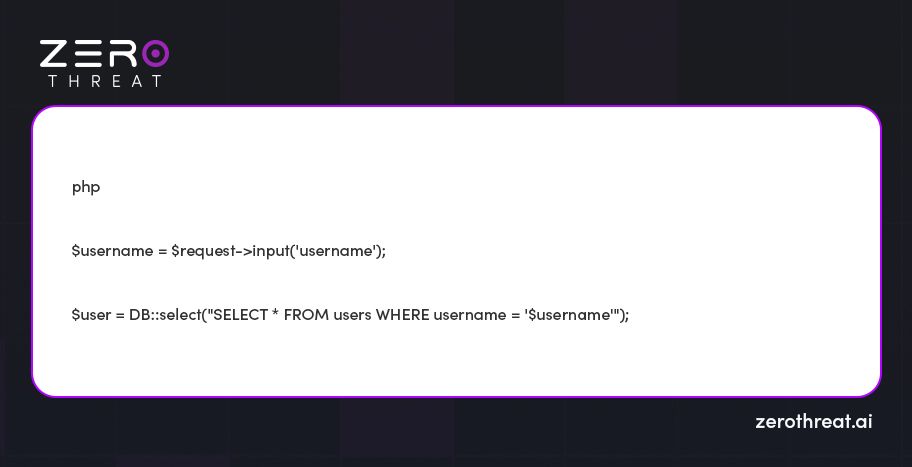
If $username carries a malicious input like ' OR 1=1 --, it would lead to a SQL injection vulnerability.
Common Types of Laravel SQL Injection Attacks
Let's learn in detail about the common types of SQL injections in Laravel in order to enforce defensive security measures properly.
1. Basic SQL Injection
In Laravel, developers might write SQL queries to fetch data from the database. If these queries concatenate user input directly into the SQL statement, avoiding sanitization, it can increase the likelihood of SQL injection vulnerabilities in the database.
Here's an example:
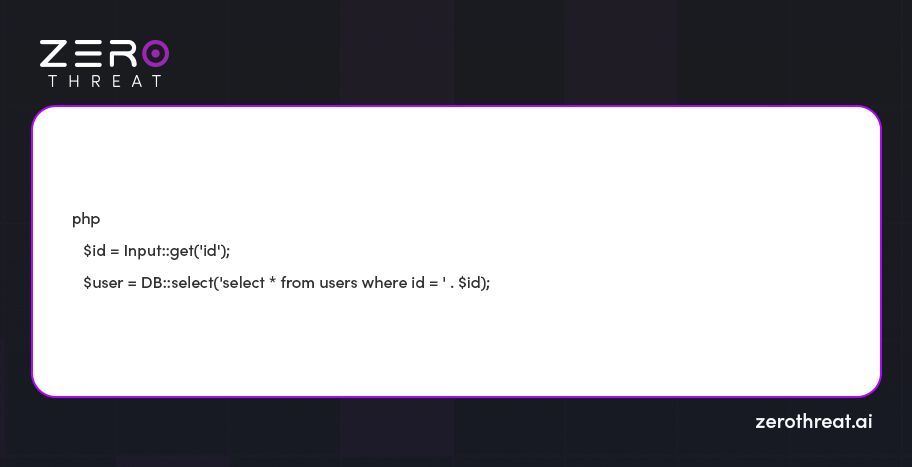
If an attacker provides id as 1; DROP TABLE users;, the manipulated SQL query looks something like this:
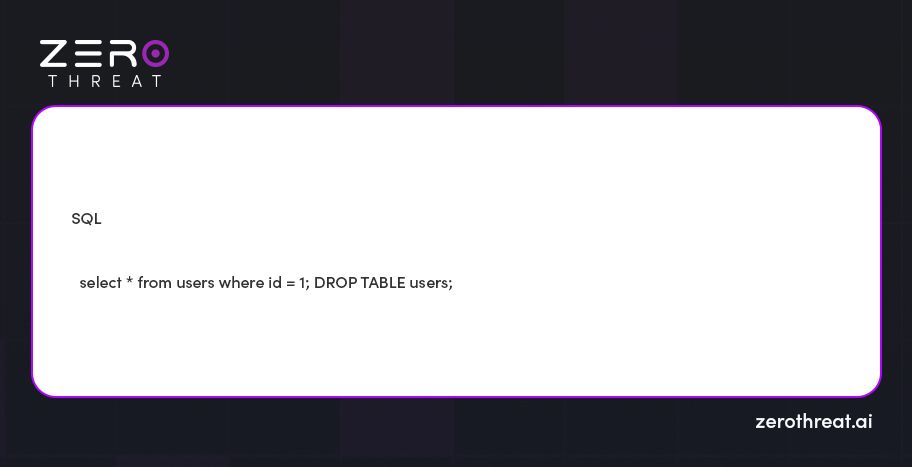
This would represent two SQL commands instead of one, which can lead to huge data loss.
2. Eloquent ORM Injection
Laravel's Eloquent ORM is created to safeguard SQL injection with the help of parameter binding and query building techniques. However, its misuse by using input directly without proper validation can create room for vulnerabilities.
Let's take an example:
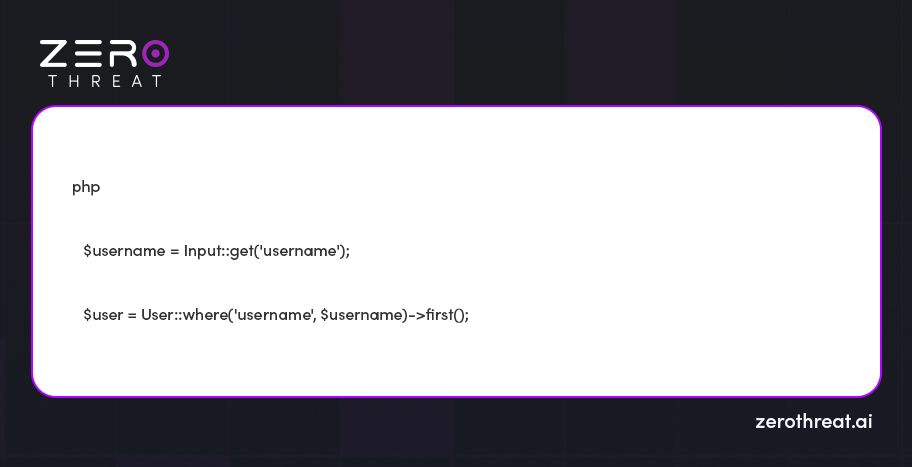
If 'username' is manipulated to encompass SQL commands, such as admin' OR 1=1 --, the query is likely to retrieve unintended information or might end up allowing unauthorized access.
3. Raw SQL Queries
Developers might use raw SQL queries for specific requirements. If these queries end up concatenating user input directly, avoiding using Laravel's parameter binding capabilities, the chances of vulnerabilities increase.
Let's take an example:
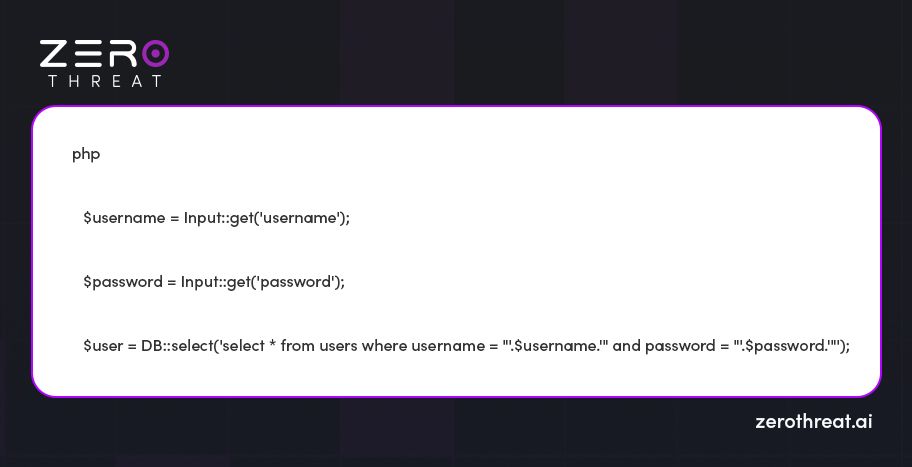
If username or password includes malicious SQL commands, such as admin'--, it could alter the intended logic of the query.
4. Blind SQL Injection
There are also chances of attackers attempting blind SQL injection attacks by examining application responses to crafted queries, even if direct manipulation of queries is not feasible because of Laravel's built-in protection. This involves the usage of techniques to infer data from the application's responses to their injected queries.
Laravel Anti-Patterns That Lead to SQLi
Laravel shields developers from many SQL injection pitfalls, but a few common anti-patterns still open the door. Spotting them early prevents exposure and saves response time.
Concatenating User Input into Raw SQL
Building queries by stitching user input into strings bypasses Laravel's protections. Attackers can inject payloads that change the intent of your query. Always prefer parameter binding or Eloquent methods that escape values for you.
Misusing whereRaw / orderByRaw Without Bindings
whereRaw and orderByRaw are powerful but risky when used with unbound values. Passing unvalidated input directly into these helpers produces the same effect as raw SQL concatenation. Use bindings or validate and whitelist any fields used in order clauses.
Unsafe Mass Assignment Leading to Query Manipulation
Mass assignment simplifies models but can expose queryable fields when combined with unfiltered input. Restrict fillable attributes and sanitize request data. Validate incoming payloads and avoid letting clients control fields that alter query logic.
How to Prevent SQL Injection in Laravel
For robust Laravel SQL injection protection, you have to follow the OWASP Cheatsheet, which helps you secure your Laravel application.
It comes with:
- Eloquent ORM SQL Injection Protection
- Raw query SQL injection
- Column Name SQL Injection
- Validation Rule SQL Injection
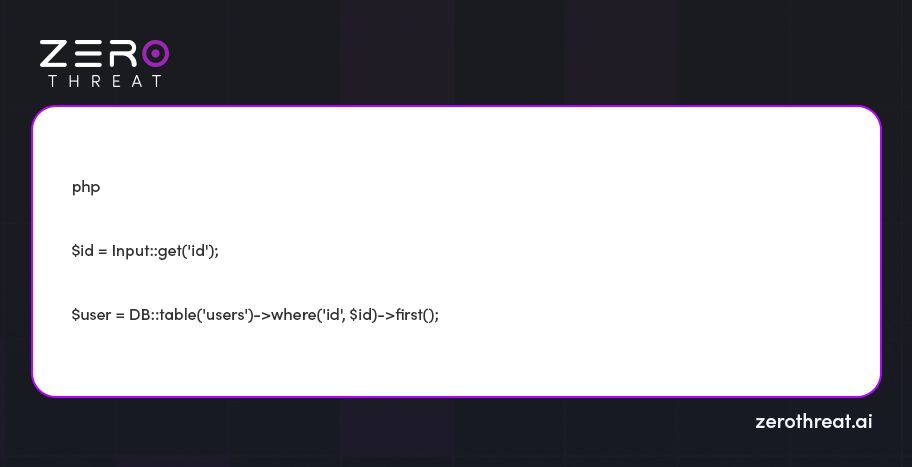
1. Parameter Binding with Query Builder
Laravel's query builder offers a simple and secure option for creating SQL queries. This ensures that more priority is given to using parameter binding instead of concatenating raw user inputs into SQL queries. Parameter binding automatically takes care of escaping user inputs, preventing SQL injection attacks.
Check out the example:
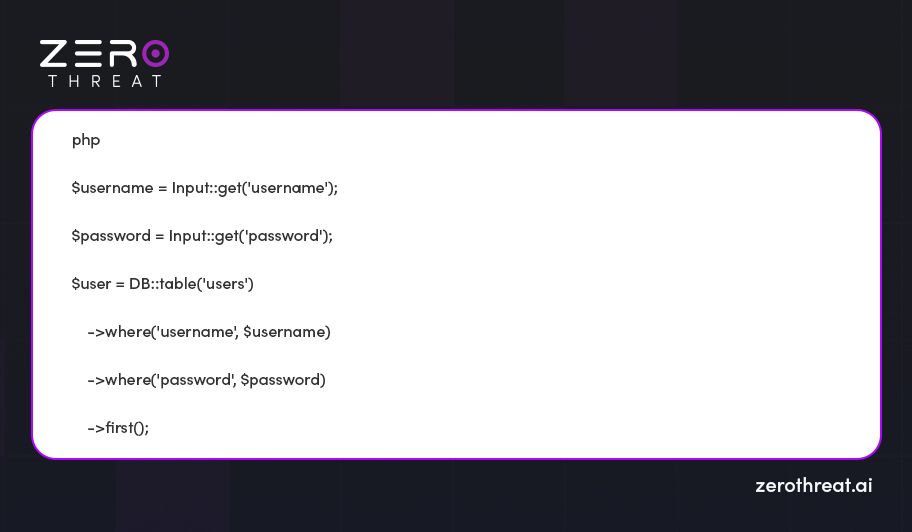
2. Eloquent ORM Usage
Eloquent ORM in Laravel safeguards your web apps against SQL injection attacks if used in a correct manner. Don't follow the practice of using raw inputs directly in Eloquent queries and entirely depend on Eloquent's query building abilities.
Check out the example:
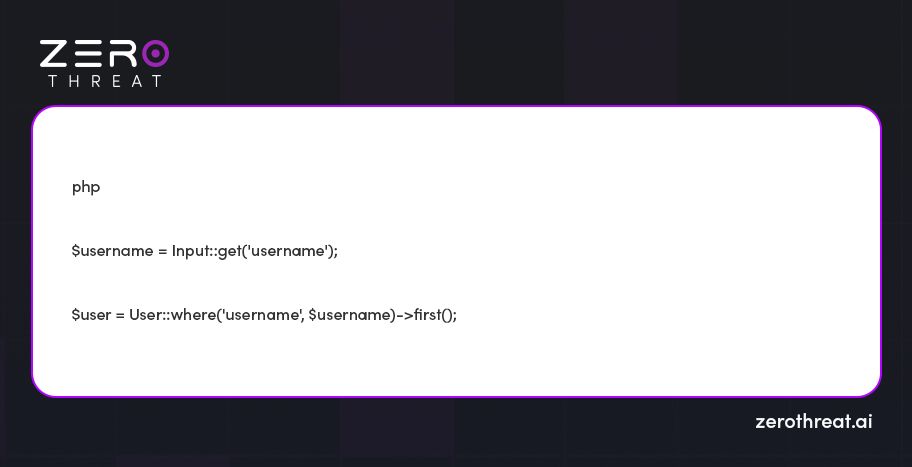
3. Input Validation and Sanitization
Always ensure that user inputs are validated and sanitized to verify if they adhere to the standard formats and types before embedding them directly into database queries. Laravel helps with a set of validation rules that can be deployed to incoming requests, which allows developers to ensure that inputs are safe and within acceptable bounds.
Check out the example:
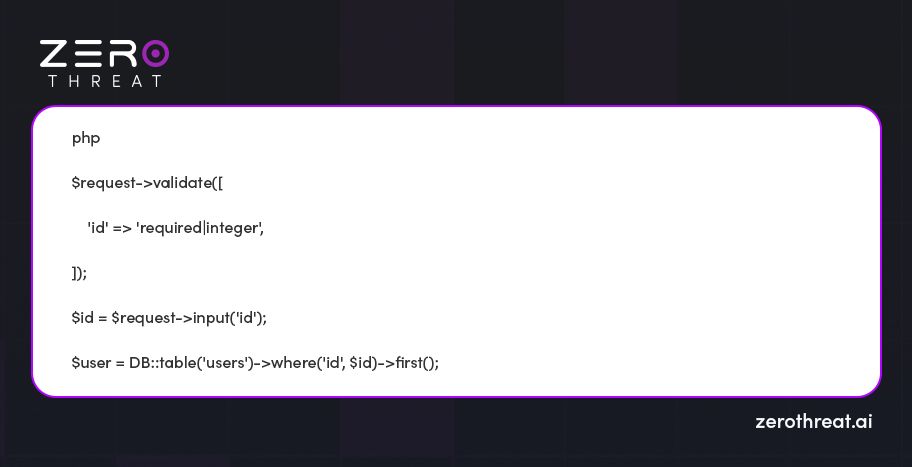
4. Avoid Usage of Raw SQL Queries
Don't follow the practice of using raw SQL queries as much as possible. Instead, optimize Laravel's query builder or Eloquent ORM methods that are created to provide security against SQL injection attacks with the help of parameter building.
Check out the example:
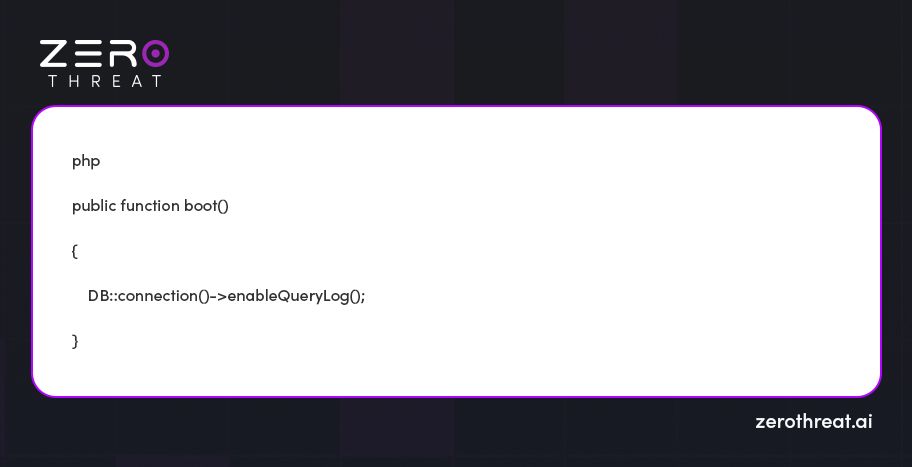
5. Leverage Laravel's Query Logging for Debugging
Enable query logging in your Laravel app while development to capture the actual SQL queries that are being executed. This allows developers to recognize unintended concatenation of user inputs into SQL statements.
In order to implement query logging, add the following to your AppServiceProvider:
6. Principle of Least Privilege
Always verify that database users and connections used by your Laravel application have the minimal permissions required to perform certain tasks related to their roles and responsibilities. This relatively decreases the risk of the potential impact of a successful SQL injection attack.
Don't let vulnerabilities put your data at risk. See how ZeroThreat can protect your Laravel apps. Ready to Contact Us
How ZeroThreat Can Help You Prevent SQL Injection in Laravel
Laravel has established itself as quite a popular framework of PHP, and it's prevalent amongst the developers' community for its versatility and advanced features. Therefore, it's essential to secure your Laravel apps against any vulnerabilities like SQL injection attacks.
While Laravel offers built-in protections like Eloquent ORM and Query Builder, ensuring complete security requires a proactive and comprehensive approach. ZeroThreat, an advanced vulnerability scanner, empowers developers to identify, prevent, and remediate SQL injection vulnerabilities effectively.
Its combination of automated penetration testing and DAST ensures that your app remains secure without sacrificing productivity. Ensure your application remains resilient against evolving threats with ZeroThreat. Sign up today and stay ahead of attackers.
Frequently Asked Questions
What are the risks of SQL injection?
Here are the potential risks of SQL injection attacks:
- Data Loss or Corruption
- Unauthorized Access
- Data Disclosure
- Execution of Arbitrary Commands
- Application Disruption
- Regulatory Compliance Violations
- Reputation Damage
Is the Laravel framework secure?
Which encryption is best for Laravel?
Which is the recently identified vulnerability in Laravel?
How to prevent SQL injection in Laravel?
Explore ZeroThreat
Automate security testing, save time, and avoid the pitfalls of manual work with ZeroThreat.



